Smalltalk/X Webserver Welcome to ST/X

Smalltalk/X Webserver Welcome to ST/X

google.search: browlset

🗫 Three Speech Bubbles
Three Speech Bubbles
The image below shows how the “Three Speech Bubbles” symbol might look like on different operating systems. If the font in which this web site is displayed does not contain the symbol and there is no fallback font able to render it, you can use the image below to get an idea of what it should look like.
networked communication
Gear
round metal gear with teeth tools engineering - both : hardware & software settings on UI hard work grinding
🤖
Goes Great With🗜️🔩🧱🤖👨🏭🏗️📐🚗🧰🚲🔨🏎️🏍️🏭🔧⛓️👩🏭🔋🖥️🧲🔒🔓🔏🔐🔑🔗📎🖇️💡🪛
Woman Technologist
emoji.for - universal human user
Goes Great With
👨💻 💻 🖥️ 🖨️ ⌨️ 🖱️ 👩💼 🥑 🧑💻
A woman behind a computer screen, working in the field of technology.
Pinched Fingers
🤌
Card Index
from - Card File Box
Goes Great With
📅 🎫 🗂️ 📧 👤 👥 📞 🗒️ 🗓️ 🗃️ ☎️ 📁 📂 📃 📄 📰 👨💼 👩💼 💻 🗄️ 🏢 📆
Card File Box
better than filing cabinet
A black or gray box with a label holder, containing card index dividers with multicolored tabs, as used to organize and store files. Apple and Facebook’s designs include a lid.
Commonly used for various content concerning paper or computer files, organization, and various types of data, information, and professional or academic work.
File Cabinet
🗄️ emoji
Goes Great With
🗂️ 🗑️ 🗃️ 🗜️ 📁 📂 💻 🖥️ 👨💼 👩💼 🏢 🏷️ 📃 📄 📇 📎 🖇️
Cloud
emoji.for - cloud.computing
plex - computing.machinery
Goes Great With
☀️
Desktop Computer
emoji
🤖 🖱️ 💿 📀 💻 ⌨️ 🤓 🖨️ 📡 🖲️ 🕹️ 👨💻 👩💻 👾 🛠️ ⚙️ 🗜️ 🧰 📺 🔌 📁 📂 🗄️ 📃 📄 💽 💾 🔍 🌐
A desktop personal computer. Generally depicted as a black or gray monitor with a dark or blue screen.
Newspaper
emoji.for
Goes Great With
📻 📜 🗞️ 📺 🆕 📟 📠 ☕ ✂️ 🦅 🌋 🧻 📇 📈 🚨 📱 📉 🎙️ 📼
The front page of a newspaper, as people once read the news before the internet. Commonly used for various content concerning news, media, and journalism as well as personal news.
Robot Face Emoji 🤖
emoji.for - 🤖machine
Robot Face. Supplemental Symbols and Pictographs.
Page with Curl
🧾🧾
plex - 🧾-emoji.for - script
plex - round.trip.between
A white piece of paper, curled up at the bottom to the left or right, with text printed on it, as a business letter. Commonly used for content concerning various types of documents and writing.
Goes Great With
➿ 🖨️ ➰ 🧾 🧻 📏 🗃️ 🗄️ 🗂️ 📇 📎 🖇️ 💻 🖥️ 📄 📝 📑 📜 🗞️ 📋 🗒️ ✂️ 📠 📌 📍
📃 Page with Curl Emoji Meaning A white piece of paper, curled up at the bottom to the left or right, with text printed on it, as a business letter. Commonly used for content concerning various types of documents and writing.
for - pad - round.trip
Goes Great With
➿ 🖨️ ➰ 🧾 🧻 📏 🗃️ 🗄️ 🗂️ 📇 📎 🖇️ 💻 🖥️ 📄 📝 📑 📜 🗞️ 📋 🗒️ ✂️ 📠 📌 📍
Receipt
emoji.for - 🧾🔁📃 round.trip-between
Repeat Button
e🔁moji
emoji.for - 🔁 round.trip - 🧾🔁📃 rount.trip-between
Circular arrows pointing in a clockwise direction. Used in music player applications to loop a track or album continuously. Commonly used to represent a retweet on Twitter.
🛢 (Oil drum) \x1F6E2,
emoji utf8 for - 🛢 database (Oil drum) \x1F6E2, oil drum
Scroll
emoji.for - ?
Goes Great With
📰 🕎 🕍 🧞 🥠 ✒️ 🖋️ 🖊️ 🏺 ⚗️ 🗺️ 📃 🏛️ 📄 🗝️ 🧙 🎓 🗞️ 🗒️
An ancient scroll, unrolled to reveal text on papyrus or parchment paper. May be used to represent the study of history or official documents, such as a diploma.
Prohibited
emoji.for - 👤🚫🆔🛢️no.account(.allowed)
bits - 👤user - 🚫prohibited - 🆔id button - 🛢️database
A red circle with a diagonal line through the middle, from top-left to bottom right, used to indicate that something is not permitted
ID Button
🆔
emoji
for - alias : no.account
Oil Drum
emoji.for - 🛢️database
Goes Great With 🔵 ⛽ 🔷 🕎 🚀 🥁 🥫 🔴 ☠️ 🩸 ☢️ 💧 🟥 🗑️ 🇦🇪 🇦🇴
used,in - no.account.needed : 👤❌🛢️
Cross Mark
emoji.for - no.account.needed : 👤❌🛢️ - ❌crossmark - 👤 Bust in Silhouette - 🛢️database
hieroglyphic and ideographic
Chinese writing
漢字, 汉字
Bust in Silhouette
emoji. for - 👤 user
profile of one person. Often used in interface design to represent a user.
Remote Content
In Markdown editors (Code / Markdown, Slides, Kanban),
CryptPad blocks images and other remotely hosted content - to prevent potential tracking.
Verifying contacts
Ask your contact to share their public key over a secure channel with you.
If this public key matches the one from your contact's profile page, you can be sure that the contact belongs to the person at the other end of the secure channel.
No Account Needed
Icons and Photos For Everything
No Account Icons

Combining character

Unicode has "combining characters". How to use them?

