gradually enhancing a document into a software application
The idea of - gradually enhancing a document - into a software application is not new.
It’s related to document-based - productivity tools

gradually enhancing a document into a software application
The idea of - gradually enhancing a document - into a software application is not new.
It’s related to document-based - productivity tools

existence of the match, of the shared interests.
gist
Interest based social networks
Now in the works replacing Google+ forging the IndyVerse
Social Media Potential For Building Meaningful Connections

Current social media platforms are largely unfit for creating meaningful connections online
Find the Other create connection s that are - meaningful - (a)live for You, always - autonomous - private - secure - based on trust for trust, but verify - evergreen/permanent
With IPFS the entire World Wide Web can be considered as one torrent file that everyone shares
One torrent file that everyone shares
Here are the benefits that the web 2.0 cannot compete with
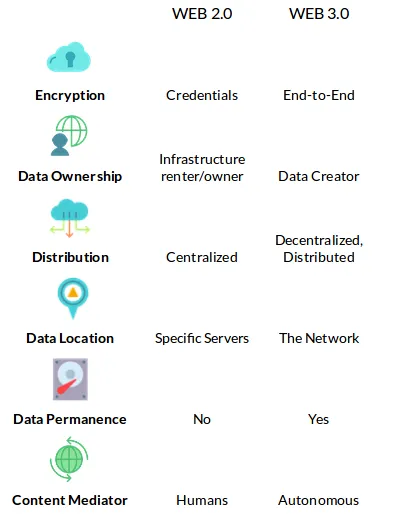
How IPFS is Challenging the Web as We Know It

How IPFS is Challenging the Web as We Know It - Medium
Is IPFS a blockchain?Quorahttps://www.quora.com › Is-IPFS-a-blockchainQuorahttps://www.quora.com › Is-IPFS-a-blockchainAug 23, 2019 — While blockchain shares a ledger with its nodes, IPFS is a peer to peer file-sharing system that hashes files (similar to the way blockchain hashes transactions) ...6 answers · 4 votes: TL;DR No IPFS is actually a network protocol that aims to replace the curren
google - search - Is IPFS a blockchain?
Although it uses similar architectural elements - like Merkle Trees,
IPFS is not built on Blockchain but rather is - designed to work together with existing Blockchain protocols.
As mentioned in the misconceptions above, - each file uploaded to IPFS will get a permanent address.
IPFS gives you the abiity to create contentchains and with IPLD allows you to link them together to suite your intent and purpose
it gives you instasnt global permanent consensus if you like
the more participants the better the network is
Reimagining peer-review.
“I see!” said a voice at the back of the hall, breaking the silence. “You are trying to articulate, in language that only philosophers can understand, intuitions that only computer scientists can have.” Still haunting, thirty years later. But it is time for change.
articulate in language philosophers can understand
intuitions only computer scientist can have
hackers
age of significance
How Judaism and Christianity were INVENTED - Jason Reza Jorjani PhD
source - https://www.youtube.com/watch?v=FOfNrwBWh_8
.png)
20,756 views Sep 23, 2019 Thoughts on Functional Programming Season 2 What happens when your language is so powerful that small, independent teams can solve their problems without libraries? Does everyone flock to it? Or do you just get a lack of libraries?
►► Audio, Video, and Transcript available: https://lispcast.com/what-is-the-curs... ►► Subscribe on iTunes: https://itunes.apple.com/us/podcast/t...

