luciancostinailenei/pretty-bookmarksGitHubhttps://github.com › luciancostinailenei › pretty-book...GitHubhttps://github.com › luciancostinailenei › pretty-book...pretty-bookmarks. A pretty Google Chrome bookmark manager created with productivity with mind. Why use it. It's a more clean and usable alternative to chrome
- Jan 2024
-
ipfs.indy0.net ipfs.indy0.net
-
-
search,google - pretty bookmarks manager
do.how - identify the page with a permanent self link - permanence is assured as the search result itself - is saved on the Permanent Web powered by IPFS - and indy0.net provides a way to load hypothesis social annotation to work on the page - the above link names this page using trailmarks - indicating that it is a result of doing a search with google - after the hyphen the keywords are given - use this convention to name a link to the page itself - the purpose being that we can even manually - copy this link the markdown wource in here - from the annotation 0 and use it in the pagers that it links to - when you annotate them to the pages - that we visit and annotate from here - so we can always answer the question - where (and how in details( did you find that site
-
-
github.com github.com
-
ipfs.indy0.net ipfs.indy0.net
-
-
Bookmark Miscellaneous Symbols and Pictographs
🔖

-
📑
-
Page with Circled Text Miscellaneous Symbols and Pictographs
🗟
-
Document with Picture Miscellaneous Symbols and Pictographs
🖻
-
Document with Text and Picture Miscellaneous Symbols and Pictographs
(◕‿◕) SYMBL
-
註 Ideograph explain; annotate; make entry CJK
Chinese symbol annotate
-
-
docs.cryptpad.org docs.cryptpad.org
-
Known caveats¶ No unique usernames
neither account names or display names are unique
-
-
docs.cryptpad.org docs.cryptpad.org
-
Code / Markdown
-
-
-
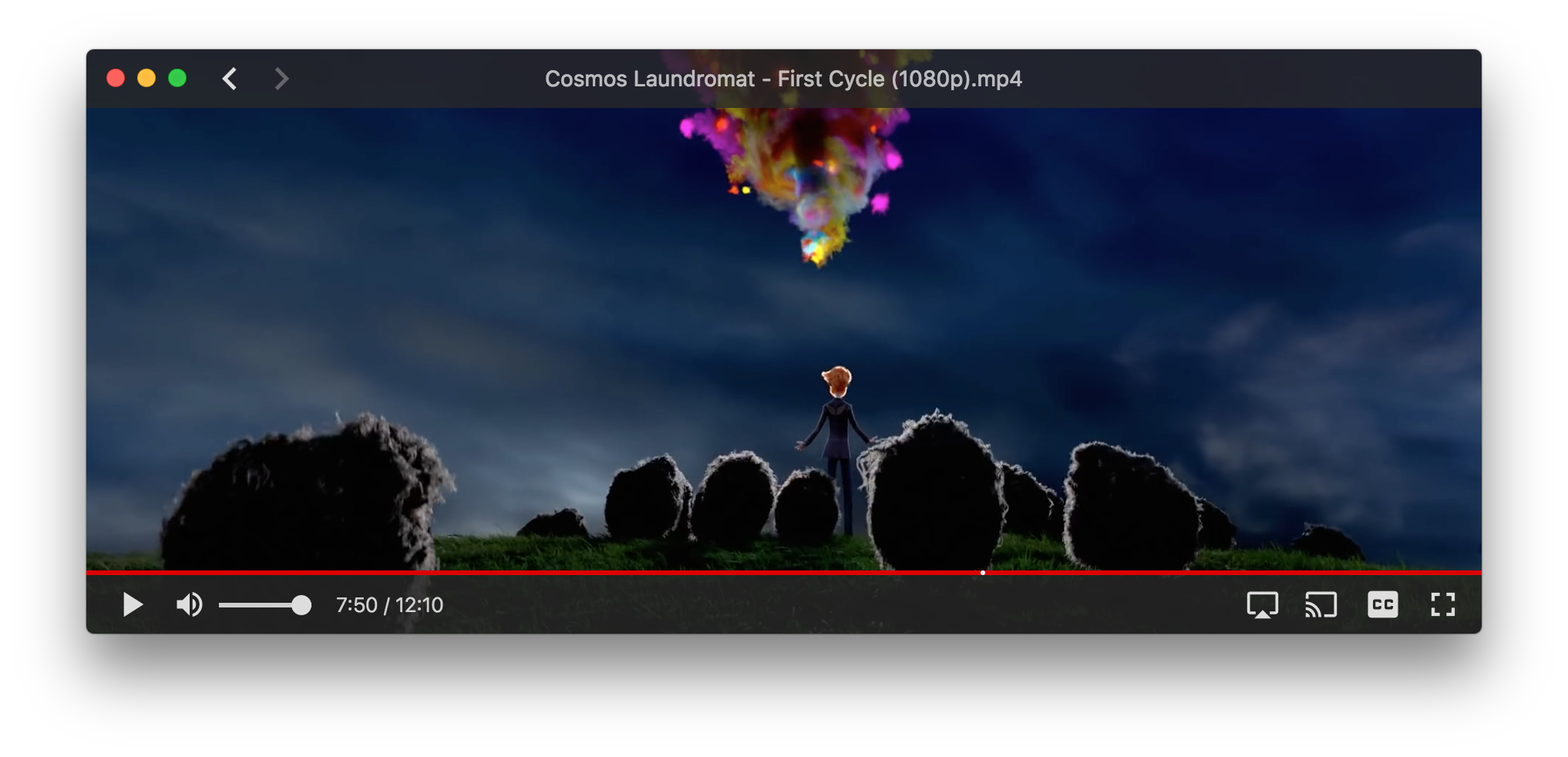
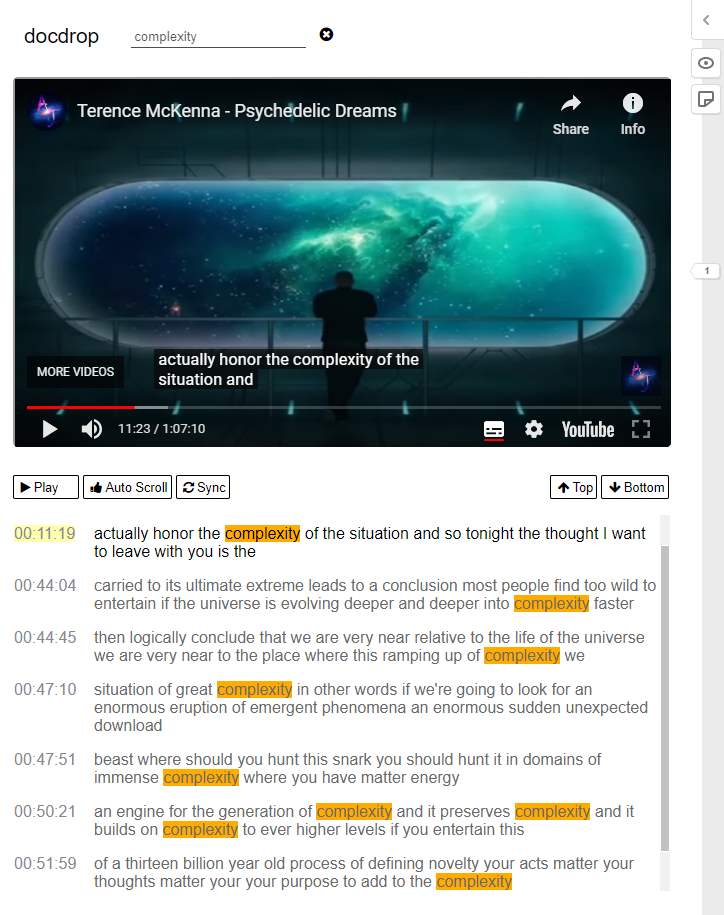
we begin to 00:11:19 actually honor the complexity of the situation
honour complexity situation
-
this awakening must not be disempowering
this awakening must not be disempowering and
the mantle that can be spread over the awakening
to counteract the possibility of disempowerment is this wish to - evoke - realize and - serve the
