source
- https://www.universalfreemasonry.org/en/article/ordo-ab-chao

- Jan 2024
-
www.universalfreemasonry.org www.universalfreemasonry.org
-
-
docs.filebase.com docs.filebase.com
-
Filebase's Pricing Model

-
-
docs.ipfs.tech docs.ipfs.tech
-
Kubo RPC API v0 reference
When a Kubo IPFS node is running as a daemon, it exposes an HTTP RPC API that allows you to control the node and run the same commands you can from the command line.
-
-
stackoverflow.com stackoverflow.com
-
www.startpage.com www.startpage.com
-
https://stackoverflow.com/questions/9755841/how-can-i-change-the-version-of-npm-using-nvm How can I change the version of npm using nvm? - Stack Overflow Mar 18, 2012 ... In order to change your npm version when using nvm, you must install your npm version only inside the folder of the desired Node.js version. For ...
-
-
symbl.cc symbl.cc
-
Person Doing Cartwheel Emoji (Person Cartwheeling) 🤸

-
-
www.freecodecamp.org www.freecodecamp.org
-
How to Install NVM on Linux and Mac
curl -o- https://raw.githubusercontent.com/nvm-sh/nvm/v0.39.1/install.sh | bash
-
-
docs.digitalocean.com docs.digitalocean.com
-
How to Connect to your Droplet with OpenSSH
openssh
-
-
linuxize.com linuxize.com
-
How to Create Users in Linux (useradd Command)
-
-
bitsavers.org bitsavers.org
-
the syntax of the languages were more suited toNLS linkage conventions, and the files themselves werebetter structured, we might again reach a point of feelingthat the structure is well understood, and the effect ofchanges in code can be properly predicted
NLS linkage conventions
for - hyper link - hyperlink - what's in a link? - keep the links outside the file
link
the original hyperlink that was active and allowed dynamic exploration of linked context with appropriate viewspecs
Now in Plex or Trail Mark.s the identity of a high resolution addressable content (the addressed is derived from the plexmark trailmark being present in an outline
whether it is in its own document or a clueon or plexon or a clue structure or plex structure outline within the context of a plexon clueon page virtual document
is not couple with a view spec but the very identity of a document carries marks that indicate - intentional - semantic - symmathetic - self-describing
qualifier marks tht in turn are amenable to interpretation by humans and machines such that "viewspec" or rahter "miorphic interpretations" can be associated with them
-
NETWORK DECODE-ENCODE LANGUAGE
section
-
do away with listing by organizing thedocumentation and code into an easily accessible, monolithic,structured NLS file.
becuase of the immanent structuring no linear listing were ever used in Meta-Lisp in practice, dynamic navigation
although a complete listing via depth first traversal was always possible and told the complete story
-
If the SPL compiler is in Tree Meta, the parse rules willcontain only parse information and node-building directions.This should make them much more readable, a feature alwayswanted by those who try to figure out commands of NLS byreading the code in the SPLs
parse rule
only contain parse information and node-building
just like MetaLISP!
-
UNCRUNCH program
query - inverse of weave in literate programming?
-
a single, monolithicprogramming and doctmentation structure for a large program.
monolithic programming and documentation structure for large programs
devolved into Literate Programming
future iutopoietic holonimorphic virtual collaborative documents articulating intentional structures amenable to the pun of lively interaction and transformations
-
ower of TreeMeta to do its top-down tree search
top down tree search
TDPL
-
the compiler cannot be checked out without a newTree ~1eta because it needs features in the metalanguagewhich are not currently in Tree Meta
bootsrap
-
It is hard toguess how long it will take to do the job, since we do notyet know what we want to do
how long##do not yet know what we want to do
-
We have finally figured out a way of writing the parse andunparse rules for the MOL compiler in Tree Meta and notoverflowing the push-down stacks during compilation. Now thatwe have a solution, it would be satisfying to have all of ourcompilers written in the same metalanguage
Everything in Tree Meta (|V)
one meta language to create them all
The great metaprogenitor
-
we would like to work out a method of compilationthat substitutes the tree structure of NLS files for the phrasestructure of the MOL and SPLs. This is virtually impossibleunless the MOL is in Tree Meta and the changes can be done inone central place, namely the Tree Meta library, for all theexperimental compilers
phrase structure Tree Meta
-
figure out what a pieceof code is "supposed" to do
figure out supposed to do
-
the syntax ofthe language closer to the intentions of the coder.
intention of the coder
-
a total planned rewrite of all three compilers offersthe most economical long-tern solution.
Pancake philosophy the first one should be thrown away
-
Graphic Oriented Documentation OutputSystem
GODOS
-
the statementnumber must 'begin with a digit, and it must be followed by atleas t one space
statement number must begin with a digit and followed by at least one space
-
"outline" format
listicles
hierarchical structure
-
Each sequence is called a "field. 1t
statement sequence is a field
-
Typewriter-Oriented Documentation Aid System (TODAS)
primer user guide
-
The user can retrace his steps within a file by using the Jumpto Return and Jump to Ahead commands
trail following back and forward
-
The system keeps track of all jumps, both within a given file(intrafile) and from one file to another (interfile).