Trailscape
for - 〽️🌆trailscape - Ward Cunningham
Cityscape at Dusk
emoji for - 〽️🌆trailscape - - 〽️🌆trail.scape
🖱️ Computer Mouse Emoji Meaning
augmentation research Commons Bootlab
for - emoji
🖱️
Best Hikes and Trails in Londonderry Park | AllTrails
Part Alternation Mark
for - trailmark - trail - trail.blaze - 〽️🌆trailscape
ggw - 🎎 Ⓜ️ 🎼 ➿ 🎤 🪕 🪘 🥁 🎵 🎶 🎷 🎸 🎹 🎺
Used in traditional Japanese music such as Noh or Renga, to indicate the start of a song. More specifically, the part alternation mark is displayed where the singer’s part begins.
This symbol looks sort of like a lopsided capital M; or a rollercoaster track showing a dip, and then a drop off to the right.
Artist Palette
emoji 🎨 =
for - 👨💻🎨tech.mix - 🗫🕸️🌐Indy0.Net
Three Speech Bubbles
emoji
for - indy.web 🗫🌐 - indy.net 🗫🕸️🌐 - indy0.net 🗫🕸️🌐 - indy.pad 🗫🌐📃 - crypt.pad ⛨🗒️ - tails.net 🪁🕸️
use the notepad 🗒️ as it is enclosing content into document which themselves are not trans or includable
if you type as forwards slash it puts you into an annotation search -
Double Curly Loop
for - trail.mark ➿ ggw - ⛎ ➿ 🕳️ =
Wavy Dash
for - trail marks
ggw - ⛎ ➿ 🕳️
Black Cross On Shield
for - crypt - crypt.pad ⛨🗒️
Milky Way
The Milky Way – a galaxy of billions of stars that includes our own solar system and planet earth.
Shown by many platforms as a night sky, with silhouettes of mountains or hills in the foreground.
for - indranet.space 🕸️🌌
Globe with Meridians
A stylized globe, with blue meridians (longitudes) and latitude. Depicted with light-blue grid of lines on a white, blue, or empty circle.
May be used as a symbol of the internet or world wide web, global communications, international affairs, connectivity and networks, time zones, coordinates, or the world more generally.
for - internet - indranet.space - web
🔗 🌍 🌎 🌏 👥 🗺️ 🗾 🔅 🔆 🕸️ 📱 📡 🕰️ 📶 📞 💻 🖥️ 🇪🇨
💎 Gem Stone Emoji Meaning A jewel or gem, as set into a ring. Depicted in the shape of a classic diamond but in the bright blue color of an aquamarine.
💎
Goes Great With
👒 👩 💍 💖 ⌚ ❇️ ✨ 👰 👑 💠 🤴 👸 🧿 ⛏️ ⚒️ 🗿 📿 👠 ♦️ 🔷 🔹 👗 🤵 🇧🇼
Note Pad
for - pad 🗊 - indy.pad 🗊 - crypt.pad 🗊
Spiral Notepad
A spiral-bound, flip-style notepad or notebook of lined paper, as used for everyday note-taking. Commonly used for content concerning various types of documents and writing.
Most platforms depict a notepad opened to an empty, white page, sometimes shown curled at the bottom. Microsoft’s design is shown closed, with a yellow cover.
for - pad - crypt.pad 🗒️
Goes Great With
🗂️ 📇 📆 ✒️ ✏️ 🖋️ 🖊️ 📐 📏 🗓️ 📎 🖇️ 📝 📒 📃 📜 📄 📅
KiteA diamond-shaped kite with a tail. This emoji appears in various colors across platforms.
kite
for - tails 🪁 - tails.net 🪁🕸️
Piñata
🪅 A colorful decorated container that comes in many shapes, a piñata is filled with candy or toys. Hit to break open for celebrations such as Cinco de Mayo, this is generally associated with Mexico
🪅
Alternate One-Way Left Way Traffic
emoji ⛕ =
for - do.how
related - use.how ⛕
♠ Black Spade Suit
utf8 emoji for - do - spade - do.how: ♠⛕
Adding a custom domain to DigitalOcean Spaces (without moving your DNS)
digital ocean custom domain
Knowledge
quora knowledge

Knowledge

How To Deploy a Static Website to the Cloud with DigitalOcean App Platform

Are We The Baddies?
x
Magic Wand
emoji for - do.how - do - how 🪄⛕
Divide
emoji for - clone
➗
 best of 2017
for
- web mesh
best of 2017
for
- web mesh
QmQ7J9TVoezr5wKRAv7rvmTKLsP5dsjLnxTJWtdx98RqFK
alternative ways of digitally supporting popular use cases for Web services.
Alternative ways
_
of providing
Web Services
-
🌟🌟🌟🌟🌟
=

create a new cyberspace.
P2P
deliver messages that travel around the world just to reach a colleague nearb
Global to reach nearby
proprietary and foreign (often American) apps
Proprietary
overutilize the global tangle
Global tangle
engage with apps that have no need for global connectivity
No need for global connectivity all the time
real-time economy enabled by the wirenet
Real+time economy
Need Continuity without being synchronous -
instant globalization
Globalization
early design decisions foreshadow certain social orders.
Design decision social order
sharing economy’ startups and services are also middlemen:
Middle man
for - web mesh
⚄🌟
best of 2029
The Web began dying in 2014, here's how
for five star
🌟
neurodivergence
Bringing to light - perceptual diversity, or - our inner differences,
could be transformational for society.