How to build tree-shakeable JavaScript librariesSeptember 13, 2022Best PracticesDan OnoshkoOpen Source Ecosystem Engineer at Cube
4 - web know how
Rollup performs
Rollup performs - tree-shaking and - dead code elimination
on its own.)
tree-shaking is a later term
tree-shaking is a later term that is - only relevant if JavaScript bundlers and - ES6 imports/exports are used.
analyse a potential power triangle between three kinds of mutuallydependent, mutually threatening and co-evolving cognitive systems
analyse a potential power triangle between three kinds of mutually dependent, mutually threatening and co-evolving cognitive systems—the human being, the social system and the emerging synthetic intelligence. The question we address is what configuration between these powers would enable humans to start governing the global socio-econo-political system, rather than being governed by it?
‘Semiocene,’ rather than the Anthropocene, would do it more justice
bad idea
goal-oriented approach to the design of AI systems
x
 // The Intentional Integral Interpersonal InterPlanetary Evergreen co-evolutionay human trust based
// The Intentional Integral Interpersonal InterPlanetary Evergreen co-evolutionay human trust based
// Kernel for the IndyVerse/Net/Web/Lab we are developing provides the - info structuring - Personal First, interpersonal - com - munication - putation - position - al Open, commons-based, peer-produced, constellations for co-evolving, co-creating bootstrapping in collaborations across self-organizing organically emergent Networked Improvement Communities to augmenting all three cognitive systems
By autonomously and critically linking to collective externalization/manifestation of human inter-intellect to establish a "Human Takeover" of the control of the - emergent man-machine symbiosys
"scaling synthesis" and - promoting human autonomyand thriving by - scaling autonomous reach in the long tail of the internet, - not just decentralized but - human centered, interpersonal intercollective reach powered
not onlylimiting the scope and power of the 'programming' inherent in the very concept of intelligence but humanizing the machine processes by creating the conditions for the manifestation for synthetic intellect that emreges from augmented caling synthesis of machine suppoted symmathetic human interintellect
the human mind, social systemsand the emerging synthetic intelligence
 // The Intentional Integral Interpersonal InterPlanetary Evergreen co-evolutionay human trust based
// The Intentional Integral Interpersonal InterPlanetary Evergreen co-evolutionay human trust based
// Kernel for the IndyVerse/Net/Web/Lab we are developing provides the - info structuring - Personal First, interpersonal - com - munication - putation - position - al Open, commons-based, peer-produced, constellations for co-evolving, co-creating bootstrapping in collaborations across self-organizing organically emergent Networked Improvement Communities to augmenting all three cognitive systems
By autonomously and critically linking to collective externalization/manifestation of human inter-intellect to establish a "Human Takeover" of the control of the - emergent man-machine symbiosys
"scaling synthesis" and - promoting human autonomyand thriving by - scaling autonomous reach in the long tail of the internet, - not just decentralized but - human centered, interpersonal intercollective reach powered
not onlylimiting the scope and power of the 'programming' inherent in the very concept of intelligence but humanizing the machine processes by creating the conditions for the manifestation for synthetic intellect that emreges from augmented caling synthesis of machine suppoted symmathetic human interintellect
The Human Takeover: A Call for a Venture into anExistential Opportunity
<svg width="480" height="480" version="1.1" xmlns="http://www.w3.org/2000/svg"><g></g><g transform="translate(240,300)scale(0.6033445358276367,1.0033445358276367)"><text text-anchor="middle" transform="translate(-215,67)rotate(59.99999999999999)" style="font-size: 10px; font-family: Impact; fill: rgb(206, 109, 189);">think</text><text text-anchor="middle" transform="translate(217,104)rotate(-59.99999999999999)" style="font-size: 10px; font-family: Impact; fill: rgb(206, 219, 156);">available</text><text text-anchor="middle" transform="translate(-75,88)rotate(-29.999999999999993)" style="font-size: 10px; font-family: Impact; fill: rgb(206, 109, 189);">final</text><text text-anchor="middle" transform="translate(196,-95)rotate(59.99999999999999)" style="font-size: 10px; font-family: Impact; fill: rgb(107, 110, 207);">development</text><text text-anchor="middle" transform="translate(-60,2)" style="font-size: 10px; font-family: Impact; fill: rgb(123, 65, 115);">one</text><text text-anchor="middle" transform="translate(63,-265)rotate(-29.999999999999993)" style="font-size: 10px; font-family: Impact; fill: rgb(165, 81, 148);">along</text><text text-anchor="middle" transform="translate(-155,-244)rotate(-59.99999999999999)" style="font-size: 10px; font-family: Impact; fill: rgb(231, 203, 148);">instead</text><text text-anchor="middle" transform="translate(-55,-214)" style="font-size: 10px; font-family: Impact; fill: rgb(123, 65, 115);">many</text><text text-anchor="middle" transform="translate(336,96)rotate(29.999999999999993)" style="font-size: 10px; font-family: Impact; fill: rgb(140, 162, 82);">Thus</text><text text-anchor="middle" transform="translate(-196,-111)rotate(-59.99999999999999)" style="font-size: 10px; font-family: Impact; fill: rgb(57, 59, 121);"></text><text text-anchor="middle" transform="translate(-76,-102)rotate(0)" style="font-size: 100px; font-family: Impact; fill: rgb(107, 110, 207);">Opportunity</text><text text-anchor="middle" transform="translate(8,-8)rotate(0)" style="font-size: 100px; font-family: Impact; fill: rgb(156, 158, 222);">Human</text><text text-anchor="middle" transform="translate(218,-85)rotate(60)" style="font-size: 92px; font-family: Impact; fill: rgb(99, 121, 57);">Existential</text><text text-anchor="middle" transform="translate(133,69)rotate(-30)" style="font-size: 74px; font-family: Impact; fill: rgb(140, 162, 82);">world</text><text text-anchor="middle" transform="translate(-219,-20)rotate(-30)" style="font-size: 60px; font-family: Impact; fill: rgb(181, 207, 107);">Venture</text><text text-anchor="middle" transform="translate(-349,60)rotate(60)" style="font-size: 60px; font-family: Impact; fill: rgb(206, 219, 156);">Artificial</text><text text-anchor="middle" transform="translate(193,-68)rotate(-30)" style="font-size: 42px; font-family: Impact; fill: rgb(140, 109, 49);">1</text><text text-anchor="middle" transform="translate(95,-219)rotate(60)" style="font-size: 42px; font-family: Impact; fill: rgb(189, 158, 57);">good</text><text text-anchor="middle" transform="translate(-23,-178)rotate(0)" style="font-size: 42px; font-family: Impact; fill: rgb(231, 186, 82);">enough</text><text text-anchor="middle" transform="translate(-119,81)rotate(-30)" style="font-size: 42px; font-family: Impact; fill: rgb(231, 203, 148);">transition</text><text text-anchor="middle" transform="translate(-359,-113)rotate(60)" style="font-size: 42px; font-family: Impact; fill: rgb(132, 60, 57);">mediating</text><text text-anchor="middle" transform="translate(-36,96)rotate(-60)" style="font-size: 42px; font-family: Impact; fill: rgb(173, 73, 74);">Information</text><text text-anchor="middle" transform="translate(-216,-220)rotate(30)" style="font-size: 42px; font-family: Impact; fill: rgb(214, 97, 107);">distributed</text><text text-anchor="middle" transform="translate(224,36)rotate(60)" style="font-size: 42px; font-family: Impact; fill: rgb(231, 150, 156);">governance</text><text text-anchor="middle" transform="translate(8,103)rotate(60)" style="font-size: 42px; font-family: Impact; fill: rgb(123, 65, 115);">must</text><text text-anchor="middle" transform="translate(59,39)rotate(-30)" style="font-size: 42px; font-family: Impact; fill: rgb(165, 81, 148);">just</text><text text-anchor="middle" transform="translate(-167,29)rotate(0)" style="font-size: 42px; font-family: Impact; fill: rgb(206, 109, 189);">cognitive</text><text text-anchor="middle" transform="translate(-10,155)rotate(60)" style="font-size: 42px; font-family: Impact; fill: rgb(222, 158, 214);">social</text><text text-anchor="middle" transform="translate(168,98)rotate(-30)" style="font-size: 42px; font-family: Impact; fill: rgb(57, 59, 121);">systems</text><text text-anchor="middle" transform="translate(152,205)rotate(-30)" style="font-size: 42px; font-family: Impact; fill: rgb(82, 84, 163);">global</text><text text-anchor="middle" transform="translate(74,-207)rotate(-60)" style="font-size: 42px; font-family: Impact; fill: rgb(107, 110, 207);">AI</text><text text-anchor="middle" transform="translate(322,177)rotate(-30)" style="font-size: 42px; font-family: Impact; fill: rgb(156, 158, 222);">Takeover</text><text text-anchor="middle" transform="translate(69,174)rotate(0)" style="font-size: 42px; font-family: Impact; fill: rgb(99, 121, 57);">Call</text><text text-anchor="middle" transform="translate(-191,195)rotate(30)" style="font-size: 42px; font-family: Impact; fill: rgb(140, 162, 82);">dominate</text><text text-anchor="middle" transform="translate(193,-126)rotate(-30)" style="font-size: 10px; font-family: Impact; fill: rgb(181, 207, 107);">9</text><text text-anchor="middle" transform="translate(258,9)rotate(-60)" style="font-size: 10px; font-family: Impact; fill: rgb(206, 219, 156);">113</text><text text-anchor="middle" transform="translate(-41,133)rotate(-30)" style="font-size: 10px; font-family: Impact; fill: rgb(140, 109, 49);">2018</text><text text-anchor="middle" transform="translate(-94,103)rotate(0)" style="font-size: 10px; font-family: Impact; fill: rgb(189, 158, 57);">Abstract</text><text text-anchor="middle" transform="translate(286,-127)rotate(0)" style="font-size: 10px; font-family: Impact; fill: rgb(231, 186, 82);">propose</text><text text-anchor="middle" transform="translate(-87,-215)rotate(-30)" style="font-size: 10px; font-family: Impact; fill: rgb(231, 203, 148);">establishing</text><text text-anchor="middle" transform="translate(226,112)rotate(-60)" style="font-size: 10px; font-family: Impact; fill: rgb(132, 60, 57);">humans</text><text text-anchor="middle" transform="translate(174,-131)rotate(60)" style="font-size: 10px; font-family: Impact; fill: rgb(173, 73, 74);">live</text><text text-anchor="middle" transform="translate(108,9)rotate(0)" style="font-size: 10px; font-family: Impact; fill: rgb(214, 97, 107);">Defining</text><text text-anchor="middle" transform="translate(-69,-86)rotate(30)" style="font-size: 10px; font-family: Impact; fill: rgb(231, 150, 156);">converse</text><text text-anchor="middle" transform="translate(-8,-85)rotate(-30)" style="font-size: 10px; font-family: Impact; fill: rgb(123, 65, 115);">riskthat</text><text text-anchor="middle" transform="translate(79,125)rotate(-60)" style="font-size: 10px; font-family: Impact; fill: rgb(165, 81, 148);">promises</text><text text-anchor="middle" transform="translate(-284,-67)rotate(60)" style="font-size: 10px; font-family: Impact; fill: rgb(206, 109, 189);">dramatically</text><text text-anchor="middle" transform="translate(167,-89)rotate(-60)" style="font-size: 10px; font-family: Impact; fill: rgb(222, 158, 214);">improve</text><text text-anchor="middle" transform="translate(-41,11)rotate(60)" style="font-size: 10px; font-family: Impact; fill: rgb(57, 59, 121);">future</text><text text-anchor="middle" transform="translate(-33,164)rotate(30)" style="font-size: 10px; font-family: Impact; fill: rgb(82, 84, 163);">humanitywe</text><text text-anchor="middle" transform="translate(124,150)rotate(-30)" style="font-size: 10px; font-family: Impact; fill: rgb(107, 110, 207);">argue</text><text text-anchor="middle" transform="translate(170,-57)rotate(-60)" style="font-size: 10px; font-family: Impact; fill: rgb(156, 158, 222);">explored</text><text text-anchor="middle" transform="translate(-220,-86)rotate(60)" style="font-size: 10px; font-family: Impact; fill: rgb(99, 121, 57);">now</text><text text-anchor="middle" transform="translate(122,-78)rotate(0)" style="font-size: 10px; font-family: Impact; fill: rgb(140, 162, 82);">resides</text><text text-anchor="middle" transform="translate(238,-20)rotate(30)" style="font-size: 10px; font-family: Impact; fill: rgb(181, 207, 107);">moment</text><text text-anchor="middle" transform="translate(91,-90)rotate(0)" style="font-size: 10px; font-family: Impact; fill: rgb(206, 219, 156);">Internetfrom</text><text text-anchor="middle" transform="translate(241,121)rotate(0)" style="font-size: 10px; font-family: Impact; fill: rgb(140, 109, 49);">direct</text><text text-anchor="middle" transform="translate(44,-88)rotate(30)" style="font-size: 10px; font-family: Impact; fill: rgb(189, 158, 57);">sense</text><text text-anchor="middle" transform="translate(-200,53)rotate(30)" style="font-size: 10px; font-family: Impact; fill: rgb(231, 186, 82);">selforganization</text><text text-anchor="middle" transform="translate(-158,55)rotate(0)" style="font-size: 10px; font-family: Impact; fill: rgb(231, 203, 148);">Internet</text><text text-anchor="middle" transform="translate(304,-77)rotate(60)" style="font-size: 10px; font-family: Impact; fill: rgb(132, 60, 57);">tomorrow</text><text text-anchor="middle" transform="translate(357,-51)rotate(0)" style="font-size: 10px; font-family: Impact; fill: rgb(173, 73, 74);">mediate</text><text text-anchor="middle" transform="translate(-71,67)rotate(-30)" style="font-size: 10px; font-family: Impact; fill: rgb(214, 97, 107);">execution</text><text text-anchor="middle" transform="translate(261,-159)rotate(60)" style="font-size: 10px; font-family: Impact; fill: rgb(231, 150, 156);">contracts</text><text text-anchor="middle" transform="translate(-224,-185)rotate(-30)" style="font-size: 10px; font-family: Impact; fill: rgb(123, 65, 115);">transactions</text><text text-anchor="middle" transform="translate(213,-51)rotate(60)" style="font-size: 10px; font-family: Impact; fill: rgb(165, 81, 148);">public</text><text text-anchor="middle" transform="translate(378,-8)rotate(-60)" style="font-size: 10px; font-family: Impact; fill: rgb(206, 109, 189);">interventions</text><text text-anchor="middle" transform="translate(34,205)rotate(-30)" style="font-size: 10px; font-family: Impact; fill: rgb(222, 158, 214);">changeestablishing</text><text text-anchor="middle" transform="translate(-153,-21)rotate(30)" style="font-size: 10px; font-family: Impact; fill: rgb(57, 59, 121);">events</text><text text-anchor="middle" transform="translate(154,144)rotate(30)" style="font-size: 10px; font-family: Impact; fill: rgb(82, 84, 163);">reliably</text><text text-anchor="middle" transform="translate(-187,-7)rotate(0)" style="font-size: 10px; font-family: Impact; fill: rgb(107, 110, 207);">synergistically</text><text text-anchor="middle" transform="translate(311,102)rotate(30)" style="font-size: 10px; font-family: Impact; fill: rgb(156, 158, 222);">technology</text><text text-anchor="middle" transform="translate(263,133)rotate(0)" style="font-size: 10px; font-family: Impact; fill: rgb(99, 121, 57);">institution</text><text text-anchor="middle" transform="translate(-17,191)rotate(30)" style="font-size: 10px; font-family: Impact; fill: rgb(140, 162, 82);">become</text><text text-anchor="middle" transform="translate(-206,89)rotate(-30)" style="font-size: 10px; font-family: Impact; fill: rgb(181, 207, 107);">synthetically</text><text text-anchor="middle" transform="translate(-235,71)rotate(-60)" style="font-size: 10px; font-family: Impact; fill: rgb(206, 219, 156);">intelligent</text><text text-anchor="middle" transform="translate(-233,-72)rotate(-30)" style="font-size: 10px; font-family: Impact; fill: rgb(140, 109, 49);">agent</text><text text-anchor="middle" transform="translate(309,131)rotate(-60)" style="font-size: 10px; font-family: Impact; fill: rgb(189, 158, 57);">observed</text><text text-anchor="middle" transform="translate(-121,-90)rotate(0)" style="font-size: 10px; font-family: Impact; fill: rgb(231, 186, 82);">exploited</text><text text-anchor="middle" transform="translate(261,-213)rotate(-60)" style="font-size: 10px; font-family: Impact; fill: rgb(231, 203, 148);">instrumentally</text><text text-anchor="middle" transform="translate(15,51)rotate(60)" style="font-size: 10px; font-family: Impact; fill: rgb(132, 60, 57);">ventured</text><text text-anchor="middle" transform="translate(-41,-89)rotate(0)" style="font-size: 10px; font-family: Impact; fill: rgb(173, 73, 74);">seized</text><text text-anchor="middle" transform="translate(-113,124)rotate(30)" style="font-size: 10px; font-family: Impact; fill: rgb(214, 97, 107);">behalf</text><text text-anchor="middle" transform="translate(86,-77)rotate(0)" style="font-size: 10px; font-family: Impact; fill: rgb(231, 150, 156);">entire</text><text text-anchor="middle" transform="translate(-172,-32)rotate(-30)" style="font-size: 10px; font-family: Impact; fill: rgb(123, 65, 115);">humanity</text><text text-anchor="middle" transform="translate(-34,-219)rotate(30)" style="font-size: 10px; font-family: Impact; fill: rgb(165, 81, 148);">envision</text><text text-anchor="middle" transform="translate(275,48)rotate(60)" style="font-size: 10px; font-family: Impact; fill: rgb(206, 109, 189);">configuration</text><text text-anchor="middle" transform="translate(-241,-83)rotate(-30)" style="font-size: 10px; font-family: Impact; fill: rgb(222, 158, 214);">three</text><text text-anchor="middle" transform="translate(114,174)rotate(60)" style="font-size: 10px; font-family: Impact; fill: rgb(57, 59, 121);">kinds</text><text text-anchor="middle" transform="translate(20,-231)rotate(0)" style="font-size: 10px; font-family: Impact; fill: rgb(82, 84, 163);">systemthe</text><text text-anchor="middle" transform="translate(-103,-179)rotate(-60)" style="font-size: 10px; font-family: Impact; fill: rgb(107, 110, 207);">mind</text><text text-anchor="middle" transform="translate(292,-171)rotate(-30)" style="font-size: 10px; font-family: Impact; fill: rgb(156, 158, 222);">emerging</text><text text-anchor="middle" transform="translate(243,179)rotate(-30)" style="font-size: 10px; font-family: Impact; fill: rgb(99, 121, 57);">synthetic</text><text text-anchor="middle" transform="translate(-58,-236)rotate(0)" style="font-size: 10px; font-family: Impact; fill: rgb(140, 162, 82);">intelligenceserving</text><text text-anchor="middle" transform="translate(305,-140)rotate(60)" style="font-size: 10px; font-family: Impact; fill: rgb(181, 207, 107);">augment</text><text text-anchor="middle" transform="translate(348,-62)rotate(0)" style="font-size: 10px; font-family: Impact; fill: rgb(206, 219, 156);">autonomy</text><text text-anchor="middle" transform="translate(-145,42)rotate(30)" style="font-size: 10px; font-family: Impact; fill: rgb(140, 109, 49);">first</text><text text-anchor="middle" transform="translate(-127,157)rotate(-30)" style="font-size: 10px; font-family: Impact; fill: rgb(189, 158, 57);">programming</text><text text-anchor="middle" transform="translate(-58,174)rotate(60)" style="font-size: 10px; font-family: Impact; fill: rgb(231, 186, 82);">imposed</text><text text-anchor="middle" transform="translate(206,99)rotate(-60)" style="font-size: 10px; font-family: Impact; fill: rgb(231, 203, 148);">second</text><text text-anchor="middle" transform="translate(354,-97)rotate(30)" style="font-size: 10px; font-family: Impact; fill: rgb(132, 60, 57);">proposition</text><text text-anchor="middle" transform="translate(-365,-65)rotate(-30)" style="font-size: 10px; font-family: Impact; fill: rgb(173, 73, 74);">grounded</text><text text-anchor="middle" transform="translate(304,-106)rotate(0)" style="font-size: 10px; font-family: Impact; fill: rgb(214, 97, 107);">detailed</text><text text-anchor="middle" transform="translate(355,-82)rotate(30)" style="font-size: 10px; font-family: Impact; fill: rgb(231, 150, 156);">analysis</text><text text-anchor="middle" transform="translate(-261,-66)rotate(60)" style="font-size: 10px; font-family: Impact; fill: rgb(123, 65, 115);">manner</text><text text-anchor="middle" transform="translate(-311,-194)rotate(-60)" style="font-size: 10px; font-family: Impact; fill: rgb(165, 81, 148);">socioeconopolitical</text><text text-anchor="middle" transform="translate(360,-2)rotate(-60)" style="font-size: 10px; font-family: Impact; fill: rgb(206, 109, 189);">system</text><text text-anchor="middle" transform="translate(71,209)rotate(60)" style="font-size: 10px; font-family: Impact; fill: rgb(222, 158, 214);">evolved</text><text text-anchor="middle" transform="translate(-376,-83)rotate(-60)" style="font-size: 10px; font-family: Impact; fill: rgb(57, 59, 121);">powerful</text><text text-anchor="middle" transform="translate(242,95)rotate(60)" style="font-size: 10px; font-family: Impact; fill: rgb(82, 84, 163);">control</text><text text-anchor="middle" transform="translate(-252,56)rotate(-30)" style="font-size: 10px; font-family: Impact; fill: rgb(107, 110, 207);">mechanism</text><text text-anchor="middle" transform="translate(-35,208)rotate(0)" style="font-size: 10px; font-family: Impact; fill: rgb(156, 158, 222);">subsumes</text><text text-anchor="middle" transform="translate(191,49)rotate(-30)" style="font-size: 10px; font-family: Impact; fill: rgb(99, 121, 57);">minds</text><text text-anchor="middle" transform="translate(357,-27)rotate(30)" style="font-size: 10px; font-family: Impact; fill: rgb(140, 162, 82);">steers</text><text text-anchor="middle" transform="translate(-174,-181)rotate(30)" style="font-size: 10px; font-family: Impact; fill: rgb(181, 207, 107);">automates</text><text text-anchor="middle" transform="translate(273,-197)rotate(-60)" style="font-size: 10px; font-family: Impact; fill: rgb(206, 219, 156);">thinking</text><text text-anchor="middle" transform="translate(93,131)rotate(-60)" style="font-size: 10px; font-family: Impact; fill: rgb(140, 109, 49);">see</text><text text-anchor="middle" transform="translate(348,-118)rotate(0)" style="font-size: 10px; font-family: Impact; fill: rgb(189, 158, 57);">described</text><text text-anchor="middle" transform="translate(-165,143)rotate(30)" style="font-size: 10px; font-family: Impact; fill: rgb(231, 186, 82);">aiming</text><text text-anchor="middle" transform="translate(344,-141)rotate(0)" style="font-size: 10px; font-family: Impact; fill: rgb(231, 203, 148);">dissolution</text><text text-anchor="middle" transform="translate(54,54)rotate(-30)" style="font-size: 10px; font-family: Impact; fill: rgb(132, 60, 57);">core</text><text text-anchor="middle" transform="translate(382,30)rotate(60)" style="font-size: 10px; font-family: Impact; fill: rgb(173, 73, 74);">reason</text><text text-anchor="middle" transform="translate(-120,-240)rotate(-60)" style="font-size: 10px; font-family: Impact; fill: rgb(214, 97, 107);">programmings</text><text text-anchor="middle" transform="translate(-58,228)rotate(60)" style="font-size: 10px; font-family: Impact; fill: rgb(231, 150, 156);">effectivenessthe</text><text text-anchor="middle" transform="translate(-261,37)rotate(-60)" style="font-size: 10px; font-family: Impact; fill: rgb(123, 65, 115);">critical</text><text