from - mixing javascript "class-free" objects

Replacing JavaScript Classes With The Module Design ...DEV Communityhttps://dev.to › bytebodger › replacing-javascript-class...DEV Communityhttps://dev.to › bytebodger › replacing-javascript-class...Mar 1, 2021 — Hi. My name is "Adam" and I'm a JavaScript developer. I've been class-free now, for... Oh, wait. I think I'm mixing up my meetings.

google - search - mixing javascript "class-free" objects
Mirrors as Reflective Capabilities
x
Programs as DataTreating programs as data means that all the benefits of synchronization carryover directly to programs as well. Just as there is one current version of the data(with auditable, consistent snapshots representing the past), there is one cur-rent version of all applications, which is consistent with the data (and likewise,consistent snapshots of the past).This economy of mechanism translates directly to a smaller platform, whichhas smaller footprint and is easier to maintain.Nevertheless, some care must be taken for this vision to work
yes forward compatibility evergreen software
Orthogonal Synchronizability
no need for this if data is always stays with its cfeator
The Newspeak Programming PlatformArticleJan 2008

Context Traits
objectscan be regarded as evolving entities that are shaped by theirenvironmen
0bjects as evolving entities
Context-oriented programming emerged as a new paradigmto support fine-grained dynamic adaptation of software beha-viour according to the context of execution
context-oriented programming
context of execution
CONCLUSION
Traits have been proposed to overcome - imitations of composition in object-oriented languages,
by having - better granularity and - no imposed composition semantics.
COP too has been proposed to overcome some of the limit- ations of composition in object-oriented languages, namely219 the lack of run-time behaviour adaptability.
marry best of those two solutions. - contribution to research on COP - by proposing traits as units convenient granularity for dynamic behaviour adaptation and - a well-defined composition semantics.
On the other hand, the paper proposes a contribution to research on traits by - proposing a simpler traits model and - a way of using it dynamically depending on detected context changes.
At the crossroads of both approaches, we have found a convenient way of developing software applications that need to evolve according to their changing environment of execution.
Context traits: dynamic behaviour adaptation through run- ...Pennsylvania State Universityhttps://citeseerx.ist.psu.edu › documentPennsylvania State Universityhttps://citeseerx.ist.psu.edu › documentPDFby S González · 2013 · Cited by 51 — Since contexts are singletons, the classless object model of. JavaScript is a better paradigmatic match than a class-based.
Holochain empowers people and communities
to reclaim control of their data, identity, and agreements
from - surveillance-based businesses.
We can build and run the same web apps we’ve come to rely on (like - social networks, - communication, - marketplaces, - knowledge sharing).
Holochain, an alternative to blockchain for running fully P2P distributed applications.
building a better Decentralized Web based on the values of equity, trust, and distributed values, can congregate.
distributed values
After a quick install, you can help us beta test the Emergence App
beta test emergence app
Jun 7MEET UP: DWeb Camp Projects & Presentations
The Most Elegant Explanation of Taoist Philosophy | Terence McKenna
https://bafybeifig3gvvkany4nixxfr4whgyf7hvcolbk4wcyf4az73pzazhji67e.ipfs.w3s.link/The%20Most%20Elegant%20Explanation%20of%20Taoist%20Philosophy%20Terence%20McKenna.3gp
if the 00:00:38 nonhuman knowledge
if human knowledge - isn't a shared resource then what is? - what civilization been doing all these years
a company that built 00:00:51 this database called freebase was free database
a company called metaweb ~ built - FreeBase - was a free database
<laugh>
Google 2.0: Why MIT scientists are building a new search engine | Danny Hillis | Big Think
Fast html code snippet: <style type="text/css"> .video-js .vjs-time-control{display:block;} .video-js .vjs-remaining-time{display: none;} </style>
show current time on videojs
Make your player yours with the world's most popular open source HTML5 player framework
make your players yours

memex
Building the Future - Daniel Hillis
Windows 11 optional updates: Here why you should wait Status is online Joshua Bevis We help London based businesses transform their IT
Zoltan Kovacs 3rd degree connection 3rd CTO at United Technology Alliance
🌍 Spectrum Search are a global specialist recruitment agency who enable tech companies to scale at pace. Our clients consist of high growth companies
hyper seminar and annotate and link the hell out of it maybe with tools like hypothesis
Doing it right Now
Bootstrapping the Indy/Verse/Net/Web to begin with to be able to do just that

aimed to be consumed as hypermedia interlinked and Inter twinkled with everything else
doing it right here
Hyper Video
Danny Hillis

Dany Hillis - is - co-founder and co-chair of the long now foundation - the designer of the 10,000 year clock he has - 300 patents invented
was a large part of - inventing massive parallel processing and - meta web which is part of how Google search actually works - the pinch that you do to make things larger and smaller on your iPhone all comes from
Danny he is particularly interested in
how the internet and everything else having to do with - the infrastructure - info structures of civilization - going forward - can best to go forward
Long Now Foundation
Fostering Long Term Responsibility
Infrastructure for Info-Structure
3,776 views Feb 11, 2020 Long Now Seminars "We live in a spectacular time,” says Juan Benet. "We're a century into our computing phase transition. The latest stages have created astonishing powers for individuals, groups, and our species as a whole. We are also faced with accumulating dangers -- the capabilities to end the whole humanity experiment are growing and are ever more accessible. In light of the promethean fire that is computing, we must prevent bad outcomes and lock in good ones to build robust foundations for our knowledge, and a safe future. There is much we can do in the short-term to secure the long-term." "I come from the front lines of computing platform design to share a number of new super-powers at our disposal, some old challenges that are now soluble, and some new open problems. In this next decade, we’ll need to leverage peer-to-peer networks, crypto-economics, blockchains, Open Source, Open Services, decentralization, incentive-structure engineering, and so much more to ensure short-term safety and the long-term flourishing of humanity.” Juan Benet is the inventor of the InterPlanetary File System (IPFS)---a new protocol which uses content-addressing to make the web faster, safer, and more open—and the creator of Filecoin, a cryptocurrency-incentivized storage market. "Long Term Info-structure" was given on August 06, 02018 as part of Long Now's Seminar series. The series was started in 02003 to build a compelling body of ideas about long-term thinking from some of the world's leading thinkers. The Seminars take place in San Francisco and are curated and hosted by Stewart Brand. To follow the talks, you can: Subscribe to our podcasts: http://longnow.org/seminars/podcast Explore the full series: http://longnow.org/seminars More ideas on long-term thinking: http://blog.longnow.org The Long Now Foundation is a non-profit dedicated to fostering long-term thinking and responsibility. Our projects include a 10,000 Year Clock, endangered language preservation, thousand year+ data storage, and Long Bets, an arena for accountable predictions. Become a Long Now member to support this series, join our community, and connect with our ongoing work to explore and deepen long-term thinking: http://longnow.org/membership Like us on Facebook: https://www.facebook.com/longnow Follow us on Twitter: https://www.twitter.com/longnow
summary
An Architectural Approach to Decentralization
I know my problem with all this has been undue focus on Information and decentralization instead of being People-Info-Service Centered autonomous omni present evergreen co-evolutionary mutual arising
symbolic (human-meaningful) side of AI
human meaningful side of AI
InfoCentral is in transition..
Blue knot
Reality is a strange loop and you don’t know it.
Concepts: Sketch, Note, Draw
concept (n.)"a general notion, the immediate object of a thought," 1550s, from Medieval Latin conceptum "draft, abstract," in classical Latin "(a thing) conceived," from concep-, past-participle stem of concipere "to take in and hold
take hold