Links were bid-directional and permanent right at the start!
-
USERNAME,FILENAME,STATEMENTSPEC:VIEWSPECS
clue name
-
A link is a string of text, in a special format, that specifies apoint to be jumped to and a set of VIEWSPECs to be used.
link
-
ump to Identity
is the most basic means of "moving about" within a file. A statement is selected, view-control parameters are set (if desired), and upon execution the display is re-created with the selected statement at the top and the new view parameters (if any) in effect
-
nIE NLS LINKING FEATURE
NLS linking
-
Experience in Collaborative Techniques
collaborative techniques
-
local sinulation of fcedbHck, construction ofmessages to go across the >Jeth!ork, and trans lation of messagesrecei ved from across t.he Netwol~k
message passing end interpretation
-
The Net\'Jork Decode-Encode Language (DEL) is in the design stages.This is a special-purpose InnU1Hl0e fOl- \:ritin£:; pr0E;rams for userin teractioll wi til rePlote sys tCTtlS .
network decode-encode language DEL
programs for user interaction with remote systems
-
valuab Ie to the experimental scope
~e f'eel that it ...·i 11 be very valuab Ie to the experimental scope and progr·pss of the nett'lork if critical documentation can be flexihly and rapidly updated and then rapidly and cheaply distributed. \~e intend to handle text, Rraphs. line figures, tah 1e$ and eqllat ions
-
Experimentation with these techniques
early stage demo
-
perimenting also \Vi th work-space layout
experimenting
-
User neptIs of concern to the ;'-He are (lS fo I1m<!s
user needs
-
-
www.amp-what.com www.amp-what.com
-
https://bafkreidygczgwdxg6nordbcx6rhgdfq2itmisp7vdmbpr7hqrymiv533by.ipfs.dweb.link/?filename=Predicate+%C2%BB+Object+%C2%AB+Enclosuse.txt
-
«\0000ab««"\u00AB"U+ab%C2%AB«left-pointing double angle quotation mark
«
-
»right-pointing double angle quotation mark
»
-
-
-
Try to avoid using years, version numbers, or other naming patterns that date a file
The opposite is needed post hoc
-
-
www.youtube.com www.youtube.com
-
ground atomic formula which is just a 02:14:09 the name of a relation and a few arguments
rule macro predicate see
ground atomic formula - That's What's in a PlexMarked Name for a Clue/Page
Clueon, Plexon which is a named node for an associative complex both incoming trails and outgoing immediate neighbourhood of structured complexes
in a Curryed form - applicative/interpretative order
-
-
docs.digitalocean.com docs.digitalocean.com
-
How do I install an SSL Certificate on a Droplet?
digitalocean SSL hosting
-
-
create-react-app.dev create-react-app.dev
-
https://cra.link/deployment
``` The project was built assuming it is hosted at /. You can control this with the homepage field in your package.json.
The build folder is ready to be deployed. You may serve it with a static server:
npm install -g serve serve -s build
Find out more about deployment here:
https://cra.link/deployment
chitchatter@0.0.0 build:sdk parcel build sdk/sdk.ts --dist-dir build --no-content-hash
✨ Built in 2.12s
build/sdk.js 8.03 KB 740ms ```
-
-
github.com github.com
-
On non-GitHub hosts
Build the app with PUBLIC_URL="https://your-domain-here.com" npm run build , and then serve the build directory. Any static file serving solution should work provided it is using a secure context.
for - self-host
-
npm start
Runs the front end app in the development mode. Uses public WebTorrent trackers. Open http://localhost:3000 to view it in your browser.
The page will reload when you make changes. You may also see any lint errors in the console.
-
embed the app as a Web Component called <chat-room />.
-
self-host your own Chitchatter instance.
self-host
-
-
blog.logrocket.com blog.logrocket.com
-
nvm install --<the node version>
install specific version of node
-
How to switch Node.js versions with NVM

-
-
developer.mozilla.org developer.mozilla.org
-
-
npx create-react-app my-react-app
just do this
-

-
-
www.startpage.com www.startpage.com
-
Setting Up Your Development Environment for React - Medium
-
https://www.startpage.com/do/dsearch?q=setup+for+react+development&cat=web&language=english
-
-
medium.com medium.com
-
-
State Management in Web Components: Crafting Cohesive and Scalable Solutions

-
-
www.startpage.com www.startpage.com
-
-
State Management in Web Components: Crafting Cohesive and ... Oct 3, 2023 ... ... react to state changes, triggering re-renders or side effects. ... Overview: When multiple components need to access or modify the same state, a ...
https://www.startpage.com/do/dsearch?q=react+webcomponent+modify+state&cat=web&language=english
-
-
www.google.co.uk www.google.co.uk
-
Set Up Session Replay for ReactSentry Docshttps://docs.sentry.io › platforms › javascript › guidesSentry Docshttps://docs.sentry.io › platforms › javascript › guidesSampling begins as soon as a session starts. replaysSessionSampleRate is evaluated first. If it's sampled, the replay recording will begin. Otherwise, ...Missing: tweak | Show results with: tweak
-
Aug 11, 2016 — This way, you don't lose any of your state which is especially useful if you are tweaking the UI. ... record and replay, without any buy-in from ...