Our research will provide - better understanding of
how neurodivergence relates - to the differences in perception
that exist between all of us,
in turn shedding new light on our understanding of - the mind.
bigskysoftware/_hyperscript a small scripting language for the web JavaScript 2,547
for - hyperscript - htmx
htmx, the successor to intercooler.js.
successor to htmx
- intercooler
Become a sponsor to Big Sky Software
from - https://hyp.is/ggvy1seHEe6gpJvF2meEZQ/github.com/sponsors/bigskysoftware
a small scripting language for the web
intercooler.js AJAX With Attributes: There is no need to be complex

can live happily alongside other Javascript frameworks
javascript framework
from
- https://hyp.is/TAKh6seGEe6RMOOYFT8H7A/github.com/sponsors/bigskysoftware

A full-featured HTML template system that is simple, lightweight, and highly performant.
x
Manage gateways · Cloudflare Web3 docs

BEHOLD we're dealing with IPFS here, and nothing gets lost on IPFS, ipfs.io still had it cached: https://ipfs.io/ipfs/QmPKFqVGGeuPRivgYB36N6j62SqNM1teqEYhNHALDS51Cm
behold IPFS
Host Your Site Under Your Domain on IPFS
Install IPFS desktop

for - chitchatter - web meshes - long tail software as a conersation in the long tail of the Indy Web Meshes
share their unique room link
X
Users shouldn't need a service account
to run their code
decentralized Google Docs
Nay
Interpersonal multiplayer collaboration
a Chitchatter room is nothing more than
a Chitchatter room is nothing more than - a named conceptual construct for the connection between peers.
My goal for this project was
My goal for this project was to - enable people to communicate simply and safely, and
I was able to achieve that by - building it as a web mesh.
the Trystero JavaScript library
x
Dan Motzenbecker and his incredible work with the Trystero JavaScript library
x
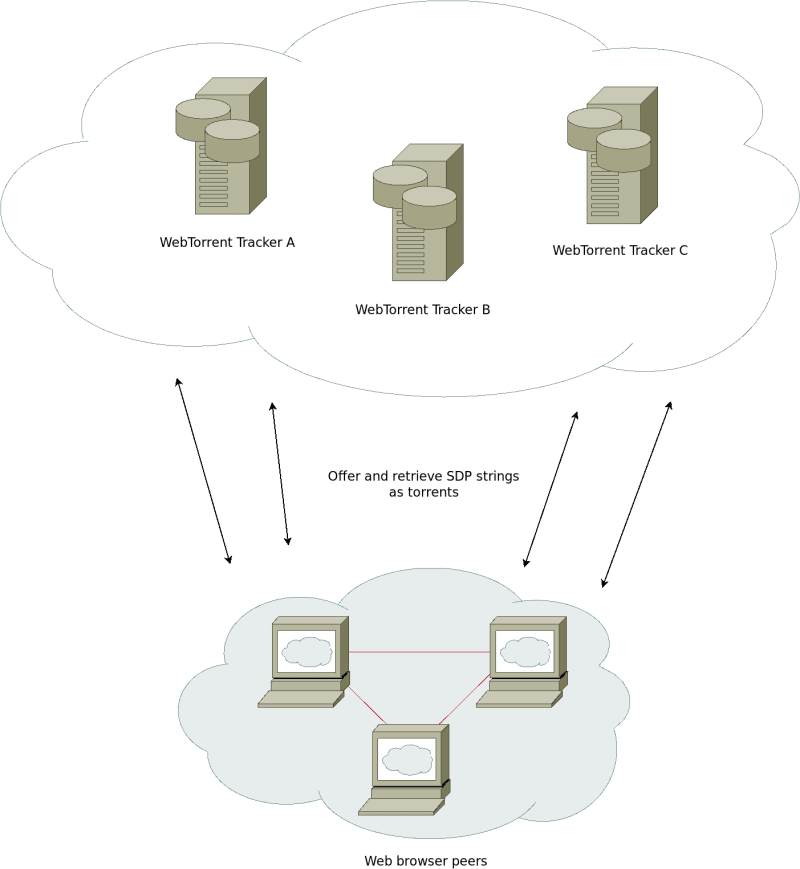
How Web meshes work
For All ∀
for - universal
∀
Bust In Silhouette Emoji
for - user - universal user
Memo Emoji 📝
📝
The New and Improved Pin By CID

We'd love to chat if you're looking for a new way to host an online club or asynchronous gathering
Studios powering a sort of internet club where people work on their own projects, posting updates on a regular cadence, with a short newsletter to periodically share what everyone's up to.
Studiomates + commenting

from - google.search

Martley Web Mesh

Installing Playwright
from - https://hyp.is/DCqbCMXPEe6n9of0Y9JURg/github.com/dmotz/trystero
playwright.config.js
use playwright for tests
Why rooms?
Browsers can only handle a limited amount of WebRTC connections at a time
so it's recommended to design your app such that
users are divided into groups (or rooms, or namespaces, or channels...
whatever you'd like to call them).
Download a pre-built JS file
x
Beyond peer discovery,
Beyond peer discovery, - your app's data never touches the strategy medium and
offers multiple "serverless" strategies for connecting peers (currently BitTorrent, MQTT, Firebase, and IPFS).
Y9ou neab strully serverless
shoulw we call hostless?
a signalling channel is needed to exchange peer information (SDP).
signalling server
to
🤝 Trystero

clandestine courier network
unenclosable carrier empowering chitchatter

🤝 Build instant multiplayer webapps, no server required — Magic WebRTC matchmaking over BitTorrent, MQTT, IPFS, and Firebase
from https://hyp.is/E49AjsTeEe6WDkdHBJoaRA/dev.to/jeremyckahn/taking-the-power-back-with-web-meshes-omg
instant multiplayer web apps
Everything you do disappears automatically when you shut down Tails.
wcwerything
oxism.com/trystero
the app
Introduction to GNOME and the Tails desktop

Dan Motzenbecker selected open-source works
from https://hyp.is/E49AjsTeEe6WDkdHBJoaRA/dev.to/jeremyckahn/taking-the-power-back-with-web-meshes-omg
Network filter
for - caddy
Sysadmin tools: How to use iptables

for - caddy tails
work via To
How to configure programs to access the Internet in Tails. Internet connection settings for command line utilities
from - https://hyp.is/xpAiasRJEe6E9aehHUCVLw/unix.stackexchange.com/questions/680302/make-npm-work-in-tails
More details here miloserdov.org/?p=2640
more details
Make npm work in tails
node.js - Make npm work in tails - Unix & Linux Stack Exchange
https://codebenchers.com › blog › tails-os-web-development-nodejsPrivate Web Development Using Tails OS, VSCodium and Node.js
ddgsearch.ddgo = install and running node app on tails.net
Visual Studio Code on Linux
from - https://hyp.is/LPgs9MQ3Ee6WhPvvLAHgjA/duckduckgo.com/?q=vscode+linux&ia=web
https://github.com › microsoft › vscode-docs › blob › main › docs › setup › linux.mdVisual Studio Code on Linux - GitHub
Tails, or "The Amnesic Incognito Live System",
is a security-focused Debian-based Linux distribution aimed at preserving Internet privacy and anonymity.[5]