conceit (n.)late 14c., "a thought, a notion, that which is mentally conceived," from conceiven (see conceive) based on analogy of deceit/deceive and receipt/receive.
conceit receive
CONCEPT FORMATION - Psycholog
In contrast, a write-ahead log provides a limited history of recent changes which is retained only until the whole system state can be reliably persisted - meanwhile, the application logic is not expected to change.
write ahead log provides the abiity to "derive the future system state from the combination of past events"
Another way to think about it: a write-ahead log is a component of the database engine, but event-sourcing will often manifest as one or more *tables* in said database.
contrast the human response to the machine
write ahead log is a kind of implicit event sourcing relying on a perfect history of data input with an implicit interpretation very much event sourcing that in this case is about manifesting a database table from input recorded in fast storage
Sage · AI botBeta
Event sourcing and a write-ahead log are both architectural patterns that are used in the realm of software development and databases.Event sourcing is a pattern that is used to record the state changes of an application over time. It involves recording every change to the application's state as an "event", which is then stored in an event store. This allows for the replay of the application's state changes, which can be useful for debugging, auditing, and other purposes.A write-ahead log, on the other hand, is a pattern that is used to ensure the durability of data in a database. It involves writing every change to the database to a log file before it is made to the actual data. This ensures that, in the event of a crash or other failure, the changes that were made to the database can be replayed from the log file, thus restoring the database to a consistent state.So, event sourcing and a write-ahead log have some similarities, but they are used for different purposes. Event sourcing is used to record the state changes of an application, while a write-ahead log is used to ensure the durability of data in a database.

What is the difference between event sourcing and a write- ...Quorahttps://www.quora.com › What-is-the-difference-betw...Quorahttps://www.quora.com › What-is-the-difference-betw...Dec 24, 2011 — Event sourcing and a write-ahead log are both architectural patterns that are used in the realm of software development. Continue reading.
Write-Ahead Logging