-
-
docs.sentry.io docs.sentry.io
-
Set Up Session Replay
<svg xmlns="http://www.w3.org/2000/svg" viewBox="0 0 75 75"><g height="75" width="75" class="loader-spin"><path d="M7.8 49.78c-1.75 2.88-3.19 5.4-4.35 7.56a3.9 3.9 0 0 0 3.34 6h18.86a25.75 25.75 0 0 0-12.87-22.19c1.9-3.17 5.12-9 6.32-11a38.47 38.47 0 0 1 19.14 33.23h12.63a50.79 50.79 0 0 0-25.51-44C29.65 12 32.38 7 33.89 4.64a4 4 0 0 1 6.66 0C42 7 69.53 54.8 71 57.34a4 4 0 0 1-3.75 6h-6.79" fill="none" stroke="currentColor" class="loader-stroke loading" stroke-width="5"></path></g></svg>
-
-
auth0.com auth0.com
-
Bootstrapping a React project
-
-
github.com github.com
-
Test Automation Made Simple
-
-
github.com github.com
-
-
ipfs.indy0.net ipfs.indy0.net
-
Session replay and analytics tool you can self-host. Ideal for reproducing issues, co-browsing with users and optimizing your product.
-
🦔 PostHog provides open-source product analytics, session recording, feature flagging and A/B testing that you can self-host.
-
The simplest option for recording and replaying user journeys

-
Full Session Replays
-
record and replay the web
-
-
github.com github.com
-
github.com github.com
-
🦔 PostHog provides open-source product analytics, session recording, feature flagging and A/B testing that you can self-host.
-
-
github.com github.com
-
The simplest option for recording and replaying user journeys

-
-
github.com github.com
-
Full Session Replays
-
-
github.com github.com
-
head to the Chrome Web Store to install
chorme web store
-
from - search.google
-
About Automated functional testing via the Chrome DevTools Protocol. Easy to use and open source. Generates unique CSS and Xpath selectors. Outputs code for multiple testing frameworks, including Jest, Puppeteer, Selenium Webdriver and Cypress.
-
-
-
-
Dive Into Events
-
-
-
ipfs.indy0.net ipfs.indy0.net
-
Session replay and analytics tool you can "truly" self-host. Ideal for reproducing issues, co-browsing with users and optimizing your product. react ..
-
OpenReplay: Open-Source Session Replay & Analytics
-
Standalone, framework-agnostic JavaScript library that enables recording, replaying, and stubbing HTTP interactions.
-
Open Source record and playback test automation for the web. electron ... Open-source and privacy-friendly. react open-source mac screenshot app typescript .
record · GitHub Topics to
-
Netflix/pollyjs: Record, Replay, and Stub HTTP Interactions.
-
-
session-replay · GitHub Topics
-
tomgallagher/RecordReplay
Automated functional testing via the Chrome DevTools Protocol. Easy to use and open source. Generates unique CSS and Xpath selectors.
-
-
netflix.github.io netflix.github.ioPolly.JS2
-
github.com github.com
-
record Here are 449 public repositories matching this topic..
-
-
openreplay.com openreplay.com
-
-
Prior Art
The "Client Server" API of Polly is heavily influenced by the very popular mock server library pretender.
-
Use Polly's client-side server
client0side server
to modify or intercept requests and responses to simulate different application states (e.g. loading, error, etc.).
-
-
-
docdrop.org docdrop.org
-
-
www.startpage.com www.startpage.com
-
https://github.com/tomgallagher/RecordReplay tomgallagher/RecordReplay - GitHub Automated functional testing via the Chrome DevTools Protocol. Easy to use and open source ... No coding skills are required to record and to replay tests.
-
https://www.freecodecamp.org/news/use-typescript-with-react/ How to Use TypeScript with React - freeCodeCamp Nov 15, 2023 ... If the file does not contain any JSX-specific code, then you can use the .ts extension instead of the .tsx extension. To create a component in ...
-
-
www.youtube.com www.youtube.com
-
Record/Replay Demonstration Video
-
-
ecosystem-wg.notion.site ecosystem-wg.notion.site
-
Getting Started With IPFS & Filecoin

-
-
docs.filebase.com docs.filebase.com
-
IPFS DesktopLearn how to configure IPFS Desktop for use with Filebase.

-
-
www.pinata.cloud www.pinata.cloud
-
Kubo vs Helia vs Elastic-IPFS: Comparing the major IPFS implementations

-

-
-
greattransition.org greattransition.org
-
What's Next for the Global Movement?

