好看
- Nov 2020
-
www.exam58.com www.exam58.com
-
这诗写的也太好了吧
青山一道同云雨,明月何曾是两乡
-
-
legacy.reactjs.org legacy.reactjs.org
-
via https://reactjs.org/docs/forms.html#alternatives-to-controlled-components
-
pass its state down as props to its child components
props down
-
This is why state is often called local or encapsulated
state is private to component that owns it
-
the props at the time the update is applied as the second argument:
相当于对应这个 state 时的 props?
-
While this.props is set up by React itself and this.state has a special meaning, you are free to add additional fields to the class manually if you need to store something that doesn’t participate in the data flow (like a timer ID).
this 里
- props
- state
这俩是特殊的
而其他的字段可以随意加?
-
When React sees an element representing a user-defined component, it passes JSX attributes and children to this component as a single object. We call this object “props”.
?
-
This function is a valid React component because it accepts a single “props” (which stands for properties) object argument with data and returns a React element
(properties) => react element
-
render a React element into a root DOM node
将一个 React Component 在一个 root DOM node 中渲染
-
{name}
variable
namein braces: {name} -
via https://reactjs.org/docs/getting-started.html#learn-react
as they called: learn concepts step by step
-
-
-
formik.org formik.orgFormik1
-
news.ycombinator.com news.ycombinator.com
-
make money?
-
-
www.scylladb.com www.scylladb.com
-
www.tetrate.io www.tetrate.io
-
www.cis.upenn.edu www.cis.upenn.edu
-
wonderful page showing
- {} braces
- [] brackets
- () parentheses
-
-
www.mmhmm.app www.mmhmm.app
-
seems interesting
-
-
github.com github.com
-
maybe a good reading material on k8s
-
-
github.com github.com
-
discussion on why deployment.spec.selector is immutable
Tags
Annotators
URL
-
-
github.com github.com
-
读了一遍收获不大,读懂的内容读之前已经懂的,不懂的看了还是不大懂,等日后再来吧
-
act before your cache has filled
什么叫(或者说怎么判断) : cache has filled?
-
You may see other mechanisms like reflectors and deltafifos driving controllers. Those were older mechanisms that we later used to build the SharedInformers. You should avoid using them in new controllers.
so
reflectorsandDeltaFIFOsare used to build theSharedInformersas this pic showed:
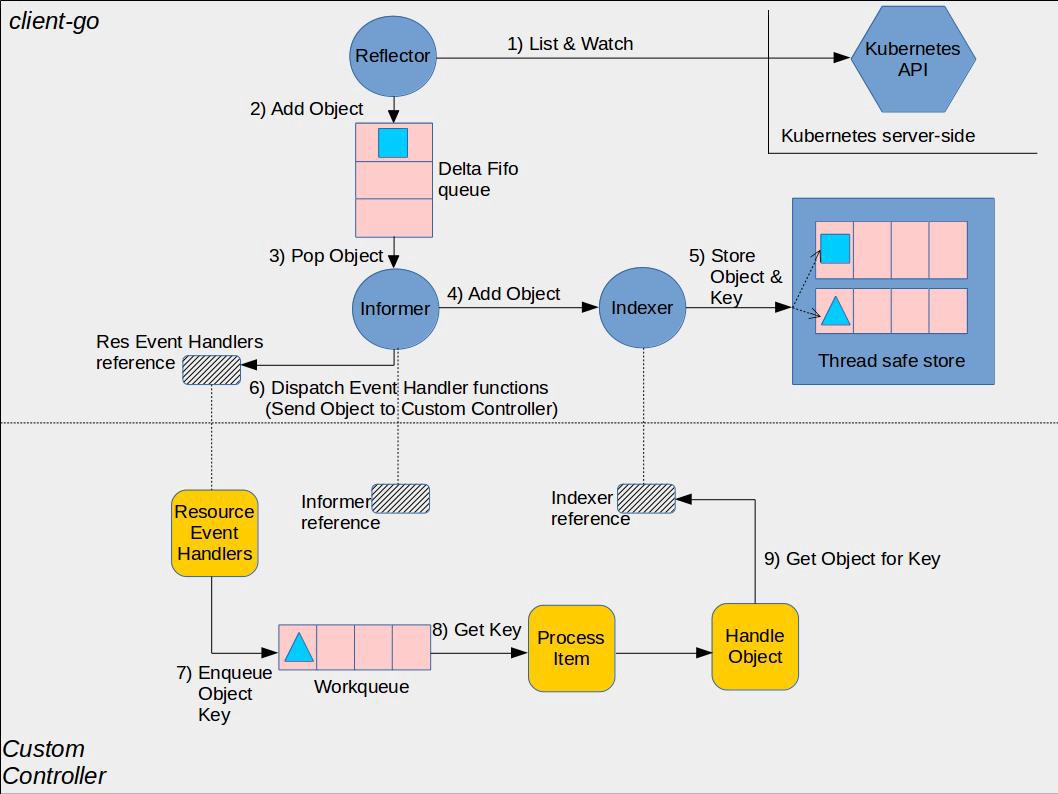
-
see code in https://github.com/kubernetes/client-go/tree/master/examples/workqueue
-
-
qoobo.info qoobo.info
-
太诡异了 哈哈a哈哈
-
-
www.metabase.com www.metabase.comMetabase1
-
seems interesting
-
-