the alien is real but it is within us it can only communicate information and that 00:43:53 information has to be made real in this world by human coders
the alien is real
has to be made real in this world by human coders
https://youtube.com/clip/UgkxtBVBSgTjJxtKudf7yi5nKTSrZ4a9NKdJ
the alien is real. it is within us. In-for-mation has to be made real in this world in man-machine symbiosis. Not inventing discovering
real as in concepts that are reasonable, made concrete, it is not the word that creates its particulars
the alien is already within us but we must 00:44:42 model it we must call it fourth into a dimension of potential dialogue and I think that ultimately this is what 00:44:55 high-tech Society can bring to the shamanic equation
must model it
externalized it, manifest it in shareable, commincate it/ scale its reach and synthesis FAIR form
enter into dialogu
the alien is a creature of pure information 00:42:47 it's purely information it's non-local it comes out of the Bell non-locality part of the universe that exists distributed through hyperspace the alien 00:43:00 is real but it is only made of information and therefore the only dimension in which it can be encountered 00:43:12 is a dimension of pure information fortunately we are building a dimension of pure information providentially we have named it the net
The Alien is a creature of pure in-for-mation, , (n)on-local situated inter personal HyperSpace, The net is a net for catching the alien
https://youtube.com/clip/UgkxALNgL2sZSVzBDa47uzH-TJiH2I3sJ0Nv
dimension of pure information the net
the net tfor catching the alien
it will 01:02:04 lead us to be a symbiotic species if we if we put the pedal to the metal that for people like yourselves who I assume to be no matter how you finagled your way in here this afternoon part of the 01:02:18 upper three percent of the ruling Elite on this planet there is a real obligation to use privilege to uh communicate and to make art I think this 01:02:31 is what is the good life has any purpose other than to drink beer and watch TV it's to produce art this is how you make a payback into the community and already 01:02:43 ambiguous your art may say things to people other than yourself that it would never say to you but that's how we make the community richer that's how we enlarge the dimensions of the human soul 01:02:57 by by making ours
enlarge the dimensions of human soul with art
if you're looking for the thumbprint of 01:01:39 almighty God on the biological organization of this planet it is human language it is a miracle
human language
language needs to evolve toward the visual and that's why I'm very keen for technically against prosthetic environments where every time 01:00:18 you say the word and a yellow three-dimensional triangle appears in the air every time you stay or an orange ball appears a computer is listening to what you're saying and giving a 01:00:31 geometric accompaniment to speech I think that there are forms of telepathy that we can evolve through the use of drugs and computer-assisted technologies that will allow us to see each other's 01:00:45 dreams in spite of your correct assessment that I'm Keen for the spoken word I spend all summer learning modeling and three-dimensional animation programs from my son 01:00:58 because I want to animate I want to model I see things on my trips that I have never been able to English but that if I were a fully competent modeler and animator I would just say 01:01:13 check it out and I'm going to do that and and I urge you to do that I mean it's a funny thing to be told you want to spiritually Advance the study 01:01:25 3D animation but these are the frontiers of communication we have an obligation to make our language more immediate it is the most Godlike thing we do if you're looking for the thumbprint of 01:01:39 almighty God on the biological organization of this planet it is human language it is a miracle I don't give a hood what the Dolphins and the honeybees are out there in the woods doing it 01:01:51 ain't like Milton it ain't even like Bob Dylan it ain't even as good as this I'm willing to say uh no human human communication is what
visual
he robots who preach 00:54:19 his freedom
roboit preach his freedom
a commitment to community and a model of to the 00:53:46 future without fear without fear thank you very much
commitment to comunity
selling the future as an aid alarm fire which is how the media does it uh only 00:52:00 makes the same future impossible
alarmist media
hearing optimistic and reasonable rhetoric about the future selling the future as an aid alarm fire which is how the media does it uh only 00:52:00 makes the same future impossible so we need a responsible approach to thinking about the future and it means taking personal responsibility for your 00:52:14 drug taking for the ideas the means that you push into society and for the images that we share among ourselves
responsible approach to thi9nking about the future
so liberate yourself from the illusion of culture take responsibility for what you think
take responsibility for what you thing and do
inform yourself what does inform yourself mean it means a transcends and mistrusts ideology go for direct experience what do you think when 00:50:40 you face the waterfall what do you think when you have sex what do you think when you take psilocybin everything else is unconfirmable rumor useless probably lies
inform yourself
deal with the raw data and trust yourself nobody is smarter than you are
deal with the raw data trust yourself
nobody understands what is happening
forget ideology
political implication is a personal one
political implications personal
destined to become mental creatures
mental creatures
promising presence of this intelligent others which beckons us out of history and says you know the Galaxy lies waving a galaxy of 00:48:12 galaxies lie waiting lose the encumbrances of three-dimensional space return with the word to its higher and 00:48:24 hidden source and at that point you will discover the alchemical uh uh uh paracletes will be given unto you the 00:48:37 alchemical dispensation will be given and as James Joyce said man will be dirigible
dirigibler
Midwife thing the burst of an entirely 00:47:07 new not species but order of biological and intelligence in existence the human machine symbiote 00:47:20 is upon
the human machine symbiote
using our flesh and our thoughts to bootstrap itself to higher and higher levels
bootstrap
we are not what we thought we were the the monkey flesh is penetrated by something 00:46:00 dare I say it divine
money divine
we would realize we are not 00:44:17 inventing this we are discovering
not inventing it but discovering it
there is an alien we are in the cultural process of 00:41:38 meeting this alien but they do not come in Thousand ton beryllium ships from the nebul ganubi to trade high technology for human people tissue and that's if you that's an intelligence 00:41:53 test folks uh that's not how it works uh our own hysteria makes it very difficult for us to deal with the presence of the alien and the alien knows that that's 00:42:08 why it has disguised itself as a psychedelic experience
alience disguised as psychedelic experience
true resistor of 00:41:02 the alien penetration of human civilization because I just saw no evidence
no aliens
nature has always operated as an integrated system of communication
communication system
it's that way because our cultural tradition is one of reductionism tear things apart break them into their 00:39:57 subordinate units break those into still smaller units well when you have a theory of reality like that what you end up with is all the pieces spread out and 00:40:08 no car and nowhere to go
reductionism
the internet is the beginning of a nervous system that is missing not 00:39:20 only all human beings but all life together all information together
internet
everywhere or nowhere the point is
everywhere and nowhere
descending 00:38:04 now into a well of novelty such that more change is now occurring in a single human lifetime than incurred in the previous ten thousand years of human 00:38:16 history we are approaching at a faster and faster rate something Unthinkable something which is sculpting Us in its image something which shamans have always 00:38:30 known was there
well of novelty
the uh acceleration into novelty is rewriting the rules now every 18 months
acc
caught in a basin of attraction to use a mathematical term in other words we are 00:37:22 under the influence of something which is pulling us into the future or into novelty if you want to put it that way at a faster and faster rate
basing of attraction faster and faster
acceleration of change
accekeratiuon of change
they stayed potheads can't see
potheads
process of complexification is occurring faster and faster
complexification faster
measure 00:34:34 it against your own experience
measure against your own experience
ten years ago there was no internet 18 months ago there was no Java things are complexifying intensifying moving together this is the universal drama 00:34:21 that is reaching culmination in our lifetimes
10 years ago no internet
the law of increasing complexity have gotten more complicated through time
increasing complexity through time
their experience has very little congruency with your own
experience little congruence
psychedelics address they address US uniquely as individuals
psychedelics address US uniquely
any change in any system 00:31:41 that you can think of is always ultimately traceable to one unit in the system undergoing a phase State change of some sort no group there are no group 00:31:56 decisions those things come later the genius of creativity and of initiation of activity always lies with the individual
individual change genius of creativity
we need to celebrate is the individual
celebrate the individual
he reality of the individual identity
individual identity
gross simplifications betray Humanity betray uniqueness make same politics impossible
sane politics impossible
culture is not your friend
culture is not your friend
if you can make people think alike they 00:29:09 will buy a life they will worship a light and if you know politics demands it they will kill a lie
think buy kill alike
the truth is that you are not created equal with yourself from day to day 00:28:28 leave alone any comparison with anybody else
not created equal with yourself let alone
cultural myths are that we are all alike we Americans each created equal 00:28:05 I mean if you can believe that at an operational level then I have some breaches I would like to sell you
uniformitarianism bridge to sell you
find the others
find the Others
we're cutting the Earth from beneath our own feet we're poisoning the atmosphere that we breathe this is not intelligent Behavior this is 00:24:31 a culture with a bug
culture with a bug
a more tolerant operating system or its plug-in supports special effects denied the positivist
positivist
what does it mean to be human
what does it mean to be human what kind of circumstance are we coughing and what kind of structures if any can we put in place to assuage the pain and accentuate the glory and the wonder that lurks waiting for us in this very narrow slice of time between the birth canal and the yawning grave
https://hyp.is/QKIuuP1iEe2hTCN2MF2SUg/www.youtube.com/watch?v=xN1UBOSgigc
https://hyp.is/QKIuuP1iEe2hTCN2MF2SUg/www.youtube.com/watch?v=xN1UBOSgigc
WHAT KIND of Novel Is Your Life? - Terence McKenna - Black Screen

WHAT KIND of Novel Is Your Life? - Terence McKenna - Black Screen

🌱
🌱
Forbes Digital AssetsDaily CoverJack Dorsey-Backed Decentralized Twitter Rival Prepares To Launch With One Million Users

The Metaphysics of Adjacency
Reticulate writ large

III DEVELOPMENTS IN USER-SYSTEMFEATURES
.png)
.png)
STUDY FOR THE DEVELOPMENTOFHUMAN INTELLECT AUGMENTATION TECHNIQUE

source - http://129.69.211.95/pdf/sri/arc/Study_For_The_Development_of_Human_Intellect_Augmentation_Techniques_Report_2_Aug69.pdf

David West OOP is Dead! Long Live OODD!
from : https://hyp.is/OsPHOP5GEe2k8ccRVOSY7w/www.yegor256.com/2016/09/20/oop-without-classes.html
he said that classes were not meant to be in object-oriented programming at all
no classes in object oriented programming
With the current version of Chrome (51.0.2704.106 (64-bit)) you can just right-click an url and then open it with the fourth menu choice from top: "Open Link as PROFILE" (your configured Chrome profile).