Debian, Ubuntu, Raspbian
install caddy
Wiring up Wireguard, Caddy, and Docker on a home server
x
Self-hosted Server accessible over Internet - EASY with Caddy 2!
Self-hosted Server accessible over Internet - EASY with Caddy 2!
*Accessing "localhost" from Anywhere: Your Guide to Remote Localhost Access*
Accessing a Localhost Server on Another Device
Accessing a Localhost Server on Another DeviceuConor Bailey
x
Tailscale network (tailnet)
Your home( lab) away from home
from - https://hyp.is/UtExXMQXEe6GW0Ok4hVjzA/www.youtube.com/watch?v=jDYyC9gF774
TailScale - Your Own Virtual Private Network
from - https://hyp.is/hXDC2sQXEe69okckVcaW6g/duckduckgo.com/?q=how+to+access+local+host+from+tails&ia=web
TailScale - Your Own Virtual Private Network
Tails - Accessing resources on the local network
To access web pages on the local network, use the Unsafe Browser instead. Downloading files from web pages on the local network To download files from web pages on the local network, you can use the curl command instead.
Remote access to local Tails from Windows : r/tails - Reddit
Remote access to local Tails from Windows "Solved" - Not Supported All the posts I've seen are asking about the reverse of this, accessing Windows through Tails. I want to know if it is possible to access a local Tails machine remotely from a Windows machine and how. Would Remote Desktop work or is
Connect to colleagues' local servers from anywhere - Tailscale
Connect to colleagues' local servers from anywhere When building websites or software, you often need to share in-development versions for feedback, review, or to present to stakeholders. Tailscale lets you easily connect to your colleagues' computers, if allowed by your network policy, to view their dev
Modify the bootstrap list | IPFS Docs
Don't change this list unless you understand what it means to do so. Bootstrapping is an important security point of failure in distributed systems: malicious bootstrap peers could only introduce you to other malicious peers.
Set up private ipfs - Help - IPFS Forums
Before you connect, you will need a few things: 1. IP address of the boot node, $BOOTNODE_IP. 2. IPFS peer id of boot node, $BOOTNODE_ID. 3. The swarm key stored at $IPFS_PATH/swarm.key. Ask your SysAdmin for the above information.
Set up private ipfs

torsocks
magiv incantation
Network access

Tor network configuration
tails network
How to run an AppImage
for - IPFS Desktop - tails
why are so many companies leaving the cloud
X
Pluralistic: Daily links from Cory Doctorow
from - https://hyp.is/6N23vjWzEeyWzBuuYTeneg/lindylearn.io/ - https://hyp.is/ynB0ZsK5Ee6mVk_Wl--UFA/ipfs.indy0.net/ipfs/QmZFBDY9yW5TCc7FBtmEfrE86h7Wr42wBUqa1ukusU3koy/

Enshittification,
is the lifecycle of the online platform:
first, - the platform allocates surpluses to end-users;
then, once users are locked in, - those surpluses are taken away and - given to business-customers.
Once the - advertisers, - publishers, - sellers, creators and - performers
are locked in, the surplus is clawed away from them - and taken by the platform.
Pluralistic: Podcasting "Twiddler" (27 Feb 2023)