www.quora.com www.quora.com
-
What was it like to be a software engineer at NeXT?
What was it like to be a software engineer at NeXT?
-
-
github.com github.com
-
cache.Indexers{}
so what is this?
-
-
stackoverflow.com stackoverflow.com
-
这个问题值得看看,
- metadata 里,resourceVersion 和 generation 的区别
- 这两个字段分别什么时机会 +1
- 貌似所有object 都有 resourceVersion 字段,但是只有部分有 generation
-
-
rancher.com rancher.com
-
In Rancher, an administrator applies a resource quota to the Project, and then the quota propagates to each Namespace. Kubernetes then enforces the admin’s limits using the native version of resource quotas.
看起来也是利用了原生的 resourceQuota,不知道如何实现的
-
-
www.youtube.com www.youtube.com
-
Life of a Kubernetes API Request by Daniel Smith, Google
-
-
www.youtube.com www.youtube.com
-
Kubernetes Design Principles: Understand the Why
-
-
en.wikipedia.org en.wikipedia.org
-
Resource contention
这儿 contention 理解成竞争(?)
-
-
www.youtube.com www.youtube.com
-
Kubernetes Resource Management, QoS, Resource Quota
keynote:
resource quota related:

-
-
kubernetes.io kubernetes.io
-
provides constraints that limit aggregate resource consumption per namespace
ResourceQuotais namespaced所以自然的,它不支持对 cluster 级别资源的限制
-
-
kubernetes.io kubernetes.io
-
If a request with the dry-run attribute would trigger a call to this webhook, the request will instead fail, and the webhook will not be called.
啥意思,是说如果标记为 Some,dry-run 时就不会被调用么?
-
To validate an object after all mutations are guaranteed complete, use a validating admission webhook instead (recommended for webhooks with side-effects).
言下之意是 validating admission webhook 会在所有 mutation 之后执行,很合理
-
may be reordered
reordered by who?
auto reordered by api-server?
-
-
zhuanlan.zhihu.com zhuanlan.zhihu.com
-
iPhone 充电
-
-
kubernetes.io kubernetes.io
-
BestEffort, the Containers in the Pod must not have any memory or CPU limits or requests.
BestEffort:
- no memory or CPU limits or requests
啥都没有
和 Guaranteed 刚好两个极端,处于中间都就是 Burstable
-
If a Container specifies its own memory limit, but does not specify a memory request, Kubernetes automatically assigns a memory request that matches the limit. Similarly,
container 只配置了 limit 的时候,k8s 会自动给他加上 request
该 request == limit
-
-
zhuanlan.zhihu.com zhuanlan.zhihu.com
-
学习
-
-
-
The .metadata.generation value is incremented for all changes, except for changes to .metadata or .status.
status 的更新不会 inc
.metadata.generationmetadata 也不会,这个有点儿意外
-
PUT/POST/PATCH requests to the custom resource ignore changes to the status stanza.