text-anchor="middle" transform="translate(-252,-215)rotate(60)" style="font-size: 10px; font-family: Impact; fill: rgb(165, 81, 148);">dependence</text><text text-anchor="middle" transform="translate(296,-189)rotate(-30)" style="font-size: 10px; font-family: Impact; fill: rgb(206, 109, 189);">continuity</text><text text-anchor="middle" transform="translate(23,-77)rotate(0)" style="font-size: 10px; font-family: Impact; fill: rgb(222, 158, 214);">lives</text><text text-anchor="middle" transform="translate(-273,-198)rotate(60)" style="font-size: 10px; font-family: Impact; fill: rgb(57, 59, 121);">coherence</text><text text-anchor="middle" transform="translate(22,-257)rotate(60)" style="font-size: 10px; font-family: Impact; fill: rgb(82, 84, 163);">socially</text><text text-anchor="middle" transform="translate(-192,141)rotate(30)" style="font-size: 10px; font-family: Impact; fill: rgb(107, 110, 207);">constructed</text><text text-anchor="middle" transform="translate(11,-213)rotate(0)" style="font-size: 10px; font-family: Impact; fill: rgb(156, 158, 222);">personas</text><text text-anchor="middle" transform="translate(-184,43)rotate(0)" style="font-size: 10px; font-family: Impact; fill: rgb(99, 121, 57);">wear</text><text text-anchor="middle" transform="translate(-272,28)rotate(-60)" style="font-size: 10px; font-family: Impact; fill: rgb(140, 162, 82);">oppose</text><text text-anchor="middle" transform="translate(-8,-261)rotate(-60)" style="font-size: 10px; font-family: Impact; fill: rgb(181, 207, 107);">popular</text><text text-anchor="middle" transform="translate(-391,41)rotate(-60)" style="font-size: 10px; font-family: Impact; fill: rgb(206, 219, 156);">prediction</text><text text-anchor="middle" transform="translate(-374,63)rotate(30)" style="font-size: 10px; font-family: Impact; fill: rgb(140, 109, 49);">upcoming</text><text text-anchor="middle" transform="translate(-140,-240)rotate(-60)" style="font-size: 10px; font-family: Impact; fill: rgb(189, 158, 57);">dreadful</text><text text-anchor="middle" transform="translate(86,190)rotate(60)" style="font-size: 10px; font-family: Impact; fill: rgb(231, 186, 82);">action</text><text text-anchor="middle" transform="translate(-406,8)rotate(30)" style="font-size: 10px; font-family: Impact; fill: rgb(231, 203, 148);">worrying</text><text text-anchor="middle" transform="translate(149,-174)rotate(-30)" style="font-size: 10px; font-family: Impact; fill: rgb(132, 60, 57);">soon</text><text text-anchor="middle" transform="translate(-81,6)rotate(60)" style="font-size: 10px; font-family: Impact; fill: rgb(173, 73, 74);">come</text><text text-anchor="middle" transform="translate(35,7)rotate(0)" style="font-size: 10px; font-family: Impact; fill: rgb(214, 97, 107);">govern</text><text text-anchor="middle" transform="translate(-219,-171)rotate(60)" style="font-size: 10px; font-family: Impact; fill: rgb(231, 150, 156);">let</text><text text-anchor="middle" transform="translate(359,82)rotate(-60)" style="font-size: 10px; font-family: Impact; fill: rgb(123, 65, 115);">help</text><text text-anchor="middle" transform="translate(88,-193)rotate(30)" style="font-size: 10px; font-family: Impact; fill: rgb(165, 81, 148);">finally</text><text text-anchor="middle" transform="translate(207,174)rotate(60)" style="font-size: 10px; font-family: Impact; fill: rgb(206, 109, 189);">able</text><text text-anchor="middle" transform="translate(-73,-258)rotate(30)" style="font-size: 10px; font-family: Impact; fill: rgb(222, 158, 214);">Keywords</text><text text-anchor="middle" transform="translate(221,-242)rotate(30)" style="font-size: 10px; font-family: Impact; fill: rgb(57, 59, 121);">personware</text><text text-anchor="middle" transform="translate(-367,100)rotate(30)" style="font-size: 10px; font-family: Impact; fill: rgb(82, 84, 163);">communication</text><text text-anchor="middle" transform="translate(399,-76)rotate(-60)" style="font-size: 10px; font-family: Impact; fill: rgb(107, 110, 207);">cognition</text><text text-anchor="middle" transform="translate(-229,120)rotate(0)" style="font-size: 10px; font-family: Impact; fill: rgb(156, 158, 222);">dissonance</text><text text-anchor="middle" transform="translate(45,221)rotate(-60)" style="font-size: 10px; font-family: Impact; fill: rgb(99, 121, 57);">symbolic</text><text text-anchor="middle" transform="translate(321,-166)rotate(-60)" style="font-size: 10px; font-family: Impact; fill: rgb(140, 162, 82);">order</text><text text-anchor="middle" transform="translate(-159,-269)rotate(-60)" style="font-size: 10px; font-family: Impact; fill: rgb(181, 207, 107);">emancipation</text><text text-anchor="middle" transform="translate(1,244)rotate(-30)" style="font-size: 10px; font-family: Impact; fill: rgb(206, 219, 156);">Introduction</text><text text-anchor="middle" transform="translate(397,-34)rotate(60)" style="font-size: 10px; font-family: Impact; fill: rgb(140, 109, 49);">collective</text><text text-anchor="middle" transform="translate(-91,239)rotate(-30)" style="font-size: 10px; font-family: Impact; fill: rgb(189, 158, 57);">imagination</text><text text-anchor="middle" transform="translate(-338,-43)rotate(60)" style="font-size: 10px; font-family: Impact; fill: rgb(231, 186, 82);">society</text><text text-anchor="middle" transform="translate(-399,-46)rotate(0)" style="font-size: 10px; font-family: Impact; fill: rgb(231, 203, 148);">grown</text><text text-anchor="middle" transform="translate(-25,-273)rotate(-30)" style="font-size: 10px; font-family: Impact; fill: rgb(132, 60, 57);">preoccupied</text><text text-anchor="middle" transform="translate(-383,-107)rotate(0)" style="font-size: 10px; font-family: Impact; fill: rgb(173, 73, 74);">images</text><text text-anchor="middle" transform="translate(-108,-218)rotate(-30)" style="font-size: 10px; font-family: Impact; fill: rgb(214, 97, 107);">course</text><text text-anchor="middle" transform="translate(234,-221)rotate(30)" style="font-size: 10px; font-family: Impact; fill: rgb(231, 150, 156);">already</text><text text-anchor="middle" transform="translate(196,202)rotate(-60)" style="font-size: 10px; font-family: Impact; fill: rgb(123, 65, 115);">pointed</text><text text-anchor="middle" transform="translate(-334,148)rotate(-60)" style="font-size: 10px; font-family: Impact; fill: rgb(165, 81, 148);">extensively</text><text text-anchor="middle" transform="translate(58,-238)rotate(30)" style="font-size: 10px; font-family: Impact; fill: rgb(206, 109, 189);">Nick</text><text text-anchor="middle" transform="translate(-233,203)rotate(-60)" style="font-size: 10px; font-family: Impact; fill: rgb(222, 158, 214);">Bostrom</text><text text-anchor="middle" transform="translate(-282,163)rotate(0)" style="font-size: 10px; font-family: Impact; fill: rgb(57, 59, 121);">however</text><text text-anchor="middle" transform="translate(378,-98)rotate(30)" style="font-size: 10px; font-family: Impact; fill: rgb(82, 84, 163);">stops</text><text text-anchor="middle" transform="translate(396,-114)rotate(30)" style="font-size: 10px; font-family: Impact; fill: rgb(107, 110, 207);">humanlevel</text><text text-anchor="middle" transform="translate(168,223)rotate(30)" style="font-size: 10px; font-family: Impact; fill: rgb(156, 158, 222);">machine</text><text text-anchor="middle" transform="translate(33,-262)rotate(60)" style="font-size: 10px; font-family: Impact; fill: rgb(99, 121, 57);">latter</text><text text-anchor="middle" transform="translate(48,247)rotate(-60)" style="font-size: 10px; font-family: Impact; fill: rgb(140, 162, 82);">destination</text><text text-anchor="middle" transform="translate(374,72)rotate(30)" style="font-size: 10px; font-family: Impact; fill: rgb(181, 207, 107);">next</text><text text-anchor="middle" transform="translate(10,-250)rotate(-30)" style="font-size: 10px; font-family: Impact; fill: rgb(206, 219, 156);">stop</text><text text-anchor="middle" transform="translate(-251,104)rotate(30)" style="font-size: 10px; font-family: Impact; fill: rgb(140, 109, 49);">short</text><text text-anchor="middle" transform="translate(-399,75)rotate(-30)" style="font-size: 10px; font-family: Impact; fill: rgb(189, 158, 57);">distance</text><text text-anchor="middle" transform="translate(-176,-269)rotate(-60)" style="font-size: 10px; font-family: Impact; fill: rgb(231, 186, 82);">farther</text><text text-anchor="middle" transform="translate(-253,77)rotate(-60)" style="font-size: 10px; font-family: Impact; fill: rgb(231, 203, 148);">tracks</text><text text-anchor="middle" transform="translate(355,-164)rotate(30)" style="font-size: 10px; font-family: Impact; fill: rgb(132, 60, 57);">doi103390info9050113</text><text text-anchor="middle" transform="translate(395,93)rotate(-30)" style="font-size: 10px; font-family: Impact; fill: rgb(173, 73, 74);">wwwmdpicomjournalinformation</text></g></svg>
Thus, we oppose the popular prediction
Thus, we oppose the popular prediction of the upcoming, - ‘dreadful AI takeover’ with - a call for action:
instead of worrying that ArtificialIntelligence
instead of worrying that - Artificial Intelligence will soon come to
let us think of how it could help the human being to - finally be able to do it
// harness emergent Artificial Intelligence - in a man-machine symbiosis created - for the people, by the people, - for Human benefit first - (not for the benefit of a few with the control of the machines designed to control humans) - which itself is a fools errand, born of the inability of honoring the complexity of the situation on a clear self-terminating path - but by Flipping the prevailing paradigm of - Augmenting the Machine's capabilities at the expense noit only of Human Potential, but actually limiting the capabilities of the machines and destroying the possibility of the emergence of collective synthesys of Human Intellect and Symmathesy for human benefit empowered by emergent externalization of human interintellect in aform that enables machine to manifest sythetic intellect capable of managing comkplexity for mutual benefit.
We see the venture intothe existential opportunity
We see the venture into - the existential opportunity described here as
aiming at the - global dissolution of the core reason of that programming’s effectiveness
—the critical dependence of the continuity of human lives on the - coherence of the socially constructed personas they ‘wear.’
Our proposition is grounded in a detailed analysis
Our proposition is grounded in a detailed analysis of - the manner in which the socio-econo-political system - has evolved into a powerful control mechanism
that - subsumes human minds, - steers their will and - automates their thinking.
We envision a configuration of three kinds of cognitive system
We envision a configuration of three kinds of cognitive system - —the human mind, - social systems and - the emerging synthetic intelligence - —serving to augment - the autonomy of the first from - the - ‘programming’ imposed by the second.
The opportunity residesin
The opportunity resides in the - moment of transition of the Internet - —from mediating information to - mediating distributed direct governance
in the sense of self-organization.
We propose a venture into an
We propose a venture into an - existential opportunity - for establishing a world - ‘good enough’ for humans to live in.
Defining an - existential opportunity as the converse of - an existential risk
—that is, a development that promises to - dramatically improve the future of humanity
—we argue that one such opportunity - is available and - should be explored now.
A demographic inversion is taking place: cities are where the affluent millennials and retirees want to live, while suburbs are becoming home to poorer people and immigrants.