project of - bringing ever greater amounts of beauty into the world
-
planetary warming complete 00:12:11 collapse of any concern for the destiny of future generations
collapse of any concern for - the destiny of future generations
-
-
fontawesome.com fontawesome.com
-
x
-
More icons like file-pdf…
<svg xmlns="http://www.w3.org/2000/svg" height="16" width="16" viewBox="0 0 512 512"><path d="M64 464l48 0 0 48-48 0c-35.3 0-64-28.7-64-64L0 64C0 28.7 28.7 0 64 0L229.5 0c17 0 33.3 6.7 45.3 18.7l90.5 90.5c12 12 18.7 28.3 18.7 45.3L384 304l-48 0 0-144-80 0c-17.7 0-32-14.3-32-32l0-80L64 48c-8.8 0-16 7.2-16 16l0 384c0 8.8 7.2 16 16 16zM176 352l32 0c30.9 0 56 25.1 56 56s-25.1 56-56 56l-16 0 0 32c0 8.8-7.2 16-16 16s-16-7.2-16-16l0-48 0-80c0-8.8 7.2-16 16-16zm32 80c13.3 0 24-10.7 24-24s-10.7-24-24-24l-16 0 0 48 16 0zm96-80l32 0c26.5 0 48 21.5 48 48l0 64c0 26.5-21.5 48-48 48l-32 0c-8.8 0-16-7.2-16-16l0-128c0-8.8 7.2-16 16-16zm32 128c8.8 0 16-7.2 16-16l0-64c0-8.8-7.2-16-16-16l-16 0 0 96 16 0zm80-112c0-8.8 7.2-16 16-16l48 0c8.8 0 16 7.2 16 16s-7.2 16-16 16l-32 0 0 32 32 0c8.8 0 16 7.2 16 16s-7.2 16-16 16l-32 0 0 48c0 8.8-7.2 16-16 16s-16-7.2-16-16l0-64 0-64z"/></svg>
-
-
www.google.com www.google.com
-
search.google - ethereum name service why
-
What Is Ethereum Name Service? (ENS) - Krakenkraken.com
-
-
www.kraken.com www.kraken.com
-
The Ethereum Name Service (ENS) is a domain name service (DNS) built on the Ethereum blockchain ENS works in a similar way to the Internet's DNS system and helps users to find Ethereum addresses via human-readable names, rather than complex hexadecimal characters
from - search.google - etherium name service why
-
-
github.com github.com
-
Functions for interacting with the Ethereum Name Service
-
Web3.js provider for the HTTP protocol
-
Collection of comprehensive TypeScript libraries for Interaction with the Ethereum JSON RPC API and utility functions. web3js.org/
-
-
docs.web3js.org docs.web3js.org
-
Quickst
web3.js documentation
-
-
web3js.org web3js.org
-
A JavaScript library for building on Ethereumweb3.js is
-
-
sedm.org sedm.org
-
Sovereignty Education and Defense Ministry (SEDM)