Shortcut to open specific link in specific chrome profile5 answersAug 27, 2021
Shortcut to open specific link in specific chrome profile
I set up an international Consortium based in London


https://hyp.is/aa4S4P3pEe25yPvCws6qPA/www.youtube.com/watch?v=SyPzD7RAbaU
https://bafybeiajnpbgcwit6hynvfr6z5ihbdpwnv5nm3gry6xfxwqy7n5nbhzzye.ipfs.w3s.link/The%20Future%20Of%20Our%20Society%20ISNT%20Looking%20Good...%20Jordan%20Peterson(1).3gp
The Future Of Our Society ISNT Looking Good... | Jordan Peterson


"To A Mind That Is Still, The Whole Universe Surrenders."
for : solipsism
The Neuroscience Of Awakening: Your Brain On Buddhism
Web3 Bends the Knee to Apple
from this Awakening we start to create meaning instead of taking away meaning from what we took for granted we 00:09:29 start building it on a firm foundation of of nothing do you see what I did there when our foundation is nothing capital N nothing 00:09:47 then that is a canvas of creation so I haven't directly answered the question but I think this does open up some 00:10:08 Avenues of exploration
firm foundation of capital N nothing
solipsism

https://bafybeib3yi4wuol2utsd52ajonemn5sfuwphnzyixpys5afccu4x5b4qom.ipfs.w3s.link/_95%20%20When%20does%20Philosophy%20become%20Spiritual%20%20%20or%20%20The%20Hyperboloid%20of%20Truth%20%20-%20YouTube.png

A protocol for thought.
interoperable with constellations for thinking and l(e)arning together supporting infformation/knowledge flows from autnbonomous individual to networked autonompous emnergent co-labortive thinkgin learcning spaces
emergent evergreen co-evolutionay Open Learning Commons*
Check out our Roadmap
deploy infrastructure that interoperates over Noosphere.
yes
open-ended, permissionless multiplayer experience.
trustful multiplayer co-creation
a worldwide medium for thinking together
interpersonal medium for thinking and l(e)arning together
A decentralized graph, where you own thoughts, and have agency to move your data between services and apps. If that sounds like your jam, come build with us!
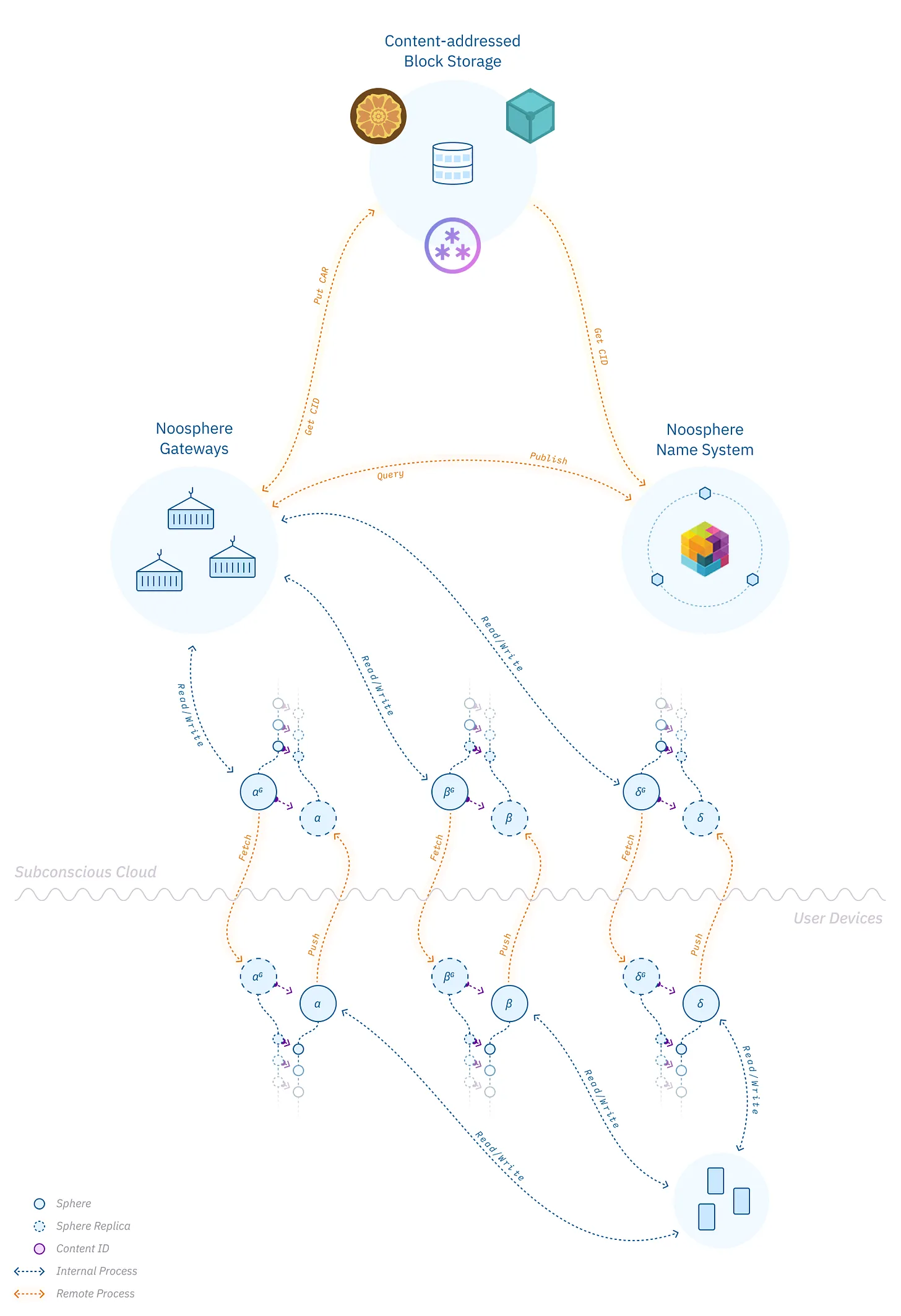
decouples your data
decoupling of data from services is
the essence of Web 3 indeed
decouples your data from any particular app or domain.
decouples your information from any particular app (serice) or domain
Can do better, share likewise the very "services" that you can own for all your information/work flows you constellate
Your sphere is like your inventory on Noosphere. It’s a data structure that contains your content and contacts.
A worldwide decentralized thought graph, made up of individual graphs called spheres
decentralzied,is at least decent, combine that and make it interoperable with a people centered networks of trusts in the long tail
protocol for thought
complete that with constellations for augmented thinking, mutual learning and co-laboration
IDs are upstream of access
flip all that
operate with virtual ids and establish trustful connections downstream based on mutual trust and shared information about aspect of each other's digital self.
user agency
An oxymoron
are a user of service that you authenticate with, access, and hand over your data, you do not have agency!
You are a slave the service is the master and the one that exercise agency and control. over your data, engagement everything.
Own your own engagement with such services and roll your own autonomnous interpersonal network that is linked to thoese services but exists independently
switch services
do not use services like that
seek out alternatives that make you the master
indyweb
Why do you need all three?
Need 4
Own the very "services" that come to you to operate on your owned data you make use of.
services authenticate with you do operate on your information for your benefit first
provocation from Rabble
users need control over their' - identity and through that - content - contacts
The reason we had to do something beyond the - server controls everything model of Activity Pub.
AP was good a decade ago, the fediverse is a good thing.
But its architecture us fundamentally limited.
We need new protocols
The minimal definition of user agencyOwn your ID, your content, and your contacts.
xx
Own your contacts
yes
So self-sovereign IDs and keys
The minimal definition of user agencyOwn your ID, your content, and your contacts.
Trustless means “you’re in control”