-
-
www.freecodecamp.org www.freecodecamp.org
-
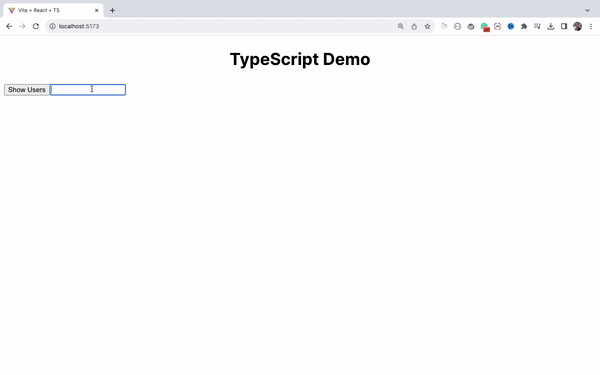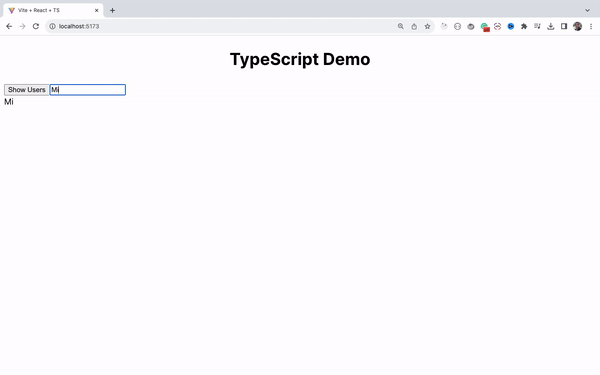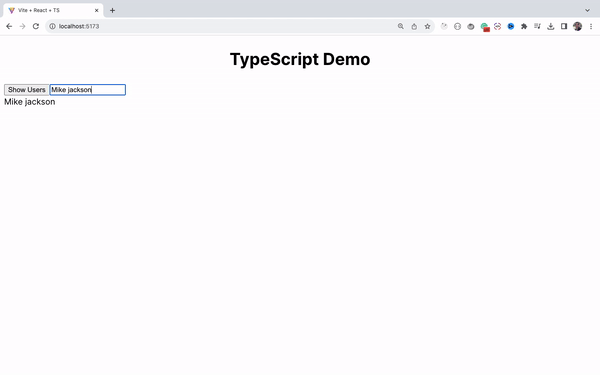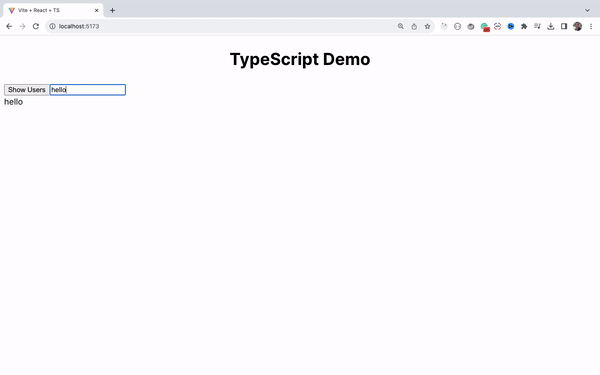
How to Handle the Change Event
-
-
ipfs.indy0.net ipfs.indy0.net
-
Web Intents
-
-
en.wikipedia.org en.wikipedia.org
-
a standalone protocol for describing multicast sessions
=on - multicast.sessions
-
The set of properties and parameters is called a session profile.
= on - session.profile
-
-
-
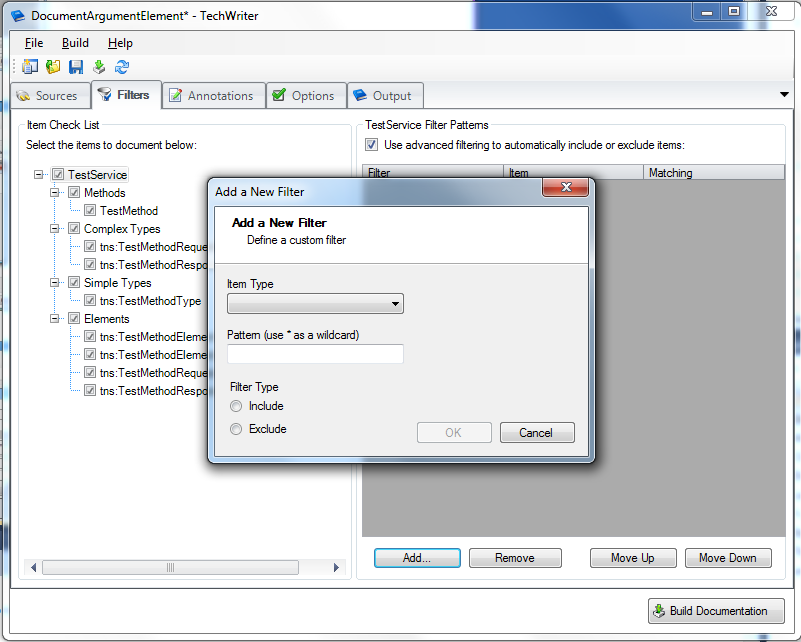
for - Quarksoft - techwriter

-
-
en.wikipedia.org en.wikipedia.org
-
CAP theorem

n a way IPFS going against the CAP theorem which says you cannot have Consistency Availability and Partition tolerance all three
As we can see availability is indeed very problematic. But as one of the great talks pointed out the more people join the IPFS networks availability will improve exponentially. In terms of ipns as a protocol when combined with dnsink seems to be giving us a pretty good availability which is a half way house