对 custom resource 的 PUT/POST/PATCH 等更新操作,是忽略 status 的
-
Custom resources are validated via OpenAPI v3 schemas and you can add additional validation using admission webhooks.
two ways of validation
- OpenAPI v3 schemas
- admission webhooks
-
-
github.com github.com
-
seems interesting
-
-
alexanderklopping.medium.com alexanderklopping.medium.com
-
nice e-ink reader showing NYT frontpage
the nyt pdf is especially useful: https://static01.nyt.com/images/2020/11/09/nytfrontpage/scan.pdf
-
-
docs.shippable.com docs.shippable.com
-
nice article, exactly what I am looking for
create kubeconfig file using service account
-
-
kubernetes.io kubernetes.io
-
Administrators might have sets of certificates that they provide to individual users
这是什么意思?
-
-
yaml-multiline.info yaml-multiline.info
-
yaml 牛逼
-
-
kubernetes.io kubernetes.io
-
If a Container specifies its own memory limit, but does not specify a memory request, Kubernetes automatically assigns a memory request that matches the limit. Similarly, if a Container specifies its own CPU limit, but does not specify a CPU request, Kubernetes automatically assigns a CPU request that matches the limit.
配置了 limit,但是没配置 resource 的时候,会自动填补上 resource (== limit)
-
-
istio.io istio.io
-
resource limit on Istio
-
-
www.zhihu.com www.zhihu.com
-
CCM
CCM = Cumulative Clean Mass = 吃尘量
-
单位时间里能净化多少体积的空气
CADR = Clean Air Delivery Rate = 每小时清洁空气立方米
-
-
www.moondownload.com www.moondownload.com
-
reader on Android
-
-
paircast.io paircast.io
-
看起来有点儿意思,值得试一试
-
-
book.kubebuilder.io book.kubebuilder.io
-
This marker is what allows new schemas to be added here automatically when a new API is added to the project.
?
-
-
github.com github.com
-
A basic proof of concept of exporting annotations from PDF into Anki.
via https://www.reddit.com/r/Anki/comments/8lpkjz/a_basic_proof_of_concept_of_exporting_annotations/
-
-
medium.com medium.com
-
flash loan & hack
-
-
forum.makerdao.com forum.makerdao.com
-
flash loan & makerdao
-
-
nomoregoogle.com nomoregoogle.com
-
cool site
-
-
kubectl.docs.kubernetes.io kubectl.docs.kubernetes.io
-
不错的一个找 kustomize 示例的地儿
-
-
kubectl.docs.kubernetes.io kubectl.docs.kubernetes.io
-
Transformers: Modify Resource Config by adding, updating or deleting fields
更新具体的 fields
Generator 和 Transformer 的区别可以简单的说是:
- Generator - 操作文件
- Transformer - 操作字段
-
Type
如上所提及的,下面的 types 就三种:
- Generator
- Transformer
- Meta
-
Meta: Configure behavior of Generators and Transformers
配置 Generator 和 Transformer 本身
-
Generators: Provide Resource Config to Kustomize
给 kustomize 提供配置信息的,比如如下配置里的
resources和configMapGeneratorcommonLabels: app: myWord resources: - dp.yml - svc.yml configMapGenerator: - name: wordpress-map files: - env.startup.txt简单说就是告诉文件在哪儿
-
will have it updated
to what?
-
Reference for Kustomization.yaml
-
-
-
simple & clear intro on WTF is
kustomize
这篇我居然读过。。。完全当新文档看的。。
-
-
istio.io istio.io
-
In particular, you use destination rules to specify named service subsets, such as grouping all a given service’s instances by version
给我的印象是 Destination Rules 就是给 service 分 version 用的
-
RANDOM
效果是每个 subset 里,默认使用 RANDOM 的负载均衡策略
-
host: my-svc
这个 host 又怎么说。。
对应 k8s 的 service ?
-
host: reviews
the hostname is a k8s service
-
Virtual service hosts don’t actually have to be part of the Istio service registry, they are simply virtual destinations.