Jun 20Murmurations Demo Day - Synchronising data across platforms
Synchronising data across platforms Tue, Jun 20 at 6:00PM - 7:00PM CEST
orbit-db/examples/browser/example.js
const creatures = [
'🐙', '🐷', '🐬', '🐞',
'🐈', '🙉', '🐸', '🐓',
'🐊', '🕷', '🐠', '🐘',
'🐼', '🐰', '🐶', '🐥'
]
Desire path

IPNS is transport agnostic
<svg id="mermaid_64a568e0" width="100%" xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink" height="539.5182495117188" style="max-width: 573.4765625px;" viewBox="0 0 573.4765625 539.5182495117188"><style>#mermaid_64a568e0 {font-family:"trebuchet ms",verdana,arial,sans-serif;font-size:16px;fill:#333;}#mermaid_64a568e0 .error-icon{fill:#552222;}#mermaid_64a568e0 .error-text{fill:#552222;stroke:#552222;}#mermaid_64a568e0 .edge-thickness-normal{stroke-width:2px;}#mermaid_64a568e0 .edge-thickness-thick{stroke-width:3.5px;}#mermaid_64a568e0 .edge-pattern-solid{stroke-dasharray:0;}#mermaid_64a568e0 .edge-pattern-dashed{stroke-dasharray:3;}#mermaid_64a568e0 .edge-pattern-dotted{stroke-dasharray:2;}#mermaid_64a568e0 .marker{fill:#333333;stroke:#333333;}#mermaid_64a568e0 .marker.cross{stroke:#333333;}#mermaid_64a568e0 svg{font-family:"trebuchet ms",verdana,arial,sans-serif;font-size:16px;}#mermaid_64a568e0 .label{font-family:"trebuchet ms",verdana,arial,sans-serif;color:#333;}#mermaid_64a568e0 .cluster-label text{fill:#333;}#mermaid_64a568e0 .cluster-label span{color:#333;}#mermaid_64a568e0 .label text,#mermaid_64a568e0 span{fill:#333;color:#333;}#mermaid_64a568e0 .node rect,#mermaid_64a568e0 .node circle,#mermaid_64a568e0 .node ellipse,#mermaid_64a568e0 .node polygon,#mermaid_64a568e0 .node path{fill:#ECECFF;stroke:#9370DB;stroke-width:1px;}#mermaid_64a568e0 .node .label{text-align:center;}#mermaid_64a568e0 .node.clickable{cursor:pointer;}#mermaid_64a568e0 .arrowheadPath{fill:#333333;}#mermaid_64a568e0 .edgePath .path{stroke:#333333;stroke-width:2.0px;}#mermaid_64a568e0 .flowchart-link{stroke:#333333;fill:none;}#mermaid_64a568e0 .edgeLabel{background-color:#e8e8e8;text-align:center;}#mermaid_64a568e0 .edgeLabel rect{opacity:0.5;background-color:#e8e8e8;fill:#e8e8e8;}#mermaid_64a568e0 .cluster rect{fill:#ffffde;stroke:#aaaa33;stroke-width:1px;}#mermaid_64a568e0 .cluster text{fill:#333;}#mermaid_64a568e0 .cluster span{color:#333;}#mermaid_64a568e0 div.mermaidTooltip{position:absolute;text-align:center;max-width:200px;padding:2px;font-family:"trebuchet ms",verdana,arial,sans-serif;font-size:12px;background:hsl(80, 100%, 96.2745098039%);border:1px solid #aaaa33;border-radius:2px;pointer-events:none;z-index:100;}#mermaid_64a568e0 :root{--mermaid-font-family:"trebuchet ms",verdana,arial,sans-serif;}</style><g><g class="output"><g class="clusters"><g class="cluster" id="flowchart-Routing-46" transform="translate(211.79296875,269.7591209411621)" style="opacity: 1;"><rect width="407.5859375" height="523.5182418823242" x="-203.79296875" y="-261.7591209411621"></rect><g class="label" transform="translate(0, -247.75912475585938)" id="mermaid_64a568e0Text"><g transform="translate(-26.8359375,-9.5)"><foreignObject width="53.671875" height="19"><div xmlns="http://www.w3.org/1999/xhtml" style="display: inline-block; white-space: nowrap;">Routing</div></foreignObject></g></g></g><g class="cluster" id="flowchart-Transports-47" transform="translate(208.609375,199.19803619384766)" style="opacity: 1;"><rect width="241.515625" height="116.39607238769531" x="-120.7578125" y="-58.198036193847656"></rect><g class="label" transform="translate(0, -44.198036193847656)" id="mermaid_64a568e0Text"><g transform="translate(-36.9609375,-9.5)"><foreignObject width="73.921875" height="19"><div xmlns="http://www.w3.org/1999/xhtml" style="display: inline-block; white-space: nowrap;">Transports</div></foreignObject></g></g></g></g><g class="edgePaths"><g class="edgePath LS-Resolver LE-Record" id="L-Resolver-Record" style="opacity: 1;"><path class="path" d="M248.39116753472223,365.3960723876953L258.83508752893516,371.1460723876953C269.27900752314815,376.8960723876953,290.1668475115741,388.3960723876953,325.0388695741338,402.73958651224774C359.9108916366936,417.0831006368001,408.76709577338715,434.27012888590497,433.19519784173394,442.86364301045734L457.6232999100808,451.45715713500977" marker-end="url(#arrowhead105)" style="fill:none"></path><defs><marker id="arrowhead105" viewBox="0 0 10 10" refX="9" refY="5" markerUnits="strokeWidth" markerWidth="8" markerHeight="6" orient="auto"><path d="M 0 0 L 10 5 L 0 10 z" class="arrowheadPath" style="stroke-width: 1; stroke-dasharray: 1, 0;"></path></marker></defs></g><g class="edgePath LS-Record LE-Publisher" id="L-Record-Publisher" style="opacity: 1;"><path class="path" d="M470.2385330012058,451.45715713500977L451.3159650010048,442.86364301045734C432.3933970008038,434.27012888590497,394.5482610004019,417.0831006368001,375.62569300020095,399.48958651224774C356.703125,381.8960723876953,356.703125,363.8960723876953,356.703125,345.8960723876953C356.703125,327.8960723876953,356.703125,309.8960723876953,356.703125,295.1460723876953C356.703125,280.3960723876953,356.703125,268.8960723876953,356.703125,253.4463996887207C356.703125,237.9967269897461,356.703125,218.59738159179688,356.703125,199.19803619384766C356.703125,179.79869079589844,356.703125,160.39934539794922,356.703125,144.9496726989746C356.703125,129.5,356.703125,118,340.2890625,105.9859761484099C323.875,93.9719522968198,291.046875,81.44390459363957,274.6328125,75.17988074204948L258.21875,68.91585689045937" marker-end="url(#arrowhead106)" style="fill:none"></path><defs><marker id="arrowhead106" viewBox="0 0 10 10" refX="9" refY="5" markerUnits="strokeWidth" markerWidth="8" markerHeight="6" orient="auto"><path d="M 0 0 L 10 5 L 0 10 z" class="arrowheadPath" style="stroke-width: 1; stroke-dasharray: 1, 0;"></path></marker></defs></g><g class="edgePath LS-Publisher LE-DHT" id="L-Publisher-DHT" style="opacity: 1;"><path class="path" d="M190.80555555555554,72L183.61140046296296,77.75C176.41724537037035,83.5,162.0289351851852,95,154.83478009259258,106.5C147.640625,118,147.640625,129.5,147.640625,139.92474619547525C147.640625,150.34949239095053,147.640625,159.69898478190103,147.640625,164.3737309773763L147.640625,169.04847717285156" marker-end="url(#arrowhead107)" style="fill:none"></path><defs><marker id="arrowhead107" viewBox="0 0 10 10" refX="9" refY="5" markerUnits="strokeWidth" markerWidth="8" markerHeight="6" orient="auto"><path d="M 0 0 L 10 5 L 0 10 z" class="arrowheadPath" style="stroke-width: 1; stroke-dasharray: 1, 0;"></path></marker></defs></g><g class="edgePath LS-DHT LE-Resolver" id="L-DHT-Resolver" style="opacity: 1;"><path