alternatively use this
from : https://hyp.is/k9U7pPxNEe2ZYAf5Jr2Xlg/docs.ipfs.tech/concepts/ipns/
-
-
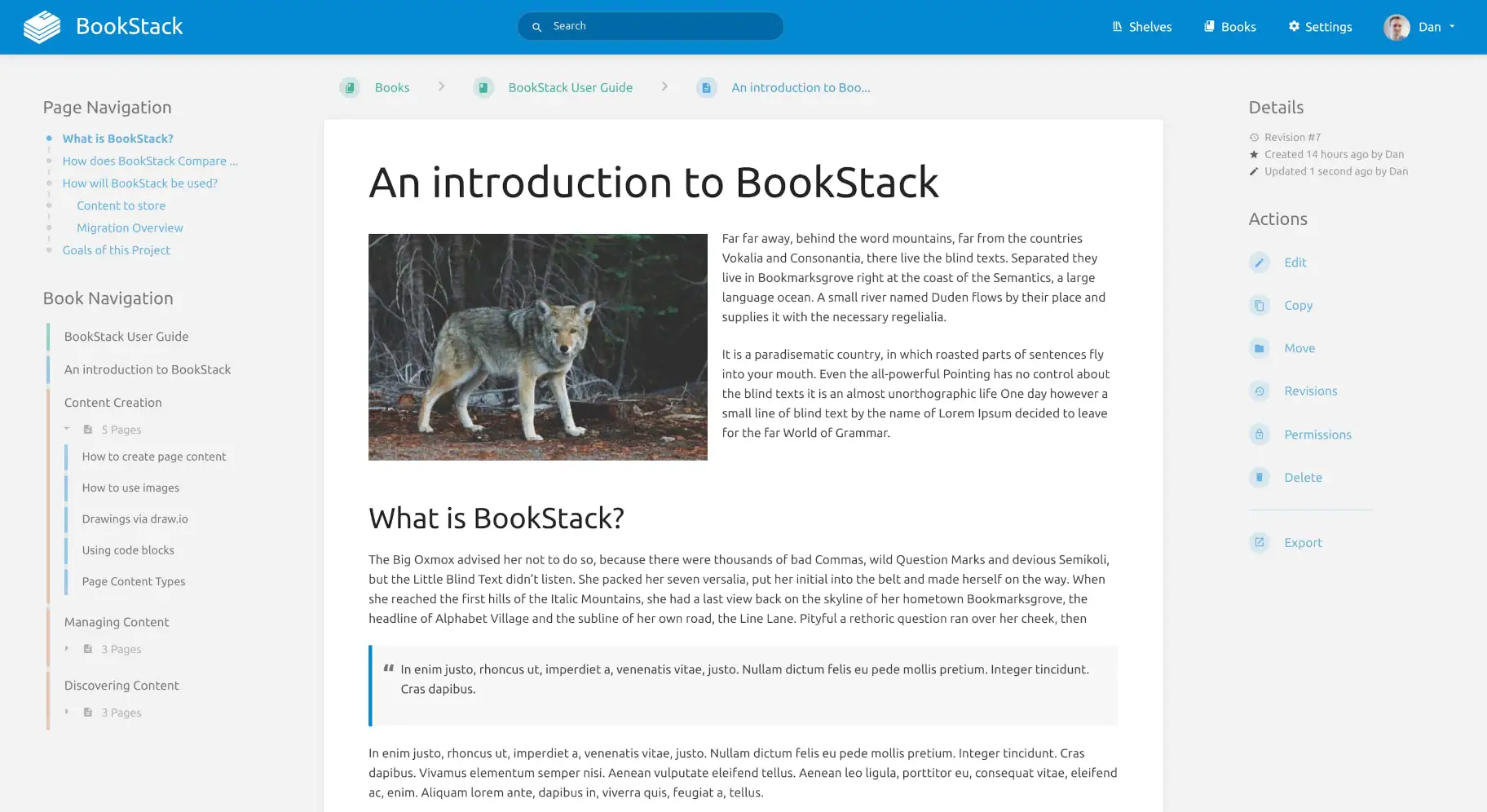
www.bookstackapp.com www.bookstackapp.com
-
BookStack is a simple, self-hosted, easy-to-use platform for organising and storing information.
-
-
ipfs.indy0.net ipfs.indy0.net
-
from hylo self.link

-
-
-
Conformal Mapping -- from Wolfram MathWorldWolfram MathWorldhttps://mathworld.wolfram.com › ConformalMappingWolfram MathWorldhttps://mathworld.wolfram.com › ConformalMappingby EW Weisstein · 2000 · Cited by 14 — A conformal mapping, also called a conformal map, conformal transformation, angle-preserving transformation, or biholomorphic map, is a
-
-
ipfs.indy0.net ipfs.indy0.net
-
math.stackexchange.com math.stackexchange.com
-
holomorphic functions are conformal: they preserve angles between curves (this is a fifth, partially independent, way to think about complex differentiable functions.)