怎么理解? host 可以随便写?
-
hosts
这儿的 hosts 对应什么, k8s 的 service?
-
看起来似乎 virtual service 主要的功能就是能给 service 分 version 访问
-
Without virtual services, Envoy distributes traffic using round-robin load balancing between all service instances, as described in the introduction.
没有 Virtual Service 的话,用 k8s 的 service 只能有 round robin 的功能,像 灰度发布之类的就没有简单的办法了
-
With a virtual service, you can specify traffic behavior for one or more hostnames.
这个 hostname 是指?
-
Specifying service subsets and other destination-specific policies in a separate object lets you reuse these cleanly between virtual services.
怎么 reuse ?
-
-
martinfowler.com martinfowler.com
-
Although the name for this technique might not be familiar [1], the practice of canary releasing has been adopted for some time. Sometimes it is referred to as a phased rollout or an incremental rollout.
好吧,几个名字一个意思
- canary release
- staged rollout
- phased rollout
- incremental rollout
- 灰度发布
-
-
www.jianshu.com www.jianshu.com
-
不错的总结
- 蓝绿 - 流量切换 standby
- 滚动 - 现有集群中逐渐升级
- 灰度/金丝雀 - 新老并存,逐渐切换
-
-
istio.io istio.io
-
policy enforcement component
?
-
-
arxiv.org arxiv.org
-
-
measure system call
-
-
pages.cs.wisc.edu pages.cs.wisc.eduVideos1
-
videos for OSTEP
-
-
www.forbes.com www.forbes.com
- Oct 2020
-
www.jianshu.com www.jianshu.com
-
1秒(s) =1000毫秒(ms) 1毫秒(ms)=1000微秒 (us) 1微秒(us)=1000纳秒 (ns)
以 1k 为单位递进
-
-
www.youtube.com www.youtube.com
-
换气, 口鼻
-
-
www.cs.utexas.edu www.cs.utexas.edu
-
consider the stack on which the operating system must run when it receives the system call. Should this be a different stack from the one that the application uses, or could it use the same stack as the application program? Assume that the application program is blocked while the system call runs.
没看懂
Tags
Annotators
URL
-
-
en.wikipedia.org en.wikipedia.org
-
The term "x86" came into being because the names of several successors to Intel's 8086 processor end in "86", including the 80186, 80286, 80386 and 80486 processors.
好几个使用了这个指令集的 CPU 的型号都以 86 结尾,所以将此指令集以 x86 命名
-
-
github.com github.com
-
mac window management
-
-
github.com github.com
-
mac window management
-
-
github.com github.com
-
mac window management
-
-
github.com github.com
-
mac window management
-
-
istio.io istio.io
-
FAQ on Istio Security
感觉有效信息挺多
-
-
istio.io istio.io
-
-n istio-system
this PeerAuthn policy is installed in root istio ns: istio-system
-
-
kubernetes.io kubernetes.io
-
curl --cacert ${CACERT} --header "Authorization: Bearer ${TOKEN}" -X GET ${APISERVER}/api
directly curl API server
展开一下就是:
curl --cacert /var/run/secrets/kubernetes.io/serviceaccount/ca.crt \ --header "Authorization: Bearer $(cat /var/run/secrets/kubernetes.io/serviceaccount/token)" \ https://kubernetes.default/api
-
-
finance.sina.com.cn finance.sina.com.cn
-
kubernetes.io kubernetes.io
-
这篇对网络隔离可能有帮助
key words:
tenant, network isolation, api-server, kubelet, etcd
-
-
istio.io istio.io
-
cluster.local/ns/default/sa/productpage
principal is just service account
-
-
tools.ietf.org tools.ietf.org
-
The "aud" (audience) claim identifies the recipients that the JWT is intended for.
貌似可以理解成使用(消费)这个 JWT 的 app 的名字
-
-
-
audience
what is audience?