-
-
github.com github.com
-
protocol extension api for adding new extension
-
peer discovery via dht, tracker, lsd, and ut_pex
peer discovery
-
Torrent client for node.js & the browser (same npm package!)
-
WebTorrent is a streaming torrent client for node.js and the browser. YEP, THAT'S RIGHT. THE BROWSER. It's written completely in JavaScript – the language of the web – so the same code works in both runtimes.
WebNative
all you need is a browser
-
Streaming torrent client for the web
-
-
github.com github.com
-
Simple, robust, BitTorrent peer wire protocol implementation
BitTorrent protocol
-
Extension for Peers to Send Metadata Files (BEP 9)
-
extension api
protocol extension API
-
-
www.npmjs.com www.npmjs.com
-
BitTorrent Extension for Peers to Send Metadata Files (BEP 9)
peers send metadata files
-
ut_metadata
ut_metadata
-
-
github.com github.com
-
Chitchatter Community Rooms
-
-
github.com github.com
-
Secure peer-to-peer chat that is serverless, decentralized, and ephemeral
-
ecure medium of your choosing (such as Burner Note or Yopass).
-
File transfer functionality is powered by secure-file-transfer.
-
would not be possible without Trystero.
-
The secure networking and streaming magic
would not be possible without Trystero.
File transfer functionality is powered by secure-file-transfer.
-
Chitchatter is a
free ( - as in both - price and - freedom) - communication tool.
Designed to be the
simplest way to - connect with others - privately and
securely,
-
-
-
ou can use the official Chitchatter SDK
learn
-
-
-
chitchatter.im chitchatter.imAbout3
-
Message size is limited to 10,000 characters.
10 k limit
-
User Guide
for - ChitChatter
-
Chat rooms
xxx
-
-
chitchatter.im chitchatter.im
-
read the docs.
-
-
ipfs.indy0.net ipfs.indy0.net
-
meta.do.how -
-
-
www.linkedin.com www.linkedin.com
-
How we can set meaningful learning intentions?
-
-
ipfs.indy0.net ipfs.indy0.net
-
google.search - journal folder structure
google.search - journal folder structure
meta.do.how use trailmarks for link names that make explicit the intent, intended meaning and the subject of the lin
-
-
yopass.se yopass.se
-
No accounts neededSharing should be quick and easy; No additional information except the encrypted secret is stored in the database.
No accounts needed
Sharing should be quick and easy; No additional information except the encrypted secret is stored in the database.
<svg aria-hidden="true" focusable="false" data-prefix="fas" data-icon="user-large-slash" class="svg-inline--fa fa-user-large-slash fa-4x " role="img" xmlns="http://www.w3.org/2000/svg" viewBox="0 0 640 512" color="black"><path fill="currentColor" d="M38.8 5.1C28.4-3.1 13.3-1.2 5.1 9.2S-1.2 34.7 9.2 42.9l592 464c10.4 8.2 25.5 6.3 33.7-4.1s6.3-25.5-4.1-33.7L381.9 274c48.5-23.2 82.1-72.7 82.1-130C464 64.5 399.5 0 320 0C250.4 0 192.4 49.3 178.9 114.9L38.8 5.1zM545.5 512H528L284.3 320h-59C136.2 320 64 392.2 64 481.3c0 17 13.8 30.7 30.7 30.7H545.3l.3 0z"></path></svg>
-
-
burnernote.com burnernote.com
-
On the back end we utilise Laravel's out of the box encryption protocols
-
more useable and technically transparent
= technically transparent
-