holomorphigenic plex spaces
preserve the spanning structure of trailmarks
thought vectors in hyperdocument spaces
-
-
github.com github.com
-
for - tech.mix - Indy.Web
-
-
symbl.cc symbl.cc
-
Ideographic Telegraph Symbol for January ㋀
㋀
-
-
-
Clipboard Emoji (List) 📋
📋
-
-
-
Eyes Emoji (Eyeballs) 👀
👀
-
-
web.archive.org web.archive.org
-
Round Trip Website Authoring

-
-
techwriter.me techwriter.me
-
to - https://hypothes.is/a/q8Yy2rgjEe6_pG8CGfrV5w - https://web.archive.org/web/20240121055817/https://techwriter.me/doc/TechWriterUserGuide/UserGuide.htm
-
Take Control of Your IT Documentation with TechWriter ®




-
-
web.archive.org web.archive.org
-
TechWriter is a documentation authoring tool that automatically generates documentation for databases, XML schemas, web services and more. With minimal effort, you can use TechWriter to create documentation that captures the information locked inside your IT projects with the accuracy and completeness of an experienced technical writer.

-
TechWriter is a documentation authoring tool that
TechWriter is a documentation authoring tool that automatically generates documentation for - databases, - XML schemas, - web services and more.
With minimal effort, you can use TechWriter to create - documentation
that captures the information locked inside your - IT projects
with the - accuracy and - completeness
of an experienced technical writer.
-
-
techwriter.me techwriter.me
-
-
TechWriter is a documentation authoring tool that automatically generates documentation for databases, XML schemas, web services and more.
Flip that!
-
-
-
-
Visual Tour of TechWriter

-
-
techwriter.me techwriter.me
-
Round Trip Database Authoring

-
-
www.pinata.cloud www.pinata.cloud
-
Collaborate with your entire team, all under one account
One Account
-
Introducing Pinata Workspaces

-
from - pinata-blog - thoughts worth pinning

-
-
www.pinata.cloud www.pinata.cloud
-
Thoughts Worth PinningFor crafty coders, ambitious creators and trailblazing businesses who want to grow (and have fun) with web3.

trailblazing businesses
-
-
fontawesome.com fontawesome.com
-
fontawesome plans

-
-
www.youtube.com www.youtube.com
-
Google might be proudly say okay we're doing a lot to help people find things out on that front error and okay but then who's 00:17:43 doing the job of really making better Maps understanding the footcare
Google and other search engine do a great job of auto-associative recall, i.e. giving you all the documents on the web that contain the terms you search for.
But as Engelbart asked back in 2007 at Google:
"Google might be proudly say, we are doing a lot to - help people find things - on the net frontier,
Who is doing the job of maybe - making better maps - understanding the frontier"

**blaze trails @ the net frontier augmenting mutual learning
new profession of trail blazers MEMEX
mutual learning
- Organizing mutul learning right at the edges of the
- "endless frontier" of knowledge
- responsibility to dream
- from inception, through indwelling and growth of understanding
- stemming from our increased capacities for honouring the complexitiesof our situation
- scaling synthesis and reach together
- within in networks of people who care,
- to the point of it being notable and part of
- "The Common Record".
Empower People at the edges - to do it for themselves, - share and have conversations around their - HyperMaps of their own(ed) collaborative mutual learning in the commons - at the edge of knowledge in the long tail of the emergent autonomous indy software internet - empower people with the problem for solve if for themeselves
- turning the Curse of LISP into blissful blessings
federate these conversations in emergent communities.
With the Wiki, Ward Cunningham gave us the ability to "create a new linked" page when you reach the edge of your knowledge"
What we need is for everybody to be able to do that, and at the same time have conversations with other people in an interest based emergent social networked thoughts and thinkers.
https://www.youtube.com/watch?v=xQx-tuW9A4Q&feature=youtu.be&t=1063
-
-
learn.microsoft.com learn.microsoft.com
-
Git settings
for name and email settings in git

-
-
code.visualstudio.com code.visualstudio.com
-
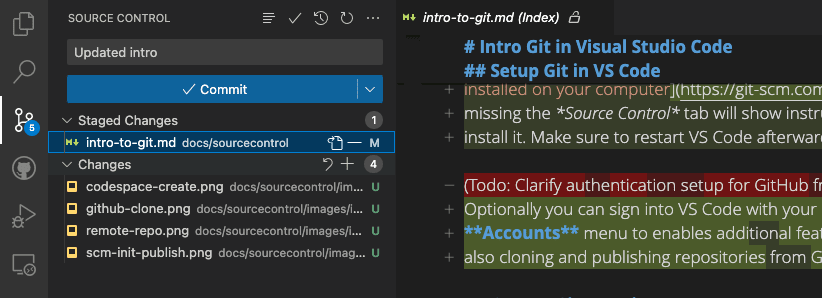
Introduction to Git in VS Code
-
-
-
Tails is a portable operating system that protects against surveillance and censorship.
-
-
www.educative.io www.educative.io
-
Progressive Web Apps (PWAs) are
highly advanced websites that
combine web technologies like - HTML, - CSS, and - JavaScript
with intelligent features such as:
Responsive design:
Adapts to - all devices and - screen sizes
for a consistent user experience.