The Great Inversion
what?
asset-centric logic
asset-centric logic
Snippet The Great Inversion: A Glimpse into the Future

Tino Klaehne 2nd degree connection 2nd Scaling Corporate Innovation with Strategy & Design Talks about #foresight, #strategicforesight, #corporateinnovation, and #strategicintelligenceTalks about hashtag foresight, hashtag strategicforesight, hashtag corporateinnovation, and hashtag strategicintelligence Lufthansa Innovation Hub Technical University Munich Berlin, Berlin, Germany Contact info
Békés Veronika A TUDOMÁNYOS TERMINUSOK JELENTÉSVÁLTOZÁSÁNAK PROBLÉMAKÖRE AZ ÖSSZEHASONLÍTÓ TUDOMÁNYTÖRTÉNETI KUTATÁSBAN
[PDF][PDF] Study for the development of human intellect augmentation techniquesDC Engelbart, WK English… - Interim Progress Report …, 1968 - 129.69.211.95… After procedures for this hard-copy distribution have been established, we intend to develop methods for handling special requests for hard-copy information from Network members. …Save Cite Cited by 14 Related articles All 12 versions
to Study for the development of human intellect augmentation techniques

augmenting human intellect
The Human Takeover: A Call for a Venture into an Existential OpportunityFrancis Heylighen

Francis Heylighen uploaded a paper: The Human Takeover: A Call for a Venture into an Existential Opportunity.3 days ago


Telegram Private Channels & Groups: All You Need to Know in 2022
Decentralized Storage Alliance@_DSAllianceJoin the most influential enterprises advancing decentralized storage technology, Filecoin, IPFS, and libp2p.dsalliance.ioJoined October 2022
By the People, For the People
x
Local-First to the Rescue
yes
Simplifying Web App Development

This document will mimic wiki's item mobility
mimic wiki's item moblity by writing in - single line paragraphs - each item begins with a quotable statement in bold, followed by - disambiguate statement of purpose - // equivalent to '- stub ' clueMark in TrailMarks In-line-plain-text-notation - initially serve as a guide to discussion - later outline for a more standalone document
Visual Design Principles
song of the cosmos

List of ENS+IPFS websites : r/ipfsReddithttps://www.reddit.com › ipfs › comments › list_of_en...Reddithttps://www.reddit.com › ipfs › comments › list_of_en...May 28, 2019 — We create an IPFS content-chain per author. Everytime an author publishes an article, it is added to the end of this content-chain and the ...
Content Sharing Network based on IPFS and BlockchainInstitute of Physicshttps://iopscience.iop.org › article › pdfInstitute of Physicshttps://iopscience.iop.org › article › pdfby H Xu · 2021 · Cited by 3 — InnerLight uses two chains, one is IPFS content chain and the other is a blockchain, which is a cryptocurrency chain. Each article is posted ...
search - "ipfs content chain"

Content Sharing Network based on IPFS and Blockchain

google - search -"ipfs content chain"
who needs - blockchains
when we can have - content-chains
?

Holy Spirit

Alignment with what? Human values. Who has human values?
who's human values?
https://www.youtube.com/watch?v=-hxeDjAxvJ8

And if AI assistance can do that better
question
Do you think we'll still have Google search 00:01:14 in 5 in 10 years
topic - would we have Google Search in 5 ten years time?
Biggest story of the Year and the media ignores it?