-
We "Encrypt-then-MAC"
encrypt-then-MAC
to - crypto.stackexchange.com - encrypt-then-MAC

-
-
crypto.stackexchange.com crypto.stackexchange.com
-

-
Should we MAC-then-encrypt or encrypt-then-MAC?
[from - burnernote.com - Encrypt-then-MAC])(https://hyp.is/TkRxmLMLEe6etTvzQy5TEQ/burnernote.com/about)

-
-
burnernote.com burnernote.com
-
Send secure and encrypted notes that self destruct once they've been read
-
-
github.com github.com
-
A library to encrypt and transfer files P2P in the browser
from - annote
-
, encrypting data prior to sending it
-
-
github.com github.com
-
🤝 Trystero Serverless WebRTC matchmaking for painless P2P: make any site multiplayer in a few lines
-
-
github.com github.com
-
ipfs.indy0.net ipfs.indy0.net
-
ipfs.indy0.net ipfs.indy0.net
-
www.bittorrent.org www.bittorrent.org
-
magnet URI format
URI format
-
In order to support future extensability, an unrecognized message ID MUST be ignored.
extensibility
unrecognized messages ignored
-
only transfers the info-dictionary part of the .torrent file. This part can be validated by the info-hash.
metadata portiion
info plex is not a hash but a human/machine readabl clue structure with info/content hashes
for the plex page
-
the info hash
the info hash
-
support magnet links
magnet links
a link on a web page only containing enough information to join the swarm (the info hash).
the info hash
-
Extension for Peers to Send Metadata Files
-
-
www.npmjs.com www.npmjs.com
-
support magnet links
gloss magnet links = a link on a web page only containing enough information to join the swarm (the info hash).
-
JavaScript implementation of the
-
ut_metadata
-
-
webtorrent.io webtorrent.io
-
-
Running your own private instance of bittorrent-tracker
own bitttorent tracker 
-
if the hash of the file leaks out somehow -- say via a bug in webtorrent #271 -- the file will be worthless.
hash of a file leaking
the base case for ipfs
-
-
Best solution for private torrents? #386
-
-
sariazout.medium.com sariazout.medium.com
-
from - https://hyp.is/yJbgqndsEe6ks4MoZlHwyQ/sariazout.medium.com/
for - Indy Learning Commons

-
-
-
Related searchesYou will see more English now.Open source peer to peer chat voice no server reddit
-
-
www.reddit.com www.reddit.com
-
from - hyp
-
I built a decentralized, serverless, peer-to-peer private chat app
that's - open source, - ephemeral, and - runs entirely in the browser
chitchatter
-
-
ipfs.indy0.net ipfs.indy0.net
-
for - chitchatter - chitchatter.im
-
-
-
google.search - open source peer to peer chat voice no server
for - chitchatter - chitchatter.im - Inter.Personal.Messaging
-
-
www.xml.com www.xml.com
-
A topic map is a computer-readable graph or network of interconnected subjects.
"Eventually everything connects — people, ideas, objects… the quality of the connections is the key to quality per se."
https://hypothes.is/a/zTNK2EMXEe6XQ2__Rk00Fg