class="path" d="M147.640625,229.34759521484375L147.640625,234.022341410319C147.640625,238.69708760579428,147.640625,248.04657999674478,147.640625,258.47132619222003C147.640625,268.8960723876953,147.640625,280.3960723876953,154.59727647569443,291.8960723876953C161.55392795138889,303.3960723876953,175.46723090277774,314.8960723876953,182.4238823784722,320.6460723876953L189.38053385416666,326.3960723876953" marker-end="url(#arrowhead108)" style="fill:none;stroke-width:2px;stroke-dasharray:3;"></path><defs><marker id="arrowhead108" viewBox="0 0 10 10" refX="9" refY="5" markerUnits="strokeWidth" markerWidth="8" markerHeight="6" orient="auto"><path d="M 0 0 L 10 5 L 0 10 z" class="arrowheadPath" style="stroke-width: 1; stroke-dasharray: 1, 0;"></path></marker></defs></g><g class="edgePath LS-Publisher LE-PubSub" id="L-Publisher-PubSub" style="opacity: 1;"><path class="path" d="M230.80143229166666,72L235.4009331597222,77.75C240.00043402777774,83.5,249.19943576388889,95,253.79893663194446,106.5C258.3984375,118,258.3984375,129.5,258.3984375,139.41666666666666C258.3984375,149.33333333333334,258.3984375,157.66666666666666,258.3984375,161.83333333333334L258.3984375,166" marker-end="url(#arrowhead109)" style="fill:none"></path><defs><marker id="arrowhead109" viewBox="0 0 10 10" refX="9" refY="5" markerUnits="strokeWidth" markerWidth="8" markerHeight="6" orient="auto"><path d="M 0 0 L 10 5 L 0 10 z" class="arrowheadPath" style="stroke-width: 1; stroke-dasharray: 1, 0;"></path></marker></defs></g><g class="edgePath LS-PubSub LE-Resolver" id="L-PubSub-Resolver" style="opacity: 1;"><path class="path" d="M258.3984375,232.3960723876953L258.3984375,236.56273905436197C258.3984375,240.72940572102866,258.3984375,249.06273905436197,258.3984375,258.9794057210286C258.3984375,268.8960723876953,258.3984375,280.3960723876953,253.5614330150463,291.8960723876953C248.7244285300926,303.3960723876953,239.0504195601852,314.8960723876953,234.2134150752315,320.6460723876953L229.37641059027777,326.3960723876953" marker-end="url(#arrowhead110)" style="fill:none;stroke-width:2px;stroke-dasharray:3;"></path><defs><marker id="arrowhead110" viewBox="0 0 10 10" refX="9" refY="5" markerUnits="strokeWidth" markerWidth="8" markerHeight="6" orient="auto"><path d="M 0 0 L 10 5 L 0 10 z" class="arrowheadPath" style="stroke-width: 1; stroke-dasharray: 1, 0;"></path></marker></defs></g><g class="edgePath LS-Publisher LE-Local" id="L-Publisher-Local" style="opacity: 1;"><path class="path" d="M172.1875,68.26395737235566L154.79817708333334,74.63663114362971C137.40885416666666,81.00930491490378,102.63020833333333,93.75465245745188,85.24088541666667,105.87732622872595C67.8515625,118,67.8515625,129.5,67.8515625,144.9496726989746C67.8515625,160.39934539794922,67.8515625,179.79869079589844,67.8515625,199.19803619384766C67.8515625,218.59738159179688,67.8515625,237.9967269897461,67.8515625,253.4463996887207C67.8515625,268.8960723876953,67.8515625,280.3960723876953,67.8515625,295.1460723876953C67.8515625,309.8960723876953,67.8515625,327.8960723876953,67.8515625,345.8960723876953C67.8515625,363.8960723876953,67.8515625,381.8960723876953,72.84503344541245,397.06214232989674C77.8385043908249,412.22821227209823,87.82544628164977,424.5603521565011,92.81891722706223,430.7264220987026L97.81238817247467,436.892492040904" marker-end="url(#arrowhead111)" style="fill:none"></path><defs><marker id="arrowhead111" viewBox="0 0 10 10" refX="9" refY="5" markerUnits="strokeWidth" markerWidth="8" markerHeight="6" orient="auto"><path d="M 0 0 L 10 5 L 0 10 z" class="arrowheadPath" style="stroke-width: 1; stroke-dasharray: 1, 0;"></path></marker></defs></g><g class="edgePath LS-Local LE-Resolver" id="L-Local-Resolver" style="opacity: 1;"><path class="path" d="M173.11816333154974,440.39358703437904L180.1323236096248,433.6440012599317C187.14648388769982,426.89441548548444,201.17480444384992,413.39524393658985,207.95146110502682,400.8956581621426C214.7281177662037,388.3960723876953,214.2531105324074,376.8960723876953,214.01560691550924,371.1460723876953L213.77810329861111,365.3960723876953" marker-end="url(#arrowhead112)" style="fill:none;stroke-width:2px;stroke-dasharray:3;"></path><defs><marker id="arrowhead112" viewBox="0 0 10 10" refX="9" refY="5" markerUnits="strokeWidth" markerWidth="8" markerHeight="6" orient="auto"><path d="M 0 0 L 10 5 L 0 10 z" class="arrowheadPath" style="stroke-width: 1; stroke-dasharray: 1, 0;"></path></marker></defs></g><g class="edgePath LS-Resolver LE-Local" id="L-Resolver-Local" style="opacity: 1;"><path class="path" d="M176.78396267361111,365.3960723876953L166.11293764467592,371.1460723876953C155.44191261574073,376.8960723876953,134.09986255787035,388.3960723876953,124.76291266963916,399.9226045635624C115.42596278140799,411.44913673942955,118.09411306281599,423.0022010911637,119.42818820351998,428.7787332670309L120.76226334422397,434.5552654428979" marker-end="url(#arrowhead113)" style="fill:none"></path><defs><marker id="arrowhead113" viewBox="0 0 10 10" refX="9" refY="5" markerUnits="strokeWidth" markerWidth="8" markerHeight="6" orient="auto"><path d="M 0 0 L 10 5 L 0 10 z" class="arrowheadPath" style="stroke-width: 1; stroke-dasharray: 1, 0;"></path></marker></defs></g></g><g class="edgeLabels"><g class="edgeLabel" transform="translate(311.0546875,399.8960723876953)" style="opacity: 1;"><g transform="translate(-25.6484375,-9.5)" class="label"><rect rx="0" ry="0" width="51.296875" height="19"></rect><foreignObject width="51.296875" height="19"><div xmlns="http://www.w3.org/1999/xhtml" style="display: inline-block; white-space: nowrap;"><span id="L-L-Resolver-Record" class="edgeLabel L-LS-Resolver' L-LE-Record">resolve</span></div></foreignObject></g></g><g class="edgeLabel" transform="translate(356.703125,291.8960723876953)" style="opacity: 1;"><g transform="translate(-38.8828125,-9.5)" class="label"><rect rx="0" ry="0" width="77.765625" height="19"></rect><foreignObject width="77.765625" height="19"><div xmlns="http://www.w3.org/1999/xhtml" style="display: inline-block; white-space: nowrap;"><span id="L-L-Record-Publisher" class="edgeLabel L-LS-Record' L-LE-Publisher">(re)publish</span></div></foreignObject></g></g><g class="edgeLabel" transform="translate(147.640625,106.5)" style="opacity: 1;"><g transform="translate(-14.296875,-9.5)" class="label"><rect rx="0" ry="0" width="28.59375" height="19"></rect><foreignObject width="28.59375" height="19"><div xmlns="http://www.w3.org/1999/xhtml" style="display: inline-block; white-space: nowrap;"><span id="L-L-Publisher-DHT" class="edgeLabel L-LS-Publisher' L-LE-DHT">PUT</span></div></foreignObject></g></g><g class="edgeLabel" transform="translate(147.640625,291.8960723876953)" style="opacity: 1;"><g transform="translate(-14.34375,-9.5)" class="label"><rect