Offline access:
Uses service workers - to work offline or - in low network conditions.
App-Like feel:
Can be installed on - home screens, - resembling native apps.
Manifest files:
Includes - metadata for app installation and - appearance.
Push notifications: Sends - updates and messages
even when not open.
Fast loading:
Optimized for - quick loading,
especially on slow connections.
-
How to perform a PWA performance auditing
-
-
obsproject.com obsproject.com
-
Display Capture capturing literally everything??

-
-
stackoverflow.com stackoverflow.com
-
VS Code's Source Control icon has gone missing, how do I get it back?

-
-
www.youtube.com www.youtube.com
-
How to create a Git repository with git init, GitHub and Git GUI tools Cameron McKenzie Cameron McKenzie 14.8K subscribers SubscribeSubscribed 15Sha
-
-
www.indiehackers.com www.indiehackers.com
-
Build an app with me: Youtube Bookmark Manager

-
-
ipfs.indy0.net ipfs.indy0.net
-
community.brave.com community.brave.com
-
Cannot use independent IPFS node with Brave nor configure the Brave node to use different port
Brave issue
-
-
github.com github.comHome2
-
from https://hyp.is/AFs6PrUEEe6ay-c4IYPy9w/www.thescottkrause.com/emerging_tech/neodigm55_ux_library/
-
Neodigm 55 Easy JavaScript Popups
-
-
www.thescottkrause.com www.thescottkrause.com
-
It's low-code, performant, responsive, and open source. Because it’s so easy to get started it is the perfect solution for quick landing pages, business accelerators, and event sites.
-
Neodigm 55 Low Code UX micro-library Scott C. Krause | Friday, Nov 25, 2022
from - https://hyp.is/HysQdrUCEe6HgDNGpn7Q4w/gist.github.com/neodigm/ffa4a9e22a5da14e2472274d476eaa55

-
-
gist.github.com gist.github.com
-
Now part of the Neodigm 55 UX micro-library
-
snackbar_toast.js
-
-
github.com github.com
-
self.link: neodigm - github - Scott.C.Krause
-
DataVis 👁️ UX 🍭 PWA 👁️ ThreeJS ✨ Vue..
neodigmToast
-
I code
- performant,
- functional,
- testable,
- future-proof, and
- trusted
what? - JavaScript, TypeScript, Vue, and SolidJS.
I've enchanted the UX for Abbott Laboratories, AbbVie, CDW, Corporate Express, Hyundai, Microsoft, and Sears.
-
Scott C. Krause neodigm
-
-
ipfs.indy0.net ipfs.indy0.net
-
ipfs.indy0.net ipfs.indy0.net
-
-
HTML Over the Wire - Scott C. Krausethescottkrause.comhttps://www.thescottkrause.com › curated-htmx-linksthescottkrause.comhttps://www.thescottkrause.com › curated-htmx-linksAug 5, 2023 — Is HTMX worth the effort to learn as a pragmatic skill? Yes ... browser automation. /* _____ / __ \ | / \/_ _ _ __ _ __ ___ ___ ___ ...
-
-
ipfs.indy0.net ipfs.indy0.net
-
HTML Over The Wire means that HTML, instead of JSON, is transported between the client and the server / API. Considered to be a simpler approach when compared to popular bloated reactive frameworks.
broader reactive frameworks
-
-
-
No accounts. 100% privacy.
Funded by happy users' donations.
No accounts 100% privacy
as a USP

-
No accounts. 100% privacy. Funded by happy users' donations.
**No accounts **
-
All-in-one tab session manager for Chrome Stay in the flow with saved workspaces and organised bookmarks. Get to tab zero in seconds.