-
the name "Topic Maps" is hardly ever mentioned.
yep
-
-
pretextbook.org pretextbook.orgPreTeXt1
-
PreTeXtWrite Once, Read Anywhere
Write Once, Read Anywhere
-
-
www.reddit.com www.reddit.comHey1
-
[META] The future of r/programming

-
-
ipfs.indy0.net ipfs.indy0.net
-
for - chitchatter - chitchatter.im
from - google.search
-
-
ipfs.indy0.net ipfs.indy0.net
-
I built a decentralized, serverless, peer-to-peer private chat ...
-
-
www.google.co.uk www.google.co.uk
-
Related searchesYou will see more English now.Open source peer to peer chat voice no server reddit
reddit
-
I built a decentralized, serverless, peer-to-peer private chat ...
-
P2P Private Chats (No Servers) · Issue #4159 · mumble- ...
-
-
docbook.org docbook.org
-
DocBook.org


-
-
semver.org semver.org
-
Semantic Versioning 2.0.0

-

-
-
emojipedia.org emojipedia.org
-
Yin Yang
☯️
-
-
ipfs.indy0.net ipfs.indy0.net
-
google.search - ipfs desktop share link w3s.link

-
-
ipfs.indy0.net ipfs.indy0.net
-
google.search - ipfs desktop share link w3s.link

-
-
www.svgrepo.com www.svgrepo.com
-
Outline Vectors Free Outline SVG Vectors and Icons. Outline icons and vector packs for Sketch, Figma, websites or apps. Browse 50 vector icons about Outline term.
-
-
Openweb Icons Collection
-
-
ipfs.indy0.net ipfs.indy0.net
-
Need to click on the highlighted item in the outline docs.lansa.com_14_en_lansa015_index.htm
LANSA's RDML (Rapid Development and Maintenance Language) allows you to create a High Level Application Definition or abstraction of your business application. This definition is independent of the operating platform. Defining logic with a 4GL makes your programs independent of the 3GL layer. A 4GL will eventually generate some type of 3GL code which is compiled and executed, but you never need to modify the generated 3GL. In fact, it should not matter which 3GL is used. A High Level Application Definition should allow you to generate or regenerate the same applications in different languages to make your applications portable.
This is why you use a 4GL/RDML:
- High Productivity (Reduce Backlog): A single RDML command can replace hundreds of lines of 3GL code.
- Reduce Maintenance Effort: High level constructs and less code make maintenance much easier.
- Platform Independent Definition: RDML can be generated into multiple languages to support multiple platforms.
- Portable & Durable: RDML is platform independent and can be extended, without impacting development, as 3GL languages improve and change.
- Focus on Business Application Logic: RDML is easy to use so that you can focus on the business logic instead of the programming language.
As your business and technology changes, LANSA's RDML protects your application programming efforts.
-
-
-

-
-
docdrop.org docdrop.orgUntitled1
-
Rapid Development and Maintenance Language)
RDML
-
-
web.archive.org web.archive.org
-
docs.lansa.com docs.lansa.com
-
gotcha online version ca nnot be annotated by hypothesis Neither is the versaion archived with ipfs

-
-
docs.lansa.com docs.lansa.com
-
Technical Reference Guide
https://docs.lansa.com/14/en/lansa015/index.htm#lansa/l4wtgu4a_0005.htm
-
Weblets
stub - Weblets
Weblets are reusable components for common HTML functions and can simply be dragged and dropped into your web pages.