peter_murray 28 Feb 2023 in Public
nice annotations
from - https://hyp.is/6N23vjWzEeyWzBuuYTeneg/lindylearn.io/
Personal Knowledge Management Tools
kmtools is a script with commands that I'm using to save Hypothesis annotations and Pinboard bookmarks to a local database, then create daily Markdown documents reflecting newly created resources.
Older Woman Emoji 👵
👵
Using the Fetch API
<svg id="mdn-docs-logo" xmlns="http://www.w3.org/2000/svg" x="0" y="0" viewBox="0 0 694.9 104.4" style="enable-background:new 0 0 694.9 104.4" xml:space="preserve" role="img"><title>MDN Web Docs</title><path d="M40.3 0 11.7 92.1H0L28.5 0h11.8zm10.4 0v92.1H40.3V0h10.4zM91 0 62.5 92.1H50.8L79.3 0H91zm10.4 0v92.1H91V0h10.4z" class="logo-m"></path><path d="M627.9 95.6h67v8.8h-67v-8.8z" class="logo-_"></path><path d="M367 42h-4l-10.7 30.8h-5.5l-10.8-26h-.4l-10.5 26h-5.2L308.7 42h-3.8v-5.6H323V42h-6.5l6.8 20.4h.4l10.3-26h4.7l11.2 26h.5l5.7-20.3h-6.2v-5.6H367V42zm34.9 20c-.4 3.2-2 5.9-4.7 8.2-2.8 2.3-6.5 3.4-11.3 3.4-5.4 0-9.7-1.6-13.1-4.7-3.3-3.2-5-7.7-5-13.7 0-5.7 1.6-10.3 4.7-14s7.4-5.5 12.9-5.5c5.1 0 9.1 1.6 11.9 4.7s4.3 6.9 4.3 11.3c0 1.5-.2 3-.5 4.7h-25.6c.3 7.7 4 11.6 10.9 11.6 2.9 0 5.1-.7 6.5-2 1.5-1.4 2.5-3 3-4.9l6 .9zM394 51.3c.2-2.4-.4-4.7-1.8-6.9s-3.8-3.3-7-3.3c-3.1 0-5.3 1-6.9 3-1.5 2-2.5 4.4-2.8 7.2H394zm51 2.4c0 5-1.3 9.5-4 13.7s-6.9 6.2-12.7 6.2c-6 0-10.3-2.2-12.7-6.7-.1.4-.2 1.4-.4 2.9s-.3 2.5-.4 2.9h-7.3c.3-1.7.6-3.5.8-5.3.3-1.8.4-3.7.4-5.5V22.3h-6v-5.6H416v27c1.1-2.2 2.7-4.1 4.7-5.7 2-1.6 4.8-2.4 8.4-2.4 4.6 0 8.4 1.6 11.4 4.7 3 3.2 4.5 7.6 4.5 13.4zm-7.7.6c0-4.2-1-7.4-3-9.5-2-2.2-4.4-3.3-7.4-3.3-3.4 0-6 1.2-8 3.7-1.9 2.4-2.9 5-3 7.7V57c0 3 1 5.6 3 7.7s4.5 3.1 7.6 3.1c3.6 0 6.3-1.3 8.1-3.9 1.8-2.7 2.7-5.9 2.7-9.6zm69.2 18.5h-13.2v-7.2c-1.2 2.2-2.8 4.1-4.9 5.6-2.1 1.6-4.8 2.4-8.3 2.4-4.8 0-8.7-1.6-11.6-4.9-2.9-3.2-4.3-7.7-4.3-13.3 0-5 1.3-9.6 4-13.7 2.6-4.1 6.9-6.2 12.8-6.2 5.7 0 9.8 2.2 12.3 6.5V22.3h-8.6v-5.6h15.8v50.6h6v5.5zM493.2 56v-4.4c-.1-3-1.2-5.5-3.2-7.3s-4.4-2.8-7.2-2.8c-3.6 0-6.3 1.3-8.2 3.9-1.9 2.6-2.8 5.8-2.8 9.6 0 4.1 1 7.3 3 9.5s4.5 3.3 7.4 3.3c3.2 0 5.8-1.3 7.8-3.8 2.1-2.6 3.1-5.3 3.2-8zm53.1-1.4c0 5.6-1.8 10.2-5.3 13.7s-8.2 5.3-13.9 5.3-10.1-1.7-13.4-5.1c-3.3-3.4-5-7.9-5-13.5 0-5.3 1.6-9.9 4.7-13.7 3.2-3.8 7.9-5.7 14.2-5.7s11 1.9 14.1 5.7c3 3.7 4.6 8.1 4.6 13.3zm-7.7-.2c0-4-1-7.2-3-9.5s-4.8-3.5-8.2-3.5c-3.6 0-6.4 1.2-8.3 3.7s-2.9 5.6-2.9 9.5c0 3.7.9 6.8 2.8 9.4 1.9 2.6 4.6 3.9 8.3 3.9 3.6 0 6.4-1.3 8.4-3.8 1.9-2.6 2.9-5.8 2.9-9.7zm45 5.8c-.4 3.2-1.9 6.3-4.4 9.1-2.5 2.9-6.4 4.3-11.8 4.3-5.2 0-9.4-1.6-12.6-4.8-3.2-3.2-4.8-7.7-4.8-13.7 0-5.5 1.6-10.1 4.7-13.9 3.2-3.8 7.6-5.7 13.2-5.7 2.3 0 4.6.3 6.7.8 2.2.5 4.2 1.5 6.2 2.9l1.5 9.5-5.9.7-1.3-6.1c-2.1-1.2-4.5-1.8-7.2-1.8-3.5 0-6.1 1.2-7.7 3.7-1.7 2.5-2.5 5.7-2.5 9.6 0 4.1.9 7.3 2.7 9.5 1.8 2.3 4.4 3.4 7.8 3.4 5.2 0 8.2-2.9 9.2-8.8l6.2 1.3zm34.7 1.9c0 3.6-1.5 6.5-4.6 8.5s-7 3-11.7 3c-5.7 0-10.6-1.2-14.6-3.6l1.2-8.8 5.7.6-.2 4.7c1.1.5 2.3.9 3.6 1.1s2.6.3 3.9.3c2.4 0 4.5-.4 6.5-1.3 1.9-.9 2.9-2.2 2.9-4.1 0-1.8-.8-3.1-2.3-3.8s-3.5-1.3-5.8-1.7-4.6-.9-6.9-1.4c-2.3-.6-4.2-1.6-5.7-2.9-1.6-1.4-2.3-3.5-2.3-6.3 0-4.1 1.5-6.9 4.6-8.5s6.4-2.4 9.9-2.4c2.6 0 5 .3 7.2.9 2.2.6 4.3 1.4 6.1 2.4l.8 8.8-5.8.7-.8-5.7c-2.3-1-4.7-1.6-7.2-1.6-2.1 0-3.7.4-5.1 1.1-1.3.8-2 2-2 3.8 0 1.7.8 2.9 2.3 3.6 1.5.7 3.4 1.2 5.7 1.6 2.2.4 4.5.8 6.7 1.4 2.2.6 4.1 1.6 5.7 3 1.4 1.6 2.2 3.7 2.2 6.6zM197.6 73.2h-17.1v-5.5h3.8V51.9c0-3.7-.7-6.3-2.1-7.9-1.4-1.6-3.3-2.3-5.7-2.3-3.2 0-5.6 1.1-7.2 3.4s-2.4 4.6-2.5 6.9v15.6h6v5.5h-17.1v-5.5h3.8V51.9c0-3.8-.7-6.4-2.1-7.9-1.4-1.5-3.3-2.3-5.6-2.3-3.2 0-5.5 1.1-7.2 3.3-1.6 2.2-2.4 4.5-2.5 6.9v15.8h6.9v5.5h-20.2v-5.5h6V42.4h-6.1v-5.6h13.4v6.4c1.2-2.1 2.7-3.8 4.7-5.2 2-1.3 4.4-2 7.3-2s5.3.7 7.5 2.1c2.2 1.4 3.7 3.5 4.5 6.4 1.1-2.5 2.7-4.5 4.9-6.1s4.8-2.4 7.9-2.4c3.5 0 6.5 1.1 8.9 3.3s3.7 5.6 3.7 10.2v18.2h6.1v5.5zm42.5 0h-13.2V66c-1.2 2.2-2.8 4.1-4.9 5.6-2.1 1.6-4.8 2.4-8.3 2.4-4.8 0-8.7-1.6-11.6-4.9-2.9-3.2-4.3-7.7-4.3-13.3 0-5 1.3-9.6 4-13.7 2.6-4.1 6.9-6.2 12.8-6.2s9.8 2.2 12.3 6.5V22.7h-8.6v-5.6h15.8v50.6h6v5.5zm-13.3-16.8V52c-.1-3-1.2-5.5-3.2-7.3s-4.4-2.8-7.2-2.8c-3.6 0-6.3 1.3-8.2 3.9-1.9 2.6-2.8 5.8-2.8 9.6 0 4.1 1 7.3 3 9.5s4.5 3.3 7.4 3.3c3.2 0 5.8-1.3 7.8-3.8 2.1-2.6 3.1-5.3 3.2-8zm61.5 16.8H269v-5.5h6V51.9c0-3.7-.7-6.3-2.2-7.9-1.4-1.6-3.4-2.3-5.7-2.3-3.1 0-5.6 1-7.4 3s-2.8 4.4-2.9 7v15.9h6v5.5h-19.3v-5.5h6V42.4h-6.2v-5.6h13.6V43c2.6-4.6 6.8-6.9 12.7-6.9 3.6 0 6.7 1.1 9.2 3.3s3.7 5.6 3.7 10.2v18.2h6v5.4h-.2z" class="logo-text"></path></svg>
In the event of content not being already cached, a race with multiple IPFS gateways is performed. As soon as one gateway successfully responds, its response is forwarded to the user and added to Cloudflare Cache.