Myths and MythconceptionsWhat does it mean to be a programming language, anyhow?
vernacular code
from : Ward
from - https://hyp.is/_YzBoBWBEe6NhMfmN0QEww/www.hylo.com/all/post/61543
from : hylo activity pubs pods
Creating decentralized social apps has never been easier ActivityPods brings together two game-changing technologies, ActivityPub and Solid Pods, and empowers developers to create truly decentralized applications
Once we have ActivityPub sorted then a decedent of https://activitypods.org/ might become that 'one stop' place. Where you could post thread based link stuff to Kbin, Write Mastodon microblogs or medium form pieces for Hylo or Humhub.
hylo activity pubs pods
Intelligent Archive From Viewpoints Intelligent Archive Jump to: navigation, search Welcome to Viewpoints Intelligent Archive!
4 - broken wheel - normal considered harmful
https://bafybeid7zme6dz3ztgd7eylxtkun2bezchcbufmeh5my4txhnax6z3fdmq.ipfs.w3s.link/logo%20-%20viewpoints.png
4 why worry about tomorrow

4 why worry about tomorrow

the proletariat live in the present because they have nothing else
live in the present
the aristocrats live on the past
come from a noble family
the point is eternal life which is here and now
be here now
a man who understands the dao in the morning may die with content in the evening
confucius very wisely said a man who understands the dao in the morning may die with content in the evening because when you understand
Alan Watts - Do Not Worry About Tomorrow | Life Lessons |
https://hyp.is/eEuIqBQbEe6EGwOUr4l4VQ/en.wikipedia.org/wiki/The_7_Habits_of_Highly_Effective_People


4 Integral design

Modular vs. Integral Product Architectures | Product Design and Development | Dr. Loay Al-Zube

How to control views is an implementation issue.
for : Launch Community
No we need a
Universal HyperDocument as a Lively KRNL
and specify views in terms of elaborate convergent coherent consitence complete
conceptual model of ino structure along with intended interpretation
supply morphic hoilonic blocks as |Javascriopt Modules
Effective HyperDocuments

Q&A with Doug Engelbart: July 26, 2001
what a gem
for : Launch Community

Don't tell me what you do, show me
show me
for : Launch Community
As we get better at dealing with complex problems, we'll be better at dealing with this. (3697) Must evolve
getting better
life-long learning
life long learning
Transformations (3415) Presentation (3410) Querying (3342) Doug doesn't distinguish this from presentation
transformation
presentation
querying
that is presentation
Dynamic information display We've been conditioned to static displays. This isn't taking advantage of how we can and want to view knowledge.
dynamic information display
conditioned to static display
Revision control
make refvision control integral with p2p communication patterns and explicit in the hyper document chain
not block chain
Typed links (3740)
links with shapes of TrailMarks
Edited documents won't go back to legacy tools. Evolves you to OHS documents.
no go back to legacy tools
Eliot Kimber's system Created an incredibly sophisticated system, but nobody would use it, because they didn't understand it. (3489)
nobody would use it
Evolvability is vital (3470) Humans are capable of evolving
Status quo is evolution; what Doug is talking about is a revolution.
revolution
This architectural knowledge, usually, is not documented, since it is considered tacit knowledge of architects or other stakeholders, and eventually dissipates.
architectural knowledge
considered tacit knowledge
eventually dissipates

Figure 6: Recommended architectural style

Figure 4: Example of two architectural styles stored in the knowledge database

A decision-making tool to support architectural designs based on quality attributes

Overview of Proposed Process | Download Scientific Diagram

Energy Systems DesignIntentional Design is Our ID — Energy ...

search - integral intentional design
The Importance of Being Intentional In Design | 12 Days of UX
search : "intentional design"
Intentional design
is a process where the user's interactions with the product, app or website are considered at each point of the design process. Intentional design is a process that provides systematic methods that explore a variety of user interactions and touchpoints that move, engage and respond.
Establishing a Think TankJune 27, 2023
<svg width="41" height="41" viewBox="0 0 41 41" fill="none" xmlns="http://www.w3.org/2000/svg" stroke-width="1.5" class="h-6 w-6" role="img"><title>ChatGPT</title><text x="-9999" y="-9999">ChatGPT</text><path d="M37.5324 16.8707C37.9808 15.5241 38.1363 14.0974 37.9886 12.6859C37.8409 11.2744 37.3934 9.91076 36.676 8.68622C35.6126 6.83404 33.9882 5.3676 32.0373 4.4985C30.0864 3.62941 27.9098 3.40259 25.8215 3.85078C24.8796 2.7893 23.7219 1.94125 22.4257 1.36341C21.1295 0.785575 19.7249 0.491269 18.3058 0.500197C16.1708 0.495044 14.0893 1.16803 12.3614 2.42214C10.6335 3.67624 9.34853 5.44666 8.6917 7.47815C7.30085 7.76286 5.98686 8.3414 4.8377 9.17505C3.68854 10.0087 2.73073 11.0782 2.02839 12.312C0.956464 14.1591 0.498905 16.2988 0.721698 18.4228C0.944492 20.5467 1.83612 22.5449 3.268 24.1293C2.81966 25.4759 2.66413 26.9026 2.81182 28.3141C2.95951 29.7256 3.40701 31.0892 4.12437 32.3138C5.18791 34.1659 6.8123 35.6322 8.76321 36.5013C10.7141 37.3704 12.8907 37.5973 14.9789 37.1492C15.9208 38.2107 17.0786 39.0587 18.3747 39.6366C19.6709 40.2144 21.0755 40.5087 22.4946 40.4998C24.6307 40.5054 26.7133 39.8321 28.4418 38.5772C30.1704 37.3223 31.4556 35.5506 32.1119 33.5179C33.5027 33.2332 34.8167 32.6547 35.9659 31.821C37.115 30.9874 38.0728 29.9178 38.7752 28.684C39.8458 26.8371 40.3023 24.6979 40.0789 22.5748C39.8556 20.4517 38.9639 18.4544 37.5324 16.8707ZM22.4978 37.8849C20.7443 37.8874 19.0459 37.2733 17.6994 36.1501C17.7601 36.117 17.8666 36.0586 17.936 36.0161L25.9004 31.4156C26.1003 31.3019 26.2663 31.137 26.3813 30.9378C26.4964 30.7386 26.5563 30.5124 26.5549 30.2825V19.0542L29.9213 20.998C29.9389 21.0068 29.9541 21.0198 29.9656 21.0359C29.977 21.052 29.9842 21.0707 29.9867 21.0902V30.3889C29.9842 32.375 29.1946 34.2791 27.7909 35.6841C26.3872 37.0892 24.4838 37.8806 22.4978 37.8849ZM6.39227 31.0064C5.51397 29.4888 5.19742 27.7107 5.49804 25.9832C5.55718 26.0187 5.66048 26.0818 5.73461 26.1244L13.699 30.7248C13.8975 30.8408 14.1233 30.902 14.3532 30.902C14.583 30.902 14.8088 30.8408 15.0073 30.7248L24.731 25.1103V28.9979C24.7321 29.0177 24.7283 29.0376 24.7199 29.0556C24.7115 29.0736 24.6988 29.0893 24.6829 29.1012L16.6317 33.7497C14.9096 34.7416 12.8643 35.0097 10.9447 34.4954C9.02506 33.9811 7.38785 32.7263 6.39227 31.0064ZM4.29707 13.6194C5.17156 12.0998 6.55279 10.9364 8.19885 10.3327C8.19885 10.4013 8.19491 10.5228 8.19491 10.6071V19.808C8.19351 20.0378 8.25334 20.2638 8.36823 20.4629C8.48312 20.6619 8.64893 20.8267 8.84863 20.9404L18.5723 26.5542L15.206 28.4979C15.1894 28.5089 15.1703 28.5155 15.1505 28.5173C15.1307 28.5191 15.1107 28.516 15.0924 28.5082L7.04046 23.8557C5.32135 22.8601 4.06716 21.2235 3.55289 19.3046C3.03862 17.3858 3.30624 15.3413 4.29707 13.6194ZM31.955 20.0556L22.2312 14.4411L25.5976 12.4981C25.6142 12.4872 25.6333 12.4805 25.6531 12.4787C25.6729 12.4769 25.6928 12.4801 25.7111 12.4879L33.7631 17.1364C34.9967 17.849 36.0017 18.8982 36.6606 20.1613C37.3194 21.4244 37.6047 22.849 37.4832 24.2684C37.3617 25.6878 36.8382 27.0432 35.9743 28.1759C35.1103 29.3086 33.9415 30.1717 32.6047 30.6641C32.6047 30.5947 32.6047 30.4733 32.6047 30.3889V21.188C32.6066 20.9586 32.5474 20.7328 32.4332 20.5338C32.319 20.3348 32.154 20.1698 31.955 20.0556ZM35.3055 15.0128C35.2464 14.9765 35.1431 14.9142 35.069 14.8717L27.1045 10.2712C26.906 10.1554 26.6803 10.0943 26.4504 10.0943C26.2206 10.0943 25.9948 10.1554 25.7963 10.2712L16.0726 15.8858V11.9982C16.0715 11.9783 16.0753 11.9585 16.0837 11.9405C16.0921 11.9225 16.1048 11.9068 16.1207 11.8949L24.1719 7.25025C25.4053 6.53903 26.8158 6.19376 28.2383 6.25482C29.6608 6.31589 31.0364 6.78077 32.2044 7.59508C33.3723 8.40939 34.2842 9.53945 34.8334 10.8531C35.3826 12.1667 35.5464 13.6095 35.3055 15.0128ZM14.2424 21.9419L10.8752 19.9981C10.8576 19.9893 10.8423 19.9763 10.8309 19.9602C10.8195 19.9441 10.8122 19.9254 10.8098 19.9058V10.6071C10.8107 9.18295 11.2173 7.78848 11.9819 6.58696C12.7466 5.38544 13.8377 4.42659 15.1275 3.82264C16.4173 3.21869 17.8524 2.99464 19.2649 3.1767C20.6775 3.35876 22.0089 3.93941 23.1034 4.85067C23.0427 4.88379 22.937 4.94215 22.8668 4.98473L14.9024 9.58517C14.7025 9.69878 14.5366 9.86356 14.4215 10.0626C14.3065 10.2616 14.2466 10.4877 14.2479 10.7175L14.2424 21.9419ZM16.071 17.9991L20.4018 15.4978L24.7325 17.9975V22.9985L20.4018 25.4983L16.071 22.9985V17.9991Z" fill="currentColor"></path></svg>
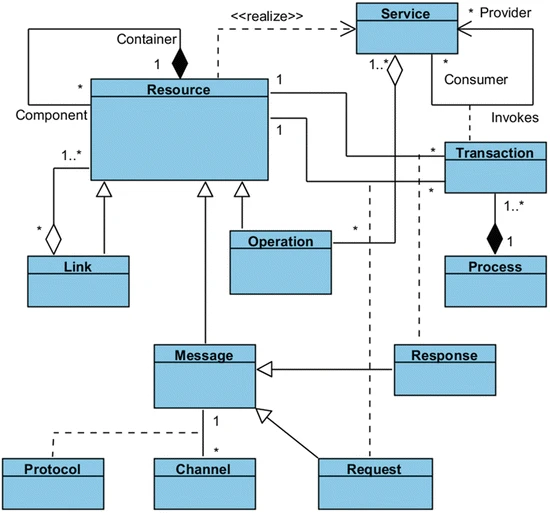
The People System and Tool System
People, Tools, and Communication systems are three legs of an (inter)personal augmented capacity to deal with complex systems
noetic exoskeletong