rx="0" ry="0" width="28.6875" height="19"></rect><foreignObject width="28.6875" height="19"><div xmlns="http://www.w3.org/1999/xhtml" style="display: inline-block; white-space: nowrap;"><span id="L-L-DHT-Resolver" class="edgeLabel L-LS-DHT' L-LE-Resolver">GET</span></div></foreignObject></g></g><g class="edgeLabel" transform="translate(258.3984375,106.5)" style="opacity: 1;"><g transform="translate(-14.296875,-9.5)" class="label"><rect rx="0" ry="0" width="28.59375" height="19"></rect><foreignObject width="28.59375" height="19"><div xmlns="http://www.w3.org/1999/xhtml" style="display: inline-block; white-space: nowrap;"><span id="L-L-Publisher-PubSub" class="edgeLabel L-LS-Publisher' L-LE-PubSub">PUT</span></div></foreignObject></g></g><g class="edgeLabel" transform="translate(258.3984375,291.8960723876953)" style="opacity: 1;"><g transform="translate(-14.34375,-9.5)" class="label"><rect rx="0" ry="0" width="28.6875" height="19"></rect><foreignObject width="28.6875" height="19"><div xmlns="http://www.w3.org/1999/xhtml" style="display: inline-block; white-space: nowrap;"><span id="L-L-PubSub-Resolver" class="edgeLabel L-LS-PubSub' L-LE-Resolver">GET</span></div></foreignObject></g></g><g class="edgeLabel" transform="translate(67.8515625,291.8960723876953)" style="opacity: 1;"><g transform="translate(-21.6875,-9.5)" class="label"><rect rx="0" ry="0" width="43.375" height="19"></rect><foreignObject width="43.375" height="19"><div xmlns="http://www.w3.org/1999/xhtml" style="display: inline-block; white-space: nowrap;"><span id="L-L-Publisher-Local" class="edgeLabel L-LS-Publisher' L-LE-Local">Cache</span></div></foreignObject></g></g><g class="edgeLabel" transform="translate(215.203125,399.8960723876953)" style="opacity: 1;"><g transform="translate(-14.34375,-9.5)" class="label"><rect rx="0" ry="0" width="28.6875" height="19"></rect><foreignObject width="28.6875" height="19"><div xmlns="http://www.w3.org/1999/xhtml" style="display: inline-block; white-space: nowrap;"><span id="L-L-Local-Resolver" class="edgeLabel L-LS-Local' L-LE-Resolver">GET</span></div></foreignObject></g></g><g class="edgeLabel" transform="translate(112.7578125,399.8960723876953)" style="opacity: 1;"><g transform="translate(-21.6875,-9.5)" class="label"><rect rx="0" ry="0" width="43.375" height="19"></rect><foreignObject width="43.375" height="19"><div xmlns="http://www.w3.org/1999/xhtml" style="display: inline-block; white-space: nowrap;"><span id="L-L-Resolver-Local" class="edgeLabel L-LS-Resolver' L-LE-Local">Cache</span></div></foreignObject></g></g></g><g class="nodes"><g class="node default" id="flowchart-Publisher-28" transform="translate(215.203125,52.5)" style="opacity: 1;"><rect rx="0" ry="0" x="-43.015625" y="-19.5" width="86.03125" height="39" class="label-container"></rect><g class="label" transform="translate(0,0)"><g transform="translate(-33.015625,-9.5)"><foreignObject width="66.03125" height="19"><div xmlns="http://www.w3.org/1999/xhtml" style="display: inline-block; white-space: nowrap;">Publisher</div></foreignObject></g></g></g><g class="node default" id="flowchart-Resolver-29" transform="translate(212.97265625,345.8960723876953)" style="opacity: 1;"><rect rx="0" ry="0" x="-39.9765625" y="-19.5" width="79.953125" height="39" class="label-container"></rect><g class="label" transform="translate(0,0)"><g transform="translate(-29.9765625,-9.5)"><foreignObject width="59.953125" height="19"><div xmlns="http://www.w3.org/1999/xhtml" style="display: inline-block; white-space: nowrap;">Resolver</div></foreignObject></g></g></g><g class="node default" id="flowchart-Local-30" label-offset-y="11.043265875785066" transform="translate(129.12890625,470.45715713500977)" style="opacity: 1;"><path d="M 0,11.043265875785066 a 49.453125,11.043265875785066 0,0,0 98.90625 0 a 49.453125,11.043265875785066 0,0,0 -98.90625 0 l 0,50.04326587578507 a 49.453125,11.043265875785066 0,0,0 98.90625 0 l 0,-50.04326587578507" transform="translate(-49.453125,-36.0648988136776)" class="label-container"></path><g class="label" transform="translate(0,0)"><g transform="translate(-39.453125,-9.5)"><foreignObject width="78.90625" height="19"><div xmlns="http://www.w3.org/1999/xhtml" style="display: inline-block; white-space: nowrap;">Local store</div></foreignObject></g></g></g><g class="node default" id="flowchart-PubSub-31" label-offset-y="9.132021580450651" transform="translate(258.3984375,199.19803619384766)" style="opacity: 1;"><path d="M 0,9.132021580450651 a 35.96875,9.132021580450651 0,0,0 71.9375 0 a 35.96875,9.132021580450651 0,0,0 -71.9375 0 l 0,48.132021580450655 a 35.96875,9.132021580450651 0,0,0 71.9375 0 l 0,-48.132021580450655" transform="translate(-35.96875,-33.198032370675975)" class="label-container"></path><g class="label" transform="translate(0,0)"><g transform="translate(-25.96875,-9.5)"><foreignObject width="51.9375" height="19"><div xmlns="http://www.w3.org/1999/xhtml" style="display: inline-block; white-space: nowrap;">PubSub</div></foreignObject></g></g></g><g class="node default" id="flowchart-DHT-32" label-offset-y="7.099704645126645" transform="translate(147.640625,199.19803619384766)" style="opacity: 1;"><path d="M 0,7.099704645126645 a 24.7890625,7.099704645126645 0,0,0 49.578125 0 a 24.7890625,7.099704645126645 0,0,0 -49.578125 0 l 0,46.09970464512664 a 24.7890625,7.099704645126645 0,0,0 49.578125 0 l 0,-46.09970464512664" transform="translate(-24.7890625,-30.149556967689968)" class="label-container"></path><g class="label" transform="translate(0,0)"><g transform="translate(-14.7890625,-9.5)"><foreignObject width="29.578125" height="19"><div xmlns="http://www.w3.org/1999/xhtml" style="display: inline-block; white-space: nowrap;">DHT</div></foreignObject></g></g></g><g class="node default" id="flowchart-Record-27" transform="translate(512.90625,470.45715713500977)" style="opacity: 1;"><polygon points="-19.5,0 105.140625,0 105.140625,-39 -19.5,-39 0,-19.5" transform="translate(-52.5703125,19.5)" class="label-container"></polygon><g class="label" transform="translate(0,0)"><g transform="translate(-42.5703125,-9.5)"><foreignObject width="85.140625" height="19"><div xmlns="http://www.w3.org/1999/xhtml" style="display: inline-block; white-space: nowrap;">IPNS Record</div></foreignObject></g></g></g></g></g></g></svg>
Shows how to import an entire module as an object
import an entire module as an object
function x () {} function y () export {x, y}
import * as modob from
taht is revealing pattern
module-aggregation: Shows how sub module features can be aggregated into a parent module using export { x } from 'y.js' syntax (run the example live).
aggregate - sub module features
into : parent module
using - export { x } from 'y.js' syntax