-
-
docs.lansa.com docs.lansa.com
-
docs.lansa.com docs.lansa.com
-

- An Introduction to Developing Web Applications using Visual LANSA
This guide gives you an overview of LANSA's Visual LANSA web architecture and explains the key concepts you will need to get started.
The techniques you use to build web applications are the same as when you're writing a Desktop Rich Client using Visual LANSA Forms and Components.
You now create a Web Page instead of a Form, but on that web page you can drag and drop controls, you can write RDMLX event handlers and incorporate the use of Reusable Parts.
Where a Form compiles into a DLL that's executed within the LANSA runtime, a Web Page compiles into a JavaScript file that's executed within LANSA's JavaScript runtime, as well as a little bit of HTML that defines the starting point of your application.
-
-
docs.lansa.com docs.lansa.com
-
LANSA RDML
x
-
-
ipfs.indy0.net ipfs.indy0.net
-
5 Weblets
Weblets are reusable components for common HTML functions and can simply be dragged and dropped into your web pages. 5.1 Weblet Name · 5.2 Weblet Description.
-
Programming your own Weblet
-
-
ipfs.indy0.net ipfs.indy0.net
-
ipfs.indy0.net ipfs.indy0.net
-
Introduction into the weblets API
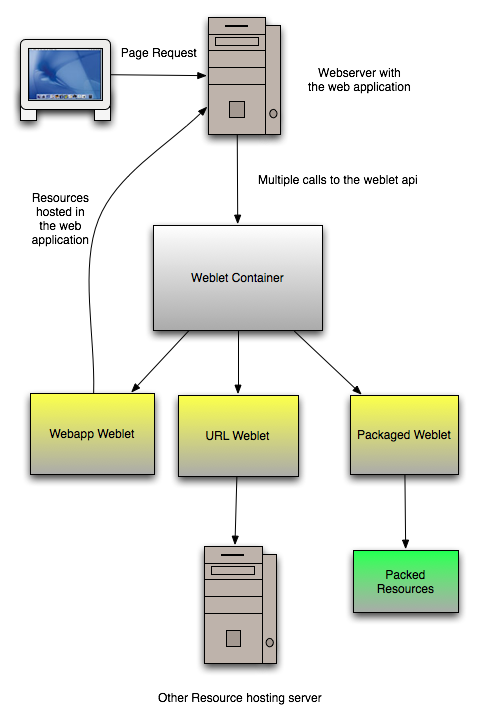
-
-
werpu.github.io werpu.github.io
-
Introduction into the weblets API
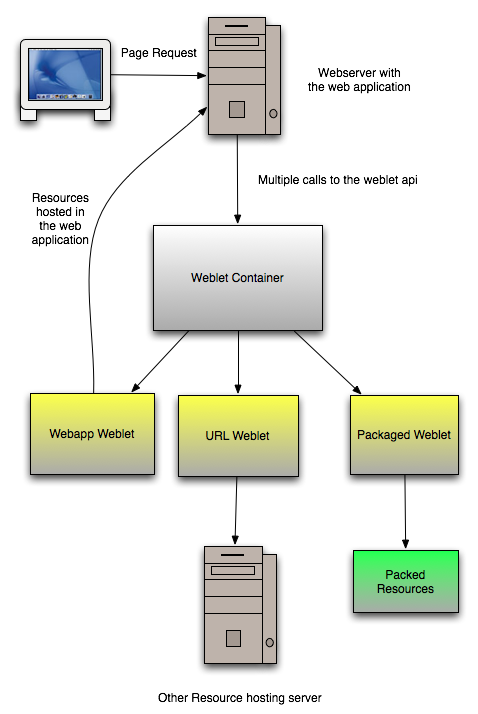
-
-
ipfs.indy0.net ipfs.indy0.net
-
google.search - weblet
-
-
ipfs.indy0.net ipfs.indy0.net
-
google.com.search - weblet
-
-
www.google.com www.google.com
-
google.com.search - weblet
-
-
www.youtube.com www.youtube.com
-
Douglas Lenat: Cyc and the Quest to Solve Common Sense Reasoning in AI | Lex Fridman Podcast #221
Lex Fridman

-
rule macro predicates
which is we'll see this complicated rule and we'll notice that things very much like it syntactically come up again and again and again so we'll create a whole brand new relation or predicate or function that captures that and takes maybe not two arguments takes maybe three four or five arguments and so on and now we have effectively converted some complicated if then rule that might have to have inference done on it into some ground atomic formula which
-
burn into human 00:12:28 long-term memory
you can only burn into human long-term memory a certain number of things per unit time like maybe one every 30 seconds or something and other than that it's just short-term memory and it flows away like water and so on
focal vs subsidiary tacit awareness - mirrors short vs long term memory
-
-
-
-
Download apks from Google Play Store