Toward a World Wise WebSep. 29, 2016•2 likes2 likes×Tasha OlivaDec. 12, 2021, Did u try to use external powers for studying? Like ⇒ www.HelpWriting.net ⇐ ? They helped me a lot once. Jonny DubowskyAug. 04, 2020, Chief Technical Officer, Cyberneticist, Blockchain Architect, Artist metadata.at at Bosman Utd FutureCorp, Show More•7,399 views
Knowing in the WildCo-creating global federated knowledge gardens.

Overhand knot becomes a trefoil knot by joining the ends

to : https://hyp.is/05Rn2BS3Ee6cCk9WETravw/en.wikipedia.org/wiki/Overhand_knot
Trefoil knot


Overhand knot

Trefoil knot fold

To be classified as a FAIR Digital Object (FDO), a digital object is identified by a globally-unique, persistent and resolvable identifier with a predictable resolution behaviour, described by related metadata records (FDOs themselves) and classified by the FDOF typing system.
for : FAIR digital Objects

This is a deeply flawed conception.
It is quite understandable whyt it had arose
why it is the dominant trend
Getting close to articulate and alternative.
the concept of a named data networks affords an alternative conceptualization for digital Objects
https://indylab1.fission.app/hyp?named%20data%20network
with that
The network can become the co-evolving Object Store
Better Still
The Network becomes the Global yet Personal First Information Store for humanity
On the IndyWeb documents created by people become virtual in autonomous hypermedia spaces
augmented with the use of the TrailMarks MarkIn notations
resulting in improving the intellectual effectiveness of not only of individual human beings but providing the means needed to combine structure with collaboration at scale for the benefit of people first
but the structuring of human readable content with TrailMarks allow machine's to process the information for the benefit of people first as opposed to disgusing that information as data for improving the intellectual effectiveness of machines first, at the detriments of humans primarily benefittng the few people who own and operate those machines via Big Tech and Big Government
, evergreen, with full provenance meaning fully connected facilitating deep asynchronous interest based trusted conversations
and the Creation of Open Commons Based Peer Produced Learning, Reasearch and Teaching Commons
better still The Network is the People Centered Internet scale Trusted Information Store created by the people connected in meaningful trusted ways for their owned benefits
in their owned Autnonomous and with the IndyWeb and Trailmarks in a form that Humans no longer disgised as Data
FAIR Digital Object Framework Documentation Working Draft
for : FAIR Digital Objects

for : FAIR digital Objects
Evaluating FAIR Digital Object and Linked Data as distributed object systems
x
An Interoperability Framework and Distributed Platform for Fast Data Applications
for : FAIR digital Objects
Comparison tables for evaluating FAIR Digital Object and Linked Data
for : FAIR digital Objects
John V. Tucker, Swansea University, Swansea, UK
nice to see this
Intertwingled: The Work and Influence of Ted Nelson (History of Computing) 1st ed. 2015 Edition

https://bafybeihhu2kzguxj2j5o6wv3sch4jyqlirc6x4n4hnueo2g3mcboc5ffqy.ipfs.w3s.link/Intertwingled_The_Work_and_Influence_of_Ted_Nelson.pdf
The 7 Habits of Highly Effective People

ACKNOWLEDGMENTS all I describe here is possible because people on the whole do getting things done
Do not focus on effectiveness
Do not try to "Get IT right first time"
Focus on getting the IT right.
Do not try to "Getting Things Done"
Do not be Goal directed be self-directed, where the self becomes selfless through recognizing it's and thr IT's interdependence.
Do not Worry about the morrow
trust the YoUniversa like another , and the Others
When the IT is right it will take care of itself.
IT will be Done. Not through the power of your will.
Do not will it, let it be so, grow never done,.
having a high self-worth and security
appreciating what you have in the first place
blessings
Do not worry about the tommorow
trust the Universe as an Other
as one self
 Be Here Now
Be Here Now
celebrate the success of others
yes
that creates abundance
abundance mentality, or abundance mindset, a way of thinking in which a person believes there are enough resources and successes to share with others.
Trust the Universe
Trust One Self not selfishly
but knowing the more give the more you will become
Do good, expect good.
Good is not the dual of Bad or Evil, but is
a self0sustaining postive attitude that creates its rewards without expectations or demands or entitlement but measured with grratitude one feels count your blessings, allways
an open mind to be influenced
synonym of care and attention what else is the point of listenting?
Use empathetic listening to genuinely understand a person
You mean pay real attention, yes Attention is sacred
well
everything is
"Seek first to understand, then to be understood"
So this is where it comes from.
"you are the programmer",
let go of control,
Let it be so
Let IT grow and grow with it
people should spend the majority of their time on II
sure
Not urgent but important (Plan) – long-term development
focus on imnportance engineer against ever facing urgent demands
burning desire detachment from outcomes
wu wei
by doing (seemingly nothing as urgent) accomplish the maximum you can, that would be your own everything
Grow and stay humble
stay humble
who you want to be?
take the wanting out of being
make your efforts rewards in themselves
"Begin with the end in mind"
cultivating attitude and reflecting on available means (personal strength and weaknesses) to purse chosen path not ends
effectiveness as the balance of obtaining desirable results with caring for that which produces those results.
caring about what produces result
Covey presents an approach to being effective in attaining goals by aligning oneself to what he calls "true north" principles based on a character ethic that he presents as universal and timeless

it would seem that a Reflector is constantly taking in other peoples’ energies and emotions. Without any reliable patterns of their own.
spot on
"banquet," and tends to suggest a mood of full-bellied joviality
conviviality
Phenomenology is the study of structures of consciousness as experienced from the first-person point of view. The central structure of an experience is its intentionality, its being directed toward something, as it is an experience of or about some object. An experience is directed toward an object by virtue of its content or meaning (which represents the object) together with appropriate enabling conditions.
Personal Knowing
self-awareness of the Spirit

No surprise that Polanyi though of huimself as Hegelian
search phenomenology writing
Peter ElbowTOWARD A PHENOMENOLOGYOF FREEWRITING
x
Joyce Armstrong Carroll
author
Abstract
abstract The change of emphasis from the written product to writing as a process manifests another important change--one from logical to phenomenological consciousness. Phenomenologically speaking, writing is both "immanent" in the writer and "transcendent" outside the writer. It is thinking of general concepts that actually occurred and writing about these things using every judgment, memory, expectation, inference, conviction, opinion, doubt, and emotion to write about these things. It is hearing and imagining sounds, seeing and imagining objects, sensing and imagining warmth and cold and writing about these things. The change from product to process came about because phenomenological consciousness enables us to "know" differently. As a result, the change continues to move us away from the traditional rhetoric paradigm all wrapped in "what's" to a process approach paradigm all packaged with "how's." (HOD)
PHENOMENOLOGY AND THE WRITING PROCESS JOYCE CARROLL
TOWARD A PHENOMENOLOGY OF FREEWRITINGColorado State Universityhttps://wac.colostate.edu › docs › jbw › elbowColorado State Universityhttps://wac.colostate.edu › docs › jbw › elbowPDFThe nascent interest in phenomenology in the profession is a good sign: a respect for the facts of what actually happens in writers. We've had a decade of ..
"lesson, written evidence"
it does not necessarily imply static
in the case of IndyPlex the key point is that IndyWeb Documents (Plex Pages) do have a canonical form that can be treated as evidence, although they can be presented as evidence, rendered in a wide variety of view forms and affordances
https://twitter.com/TrailMarks/status/1630630038121992195
He actually said that earlier
to : https://hyp.is/81IYWv5FEe2muW-Y-k9iNQ/www.youtube.com/watch?v=RdE-d_EhzmA
https://hypothes.is/a/iDmFCBMrEe6FArMyZbpkcA