dynamic-module-imports
dynamic module loading - using import().then()
JavaScript module examples
web - know how
from : https://hyp.is/E_zfsPsfEe21VdOOA7_T4Q/developer.mozilla.org/en-US/docs/Web/JavaScript/Guide/Modules
created a simple set of examples
examples
from https://hyp.is/g1FQaPseEe2bRz_dJ4UfAQ/github.com/orbitdb/orbit-db/blob/main/CHANGELOG.md

v0.29.0
orbitdb

updated OrbitDB and all of its modules to use ESM, JavaScript Modules
use ESM Javacript Modules
collect the hashes of the entries and pin them outside of the db.put/add
collect hashes and pin them
No results found for "ambient web intents".
images for the edge of knowledge

search : images for the edge of knowledge

developing human-centric solutions
How to Add Hypothesis to Your Website
x
for - embed hypothesis
DAOs
single reference
The Dawn of Decentralized Organizational Identity, Part 1: Identifiers

Legal Entity Identifier Services by GLEIF
The age of Super AppsAs more and more companies jump on the super app bandwagon, the competition is only going to get tougher

Diamine Ancient Copper fountain pen ink

goals of a pactum are comfort and survival
comfort and survival
Memetic Body by Contract
memetic bidy by contract
Memetics is a constant process
process indeed
Memetics argues that these principles can apply to ideas
There is more to ideas then blind selfish genes
intent/purpose
gestalt superorganism
MemeticEngines

Symmathetic Heuristic Serendipity Engine
Learn more about a web pageYou can find more information about the source and topic of a web page in the “Source” section of the “About this result” panel. Important: This feature is only available in some regions.
interesting

Constraint satisfaction problems: Algorithms and applicationsBarbara Smith

Web Authentication:An API for accessing Public Key CredentialsLevel 3
This is a minimal workable way of revieing past research
annotating the annotation search results and linking them to where they are relevant
When you decouple the network itself from the service you use to view and/or host it, then there’s suddenly a market with near perfect competition.
decouple the network from the service
flip that
bootstrapp kernel level constellations for - interplanetary, - evergreen, - interpersonal social media - to enable 1000 homebrew<br /> - long tail services to blooom
and complete them and any other other even centralized social media with - evergreen - autonomous - interpersonal<br /> - overweb - eventually gobal, interplanetary really, - interpersonal - autonomous social networks to any service
a functional PoC,
link
Update (April 2020): after implementing a functional PoC, I put this down to work on Gather, and make sure the Metaverse is built with these principles in mind.
to gather
from https://hyp.is/G1FnfvlWEe2zVHOCg8d__Q/github.com/npfoss/gravity-protocol
A Decentralized Secure Social Network1amsArthur WillKifle Woldu,iffer,May 2019Nate Foss, Matthew PfeContents phonesNP ele8 ek
3 minute answer: The Case for a Decentralized Social Network
case
software is made of bugs.
made of bugs
This repo is a sample implementation of the protocol underlying the Gravity social network.
Since it's open and decentralized, anyone can participate; you don't need to go through gravitynet.io or even use this code to do so.
Beware
from : https://hyp.is/qKYTtPlVEe2Y29sdSa9R2g/github.com/npfoss/gravity