-
-
-
10 Best Google Play Store Alternatives: Websites And Apps

-
-
forum.cryptpad.org forum.cryptpad.org
-
Export images alongside .md files
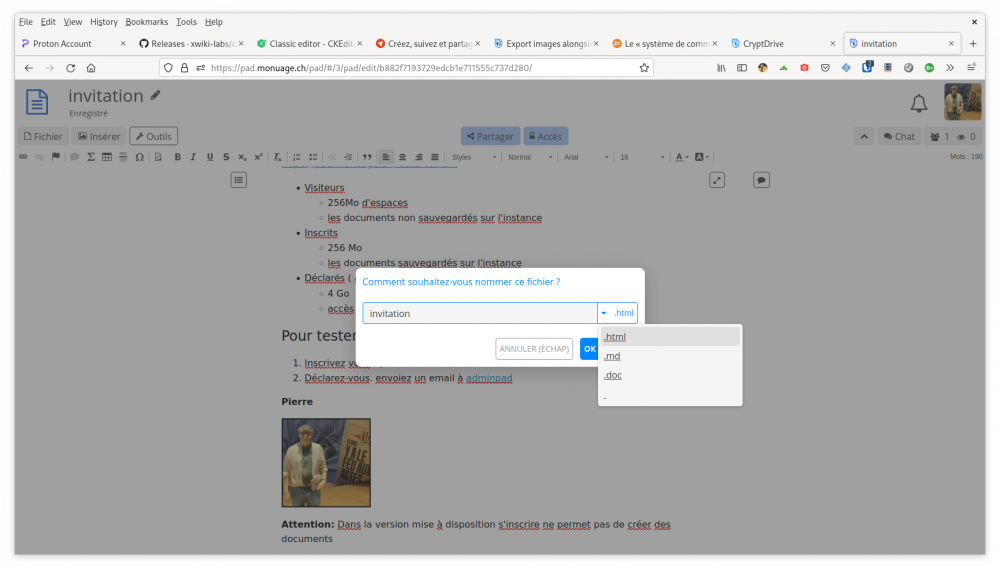
-
-
docdrop.org docdrop.org
-
planetary boundaries
☯️
-
extemporaneous
👌
-
what do we mean by metacrisis,
Question to start
-
-
www.svgrepo.com www.svgrepo.com
-
Table Of Contents Vectors
icon-for : = doc.mark - outline
-
-
www.svgrepo.com www.svgrepo.com
-
500.000+ Open-licensed SVG Vector and IconsSearch, explore and edit the best-fitting free icons or vectors for your projects using a wide variety vector library. Download free SVG vectors and icons for commercial use.
-
-
emojipedia.org emojipedia.org
-
DoveA dove carrying an olive branch, a symbol of peace in Western and Judeo-Christian culture. Depicted as a white bird in full profile facing left, flying as it holds a green sprig in its beak.
🕊️
-
-
emojipedia.org emojipedia.org
-
utf8.icon
for utf8icon search for
-
-
www.npmjs.com www.npmjs.com
-
@orbitdb/core1.0.2 • Public • Published a month ago

-
-
community.brave.com community.brave.com
-
Can’t Connect to “My Node” in brave://ipfs-internals/