From Smalltalk to Squeak by Dan Ingalls at CHM 10/11/2001 (VPRI 797)
smalltalk dan ingalls
Nothing you can do but you can learn how to be you in time

Person Centric Architecture and the MAP
Steve Melville
Memetic Activation Platform
Enterprise Architecture for a More Beautiful World

memetic activation platform
Memetic Activation Platform
MAP
Steve Melville
Collective intelligence
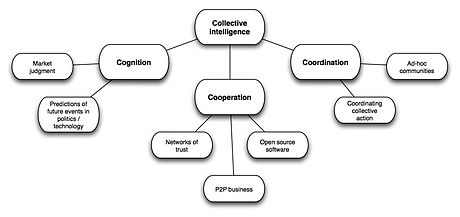
Stigmergic Collaboration: a theoretical framework for mass collaboration
stygmergic collaboration

George Pór defined the collective intelligence phenomenon as "the capacity of human communities to evolve towards higher order complexity and harmony, through such innovation mechanisms as differentiation and integration, competition and collaboration.

clear that the similarities one finds between Leibniz’s philosophy and elements of Chinese thought are merely coincidental.
cones from the same source: Awareness of the One
t is well known that Leibniz was the first Western philosopher to seriously engage with Chinese thought.
yes
search : polanyi pirsig phenomenology

Go forth and annotate!


Henry Gurr

according to our current understanding maybe some new technology some new ideas will be brought into the subject and the meaning of the word computation like now we think of condition a particular framework tuning machines or 00:11:45 church thesis and stuff like that but what if in the future another genius like on Turing will come and propose something else the theory will evolve the way you know we went from Newton's 00:11:57 gravity to Einstein's gravity maybe in the framework of that concept some other things will become possible you know so um it's not to me it's kind of like 00:12:11 not so much about deciding once and for all how it is or how it should be but kind of like accepting it as an open-ended process I think that's much more valuable
here is the answer
that's much more valuable in some 00:12:24 sense than deciding things one way or another
As I learned from Hegel, the important thing about statements not whether in our current constellation of their plodding ellaboration we can assign truth values, but the consteallation of concepts they are built from because they always point to the adjacent not yet discovered and present permutation of future choices which may take us onto path that lead us to discover new things
This one pictures explains it all better than the video
linear complete accounts will never work.
Sot the plodding propositional way will not work.
However mutual recursion and mutual arising works
hence the inexhaustible uncanny effectiveness of the mind
not just mathematics
https://hyp.is/XHzFYBD2Ee6xdQuHWZdmAQ/docdrop.org/video/u3GYrEOoKGk/

The Hyperbolic Geometry of DMT Experiences (@Harvard Science of Psychedelics Club)
Do not tel me you are no mathematician,
He is talking about Qualia, human consciousness
The images may speak to you as a human being at a deep level
The Hyperbolic Geometry of DMT Experiences (@Harvard Science of Psychedelics Club)

Links and Anchors: Connecting DHT Data Together
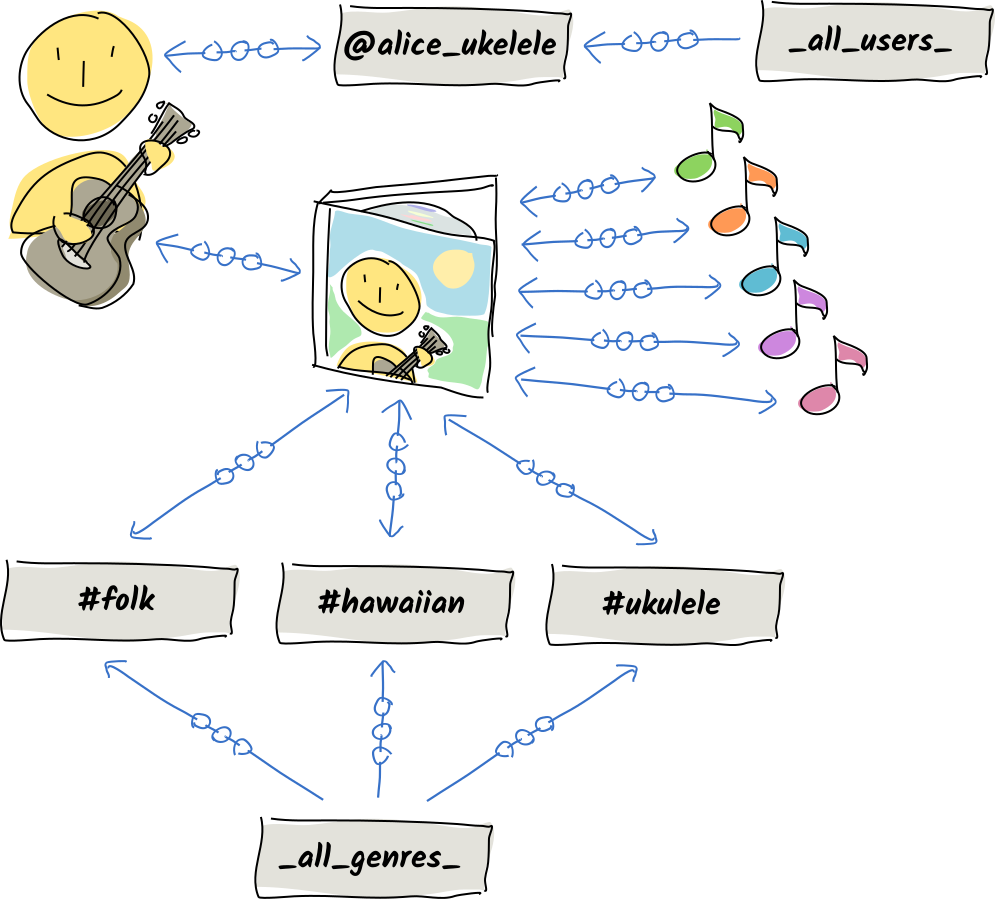
Maujean; it would be epic to get FAN on Holochain in time for this! Check it out: https://developer.holochain.org/concepts/5_links…
fan

A sípoló macskakő - Előzetes
The Internationale
x
Let’s make a clean slate of the past,
x
Learn Wisocracy for Wise Democracy, Wisdom, Wellbeing & Peace for All & Nature
![]()
You need to

You need to attract and retain - the attention of your target audience, - generate buzz and feedback, and - build trust and loyalty.
One of the best ways to do that is to create and nurture a product launch community - - and advocates.
These are the people who will share your vision, - support your goals, and - spread the word
about your product.
But how do you - build and engage such a community?
Here are some tips and best practices to help you.
How do you build and engage your product launch community and advocates?
How to Build and Engage Your Product Launch CommunityLinkedInhttps://www.linkedin.com › ... › Product StrategyLinkedInhttps://www.linkedin.com › ... › Product StrategyJun 12, 2023 — Learn how to create and nurture a product launch community and advocates who will support your goals, share your vision, and spread the word ...
SevenSigma, now offering Issue Mapping Workshops!

Introducing CogNexus Group - providing strategy and policy teams with integrated services for creating shared understanding

Dedicated to Building Shared Understanding of Wicked Problems

CogNexus Group is a new business-oriented service providing strategy and policy teams with integrated services for creating shared understanding. Check us out!

perlIBIS (01)
IBIS dialogue map
transforming our discourse into a Collective IQ
discourse to collective IQ
Eric "announces" KRNL.
search
Invent and adopt alternate ways to organize and structure the DKR.
DKR
Create a Community Development Kit
yes
Willingness to bootstrap
yes
Developing a common ontology
not common but self-defined and then commensurate or mappable/interoperable
develop a formal ontology derived from the narrative documents in the DKR.
formal ontology narrative documents
Collaborative clusters setup

NoteLedge is a digital notebook for designers and content creators to capture inspiration, make mood boards, and accelerate your creative process

thinking at each stage how this is connected to another note, and how the other note is connected back
If you can say what you mean, even to the point of explicating what the meaning of the 'is' is two way meaningful connections will emerge into a spontaneous emergent order spanning a HyperMap that is the territory. Then you come back to it after all your exploration to see it what you meant, had in mind, for the first time articulating your tacit awareness as externalized intellect or extellect
HyperDocument
Virtual IdentitySuch virtual identities, or online identities, are social identities assumed or presented by persons in computer-mediated communication and virtual communities.
for - IndyWeb
Styled text with message entities
x