-
-
istio.io istio.io
-
rules:
two rules:
- one with
fromonly - another with
toonly
first requires JWT on all paths, second allow request to
/healthzwith no requirementthus: require JWT on all paths, except /healthz
- one with
-
-
-
JSON Web Key Set
The JSON Web Key Set (JWKS) is a set of keys containing the public keys used to verify any JSON Web Token (JWT) issued by the authorization server and signed using the RS256 signing algorithm.
https://auth0.com/docs/tokens/json-web-tokens/json-web-key-sets
-
Peer authentication policies specify the mutual TLS mode Istio enforces on target workloads
特么就一个作用啊,就是启动 mTLS?
-
The following modes are supported
3 modes of mutual TLS supported for peer authn policies:
- strict
- permissive
- disable
-
When you configure multiple mesh- or namespace-wide peer authentication policies for the same mesh or namespace, Istio ignores the newer policies. When more than one workload-specific peer authentication policy matches, Istio picks the oldest one.
peer authn policy:
- 如果 mesh 或 ns 级别的 peer authn policy 有多条,用最老的
- workload 级别的有多条,用最老的
特么
ignores the newer policies.
和
Istio picks the oldest one.
不是一个意思么。。。
-
authentication policies apply to requests that a service receives. To specify client-side authentication rules in mutual TLS, you need to specify the TLSSettings in the DestinationRule.
没太懂
-
peer and request authentication policies
authn policies 分两种:
- peer authn policy - PeerAuthentication
- request authn policy - RequestAuthentication
-
Istio stores mesh-scope policies in the root namespace
默认情况下,安装在 istio-system 里的 authn policy 是全局配置
-
The control plane watches the apiserver, generates the secure naming mappings
根据什么信息来生成 secure naming mappings?
-
Identity Provision
nice pic
-
Istio agents
这是个之前没听说过的 Istio 新组件
-
exchange credentials with their identity information
credentials 这儿是指的证书
那 identity 呢?是 service account
所以证书里有 service account 信息
-
Kubernetes: Kubernetes service account
好吧,k8s 上,identity 就是 service account
-
and reject any clients who failed to pay their bill from accessing the workloads
有点儿我们 saas 收费的意思了
-
authentication, authorization and audit (AAA) tools
AAA:
- authn
- authz
- audit
-
-
-
nice write up on mTLS
-
Verifying Alice is actually Alice is a much less common operation, but is generally called “Mutual TLS authentication” as both Alice and Bob are verified.
好吧,我懂了,mTLS 之所以比较少听到,就是应为它的场景更少一些
合理了
-
-
rekt.ghost.io rekt.ghost.io
-
flash loans
Tags
Annotators
URL
-
-
kubernetes.io kubernetes.io
-
SCTP support
WTH is this?
-
in the "default" namespace
?
-
-
istio.io istio.io
-
Audit a request if it matches any of the rules.
log request
-
-
banzaicloud.com banzaicloud.com
-
Istio 和 k8s 中的访问控制 access control
- istio - AuthorizationPolicy
- k8s - NetworkPolicy
-
principal
这个
principal是个什么鬼东西?
principal:
- 校长
- 主要的
-
the same goal could have been achieved with two different AuthorizationPolicy entries for the two different rules
不同 AuthorizationPolicy 之间的关系也是:或, 有其一通过即通过
-
Istio has a data plane, and a control plane.
nice pic showing data plane & control plane

-
-
github.com github.com
-
via istio
-
-
github.com github.com
-
via 《云原生服务网格 Istio》
-
-
istio.io istio.io
-
Service-level
这个 service 貌似就是 k8s 的 service
-
-
github.com github.com
-
via https://kubernetes.io/docs/concepts/services-networking/network-policies/
totally have no idea what this is...
-
-
github.com github.com
-
via david, multi-tenancy, network isolation
-
-
dodoex.github.io dodoex.github.io
-
math is simple
Tags
Annotators
URL
-
-
dodoex.github.io dodoex.github.io
-
Single Risk Exposure
how?
-
But what about impermanent loss, i.e. how does PMM ensure that liquidity providers get what they deposited when they withdraw their tokens? The answer is by encouraging arbitrage trading.
?