Check out the Edge Gateway documentation.

🪐 The IPFS gateway for web3.storage is not "another gateway", but a caching layer that sits on top of existing IPFS public gateways.
google.search - QmSZiAjD2pXv25caUj61RyzxYNzrKqL8HQLGt8XBhpjBT6
Sovrin Provisional Trust FrameworkSovrin Board of Trustees28 June 2017Sovrin.org
sovrin identity for all
Indy has its own distributed ledger based on RBFT.
ledeger or hashtable
provide a self-sovereign identity ecosystem on top of a distributed ledger.
The server portion of a distributed ledger purpose-built for decentralized identity.

Indy Working Group Calls The Indy Working Group Calls take place every Thursday at 3:00 PM UTC via Zoom.
Developers
SSI Metrics Dashboards


enabling self-sovereign identity on the internet
IndyWiki: Web3 Native Tinkerable Wiki. You do not go to some place to collaborate using a Wiki.
Web3Native Tinkerable Wiki bootstrapping the IndyVerse
Highlights, Notes & Annotations:
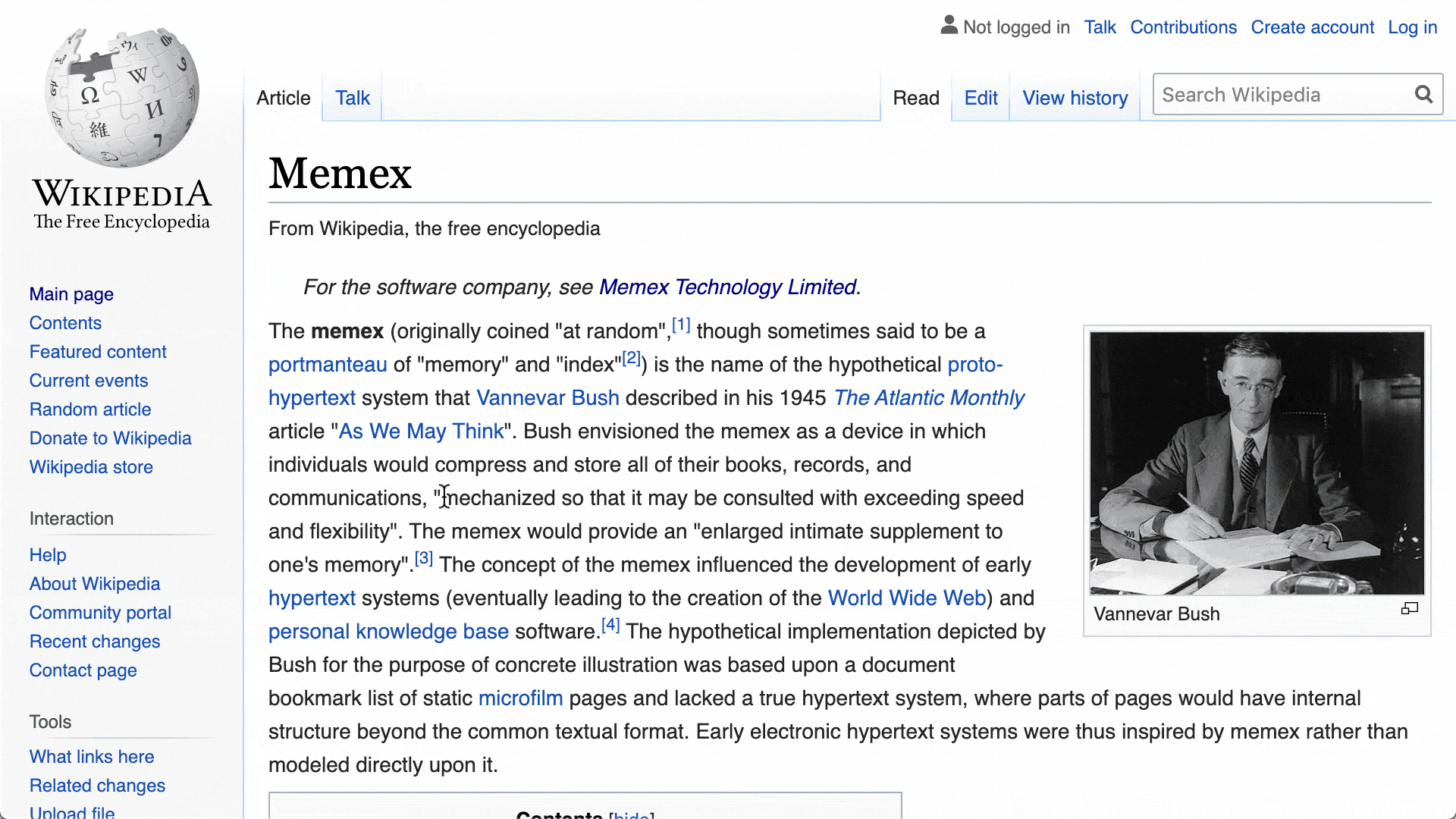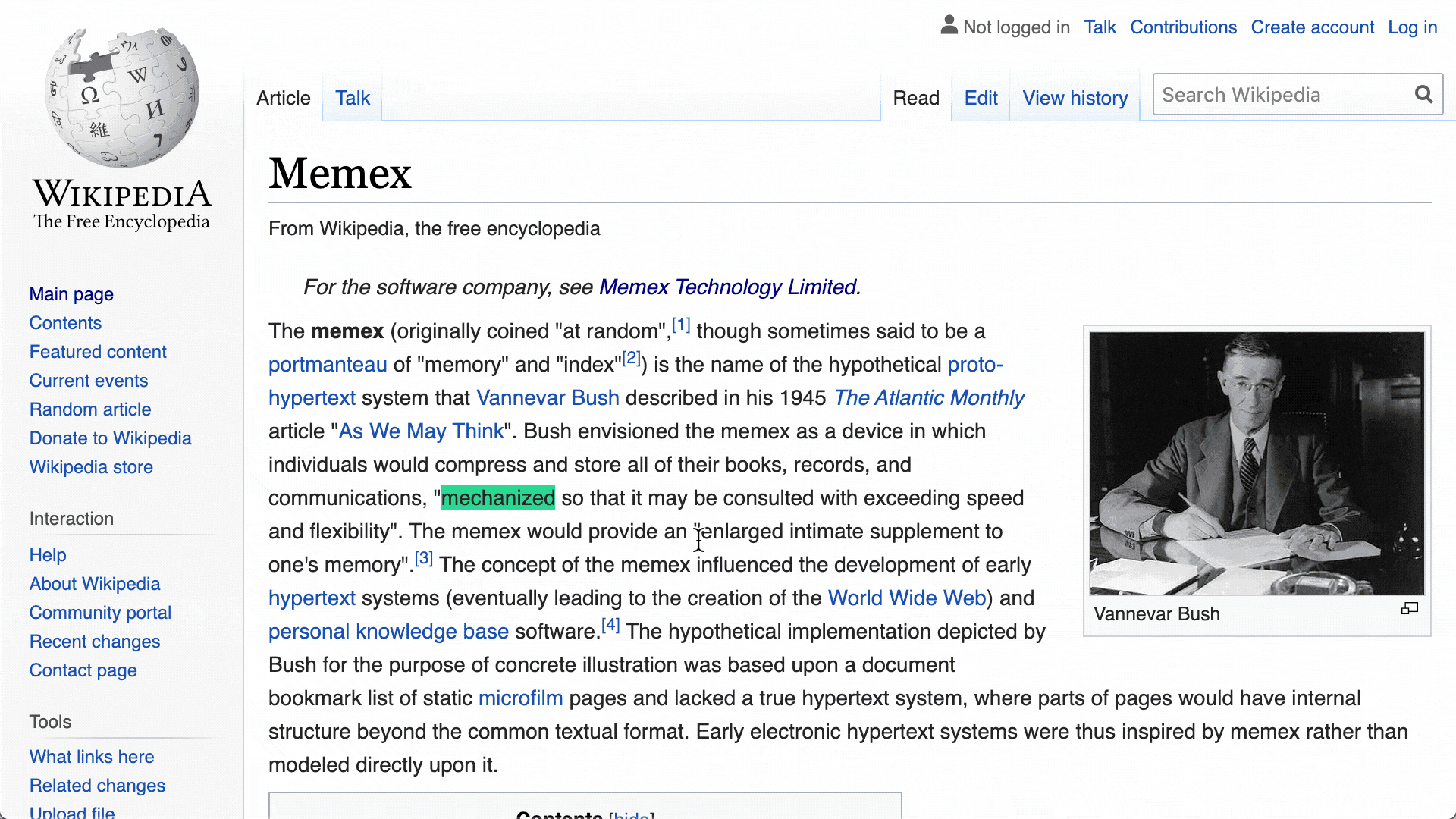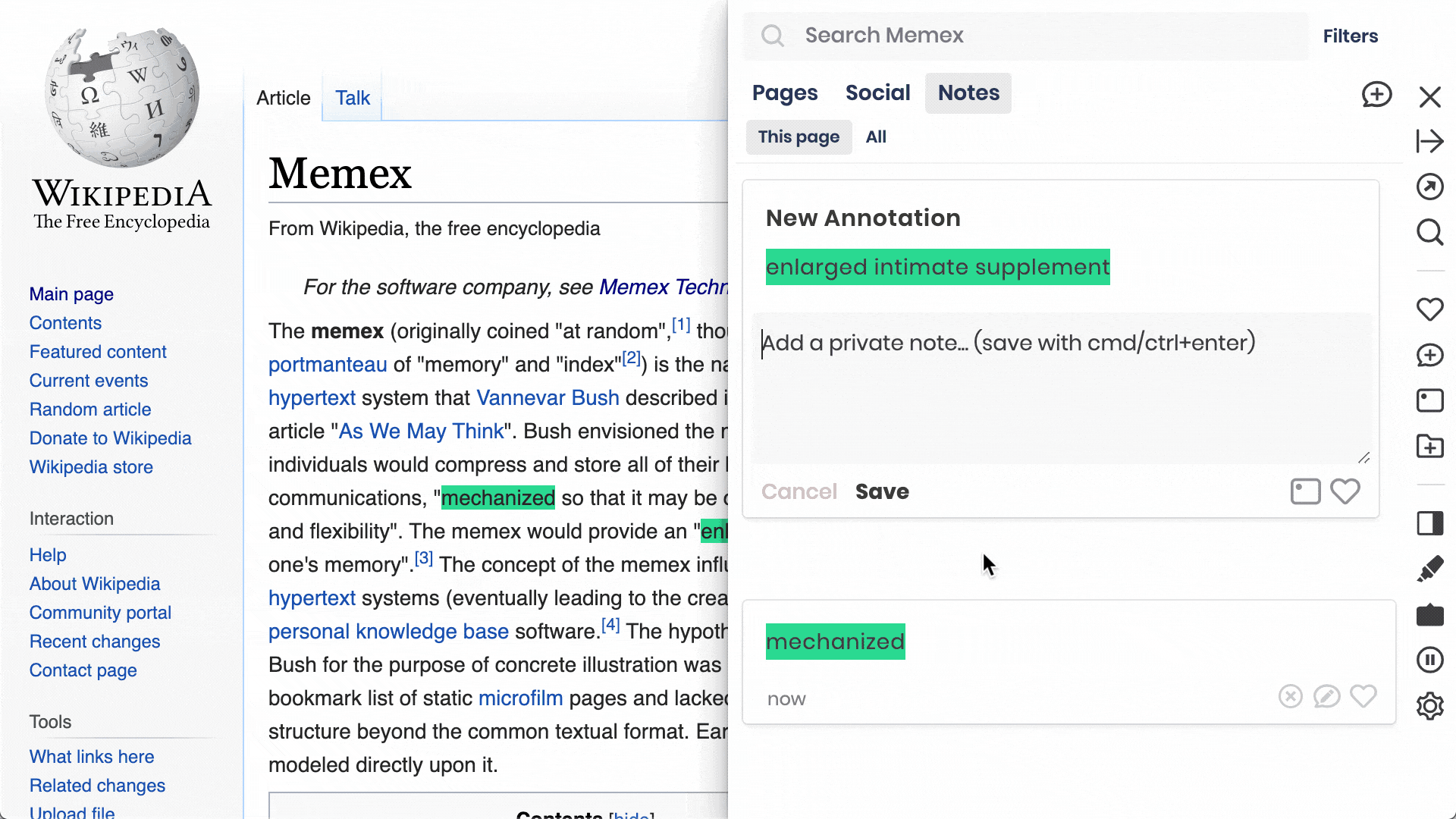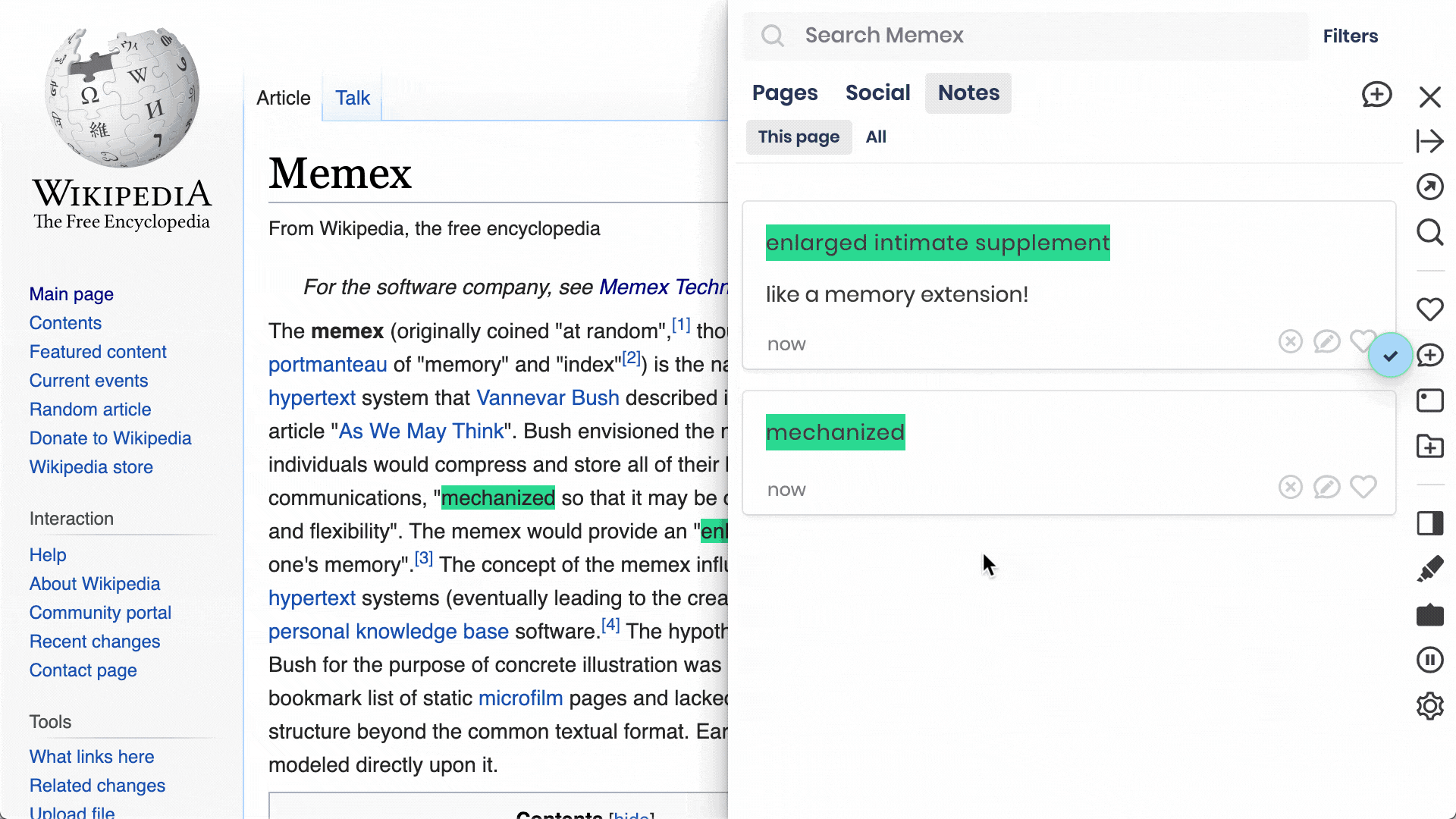
Browser extension to curate, annotate, and discuss the most valuable content and ideas on the web. As individuals, teams and communities.
linux distro to get on a pendrive
Shut down the computer and start on your Tails USB stick instead of starting on Windows, macOS, or Linux. Tails leaves no trace on the computer when shut down.
just like knoppix of old
InstantOpen Source App Hosting Run the finest Open Source web apps from just $1/month
)
PikaPods
)
searched.for - tools
⚙
search.for: tools
Carousel Horse Emoji 🎠
searched.for : go