from - HN privacy focused bookmarks manager
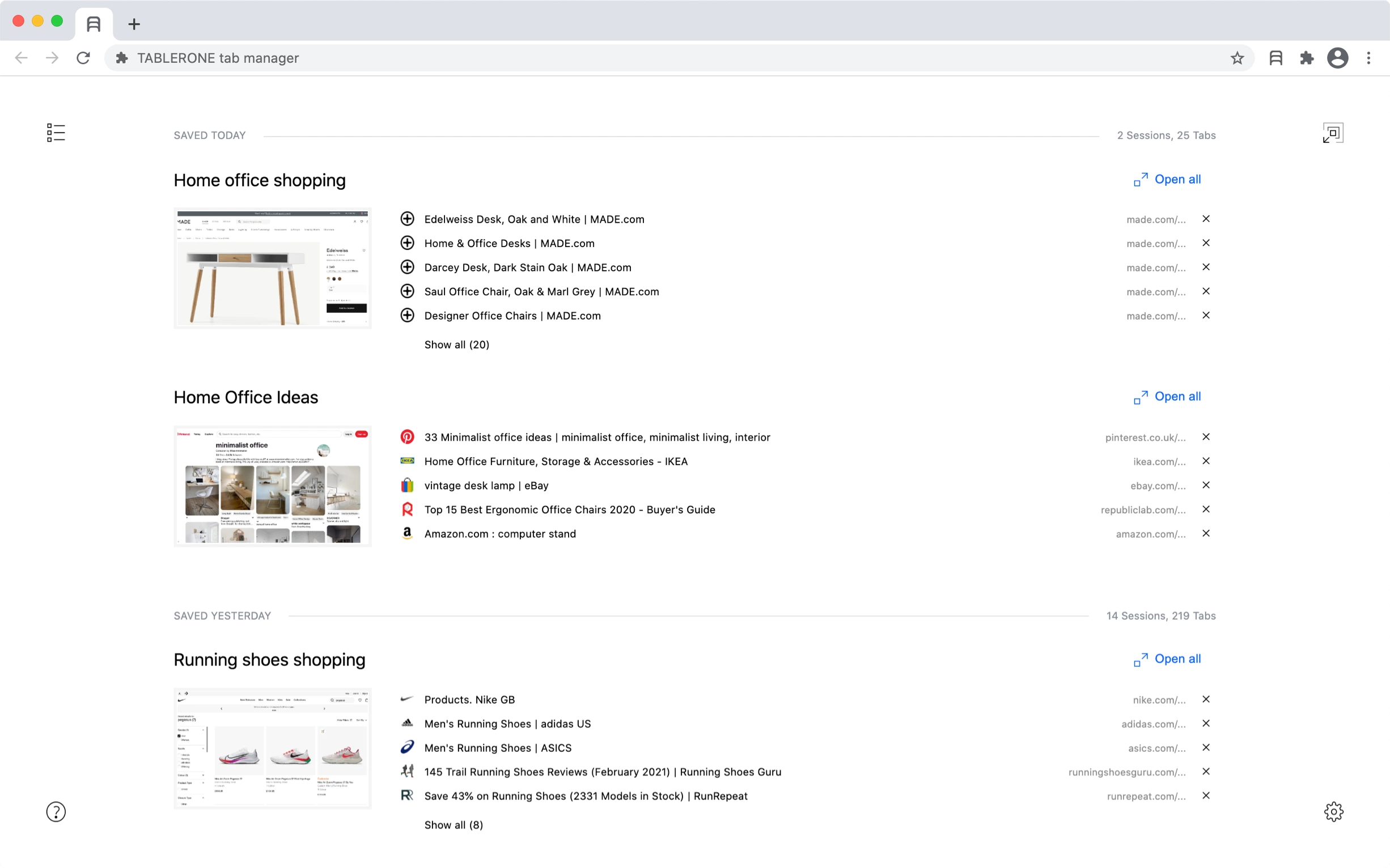
-
-
www.youtube.com www.youtube.com
-
Google Chrome - SAVE TAB GROUPS is now available - Keep your tabs organized!
23,794 views 23 Mar 2023 Google Google Chrome came out with the ability to add Tab Groups in April 2021. I know, I made a video on how to use Tab Groups. What was missing was the ability to Save the Tab Groups. You can now save Tab Groups if you turn on Chrome Flags. Chrome Flags are new or experimental features. This tells me soon Saved Tab Groups will be part of the Chrome browser. What are Tab Groups? Tabs in Chrome that are related. For example, Delta Air Lines, Southwest Airlines, Hilton, and Marriott may be grouped together under the Travel Group. Think of Tab Groups as Folders in File Explorer. Groups can be collapsed and expanded. They can be Saved, the new feature. Tab Groups that are saved will appear when Chrome is closed and re-opened. You need to Enable Tab Group Save in Flags.
How to enable Chrome flags? Open Chrome and copy and paste this into the address bar chrome://flags Screenshot https://drive.google.com/file/d/1-3vf...
-
-
news.ycombinator.com news.ycombinator.com
-
natannikolic 7 months ago | prev | next [–] https://tabler.one — Tablerone is a 100% private tabs, sessions, and bookmarks manager browser extension.
privacy focus zero knowledge encryption
-
-
-
ipfs.indy0.net ipfs.indy0.net
-
Ask HN: What's a good, privacy focused bookmark manager?News YCombinatorhttps://news.ycombinator.com › itemNews YCombinatorhttps://news.ycombinator.com › itemhttps://www.partizion.io/ is a great bookmark manager / session manager. Privacy focused, auto-saved sessions, and can add new links with the chrome extension.
-
What's the best way to manage 1000's of bookmarks?Reddit · r/chrome10+ comments · 10 months agoReddit · r/chrome10+ comments · 10 months agoChrome's bookmark manager is abysmal for organizing. A long time ago, Internet Explorer used to store it's bookmarks like files, meaning ...
-
Build an app with me: Youtube Bookmark ManagerIndie Hackershttps://www.indiehackers.com › post › build-an-app-w...Indie Hackershttps://www.indiehackers.com › post › build-an-app-w...Jan 26, 2021 — Why am I building it? · Pretty positive product hunt campaign product hunt campaign · Some traction bookmark it chrome store · No updates for a ..
-
-
-
10Posted byu/dix-hill10 months agoArchivedWhat's the best way to manage 1,000's of bookmarks?
-
-
github.com github.com
-
Install extension for Chrome Web Store
.png)
-


)