-
-
pages.cs.wisc.edu pages.cs.wisc.edu
-
OSTEP home page
-
-
github.com github.com
-
source code for OSTEP
Tags
Annotators
URL
-
-
pdos.csail.mit.edu pdos.csail.mit.edu
-
a demo os
-
-
kuboard.cn kuboard.cn
-
貌似是另一个 k8s 的 dashboard,页面全但是感觉使用比较复杂
可以关注
-
-
github.com github.com
-
k8s 安装工具?
via minghua
-
-
github.com github.com
-
via david, multi-tenancy
Cloud native networking and network security
-
-
github.com github.com
-
about.gitlab.com about.gitlab.com
-
gitlab Tech stack
-
-
github.com github.com
-
github.com github.com
-
webhook for native k8s resource
-
-
github.com github.com
-
a set of go libraries for building Controllers
libs for building controllers
-
via https://book.kubebuilder.io/reference/controller-gen.html
-
-
github.com github.com
-
webhook for k8s native resource
-
-
www.joinquant.com www.joinquant.com
-
via cc, 量化交易
-
-
github.com github.com
-
Founder
Founder @appscode
-
-
www.qikqiak.com www.qikqiak.com阳明的博客1
-
这个个人博客看起来不错啊,k8s 相关
-
-
www.youtube.com www.youtube.com
-
multi-tenancy
-
-
www.qikqiak.com www.qikqiak.com
-
via david
可能是不错的中文文档
-
-
blog.golang.org blog.golang.org
-
worth reading
-
-
kubernetes.io kubernetes.io
-
An admission controller is a piece of code that intercepts requests to the Kubernetes API server prior to persistence of the object, but after the request is authenticated and authorized.
An admission controller:
- a piece of code
- that intercepts requests to k8s API server
timing:
- before persistence of the object
- but after the request is
authned &authzed
-
-
kubernetes.io kubernetes.io
-
In addition to compiled-in admission plugins, admission plugins can be developed as extensions and run as webhooks configured at runtime.
Admission Controller 是 k8s 官方的代码,而用户可以通过 Admission Webhook 的方式,添加一些自己的逻辑,来修改和校验到 k8s api server 的请求
-
-
news.ycombinator.com news.ycombinator.com
-
seems a good article/paper explaining zk-Snark
-
-
www.zhihu.com www.zhihu.com
-
英文 广度 推荐
-
-
www.boox.com www.boox.com
-
看着不错啊
-
-
tutorials.jenkov.com tutorials.jenkov.com
-
Common Pitfall: Calling run() Instead of start()
坑爹。。
-
-
en.wikipedia.org en.wikipedia.org
-
可算明白了 Monitor 和 Lock 的区别,Monitor 是一个完整的结构,其构成元素里包括 Lock,还包括若干 Condition Variables (条件变量)
type Monitor struct { Lock Lock EntranceQueue []Thread CVs []ConditionVariable } type ConditionVariable struct { WaitingQueue []Thread }
想象 Monitor 是一个房子,所有强锁的线程先进这个房子,如果 Lock 已被占,则在这个入口等着,否则拿着锁进入正厅,执行业务逻辑
如果不需等待某些条件,则直接执行,最后退出,并释放锁,让其他线程进入,否则
在 while 循环中等待条件变量成立,同时释放锁,进入等待室,等待其他入口处的线程进入正厅后,可能执行的 nofity,被唤醒后,去入口处,重新等待获锁,之后检查条件时候确实成立(在 while(P)中),如果否,则再次 wait,如果真,则可执行业务逻辑,有需要的话退出前也执行 nofity(), 退出释放锁,结束
总结来说,monitor:一把 lock,两个 waiting queue
ps. 这个图也不错
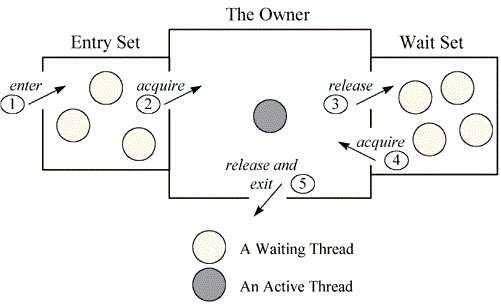
-
wikipedia 的(有些)文章质量真高啊
-
A Java style monitor
nice and clean pic showing Java style monitor:
- 1 implicit condition variable
-
The operations notify c and notify all c are treated as "hints" that P may be true for some waiting thread.
notify¬ifyAllis a hint that condition might be true -
condition variable c
这儿
c是一个代称,指代 condition variable,对应右图中的a,b -
The implementation given here is incorrect
啊?
-
Sample Mesa-monitor implementation with Test-and-Set
有点儿太底层,已经不太看得懂了,只明白个大概
-
signal(queueEmptyCV); -- OR -- notifyAll(queueEmptyCV);
wake up consumers waiting because of empty queue
-
bounded producer/consumer problem
这个 bounded producer/consumer problem 特别适合用来帮助理解 monitor
- lock, 保护 bounded queue
- condition variables:
- producer: queue is not full
- consumer: queue is not empty
-
signal c
notify()in Java -
broadcast c
notifyAll()in Java -
Monitors provide a mechanism for threads to temporarily give up exclusive access in order to wait for some condition to be met, before regaining exclusive access and resuming their task.
所以除了 lock 之外,monitor 还有一个功能就是可以让线程放弃🔒,直到它需要的条件成立,再才重新获得🔒
这是 monitor 比 lock 多的一点涵义
-
A monitor consists of a mutex (lock) object and condition variables.
这儿看出点儿 monitor 和 lock 的区别了
monitor 是一个结构,包括两个元素:
- mutex (lock)
- condition variables
-
In concurrent programming (also known as parallel programming), a monitor is a synchronization construct that allows threads to have both mutual exclusion and the ability to wait (block) for a certain condition to become false.
monitor, two feature:
- mutex
- the ability to wait for a certain condition to become true
-
-
stackoverflow.com stackoverflow.com
-
In retrospect, this design decision was probably a bad one: not only can it be confusing, but it forces JVM implementors to make tradeoffs between object size and locking performance.
哈哈
-
-
twitter.com twitter.com
-
via report on Thai Protest
-
-
www.techopedia.com www.techopedia.com
-
A mutual exclusion (mutex) is a program object that prevents simultaneous access to a shared resource.
才发现 mutex 原来是 MUTual EXclusion 的缩写
- mutual: 相互
- exclusion: 排斥
- mutual exclusion - mutex - 相互排斥 - 互斥
-
-
appscode.com appscode.com
-
a k8s company, via https://twitter.com/tsaha
-
-
twitter.com twitter.com
-
seems working on some serious shit of k8s
-
-
github.com github.com
-
intentionally
?for what
-
It makes decisions by evaluating the incoming object against all defined ResourceQuota.Status.Hard resource limits in the request namespace.
看起来官方的 ResourceQuota 也是用的 Admission Webhook 来实现的
-
-
rancher.com rancher.com
-
Project Limits
可以借鉴
-
-
en.wikipedia.org en.wikipedia.org
-
-
might be useful for Kalm Resource Quota
Tags
Annotators
URL
-
-
rancher.com rancher.com
-
信息量几乎为零的一篇文章。。。
-
Rancher goes beyond Namespaces by including a Project resource that helps ease the administrative burden of clusters
这个也是我们想要的啊
-
“If launching another resource in the Namespace would exceed the quota, then nothing else gets to launch,” Goins noted.
引用自己公司的文章的做法,就一个字:骚
-
-
kubernetes.io kubernetes.io
-
Configurations for local ephemeral storage
没看懂
-
The amount of resources available to Pods is less than the node capacity, because system daemons use a portion of the available resources.
Allocatable < Capacity
-
more than 1120m CPUs or 6.23Gi of memory, it will not fit on the node
how come the numbers?
1120m CPUs or 6.23Gi of memory
- CPU, allocatable - allocated = 1800m - 680m = 1120m
- memory, allocatable - allocated = 7474992Ki - 920Mi = (7474992/1024.0 - 920) / 1024 = 6.23Gi
-