-
-
www.trendmicro.com www.trendmicro.com
-
IPFS: A New Data Frontier or a New Cybercriminal Hideout?
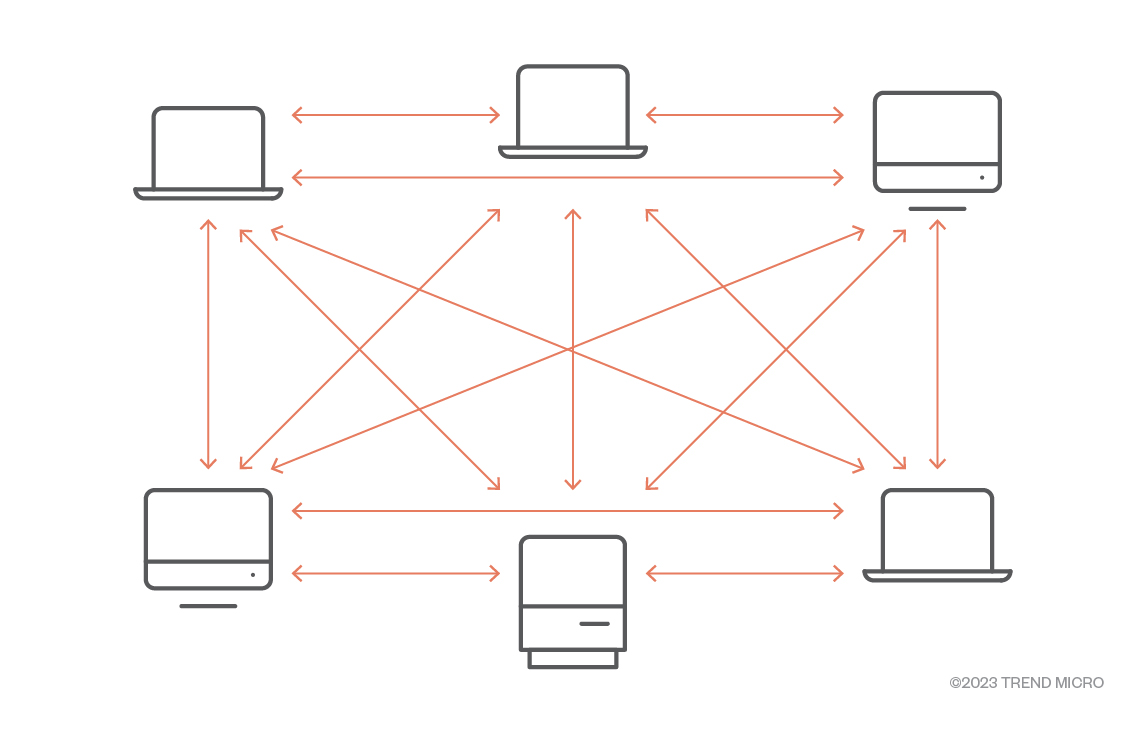
-
-
emojipedia.org emojipedia.org
-
The round, golden-brown pastry of a Chinese mooncake, a traditional delicacy and lunar symbol of the Mid-Autumn Festival. Many platforms feature a design or character imprinted on the crust, and depict a slice cut out to show a brown paste with a duck egg yolk inside. Twitter displays the Chinese character for “fall/autumn” or “harvest” (秋) on t
copy paste 🥮
-
-
emojipedia.org emojipedia.org
-
Bookmark TabsSheets of white, printed paper with variously colored tabs to bookmark important sections or indicate signature lines. Commonly used for content concerning various types of documents and writing.
📑
-
-
github.com github.com
-
Web Gallery of Art

-
PocketBase - A Go based SaaS platform for building web applications htmx - A javascript library for building web applications
interesting
-
-
ipfs.indy0.net ipfs.indy0.net
-
.. Browser Automation: A Deep Dive into the WebDriver BiDi Project and ... What Changes When Sliders Meet HTMX? Exploring New Tech Possibilities!

-
-
ipfs.indy0.net ipfs.indy0.net
-
ipfs.indy0.net ipfs.indy0.net
-
Go vs Python for Browser Automation : r/golang
to - x
-
Which web testing tool should I use?
-
Search only for htmx for "browser automation"
restrict search leave out html
-
-
automationpanda.com automationpanda.com
-
It uses HTMX for handling dynamic interactions without needing any explicit JavaScript.
use - HTMX - handling dynamic interactions - no JavaScript
from
-
-
www.google.com www.google.com
-
google.search
- "htmx" for "browser automation"

-
-
www.google.com www.google.com
-
google.search - htmx for "browser automation"
-
-
emojipedia.org emojipedia.org
-
ChainsTwo parallel lengths of silver chain. Occasionally used as an icon before a hyperlink or for metaphorical connections or chains, e.g., slang off the chains. Samsung’s design previously featured stylized, white chains in a blue square, as a sign or icon for snow chains for winter driving. Not to be confused with 🔗 Link, 📎 Paperclip, 🖇️ Linked Paperclips, or 🧷 Safety Pin.
⛓️
Goes Great With
🖇️ ⚙️ 🔒 🔓 🔏 🔐 🔑 🔗 🔩 🧷 📎 🤝 🪝 🖤 ⛓️💥
-
-
emojipedia.org emojipedia.org
-
LinkTwo links of a silver chain, positioned at a 45° angle. Used as an icon for a hyperlink on computers and the internet. May also be used for metaphorical connections. Not to be confused with ⛓️Chains, 📎 Paperclip, 🖇️ Linked Paperclips, or 🧷 Safety Pin.
🔗 Goes Great With
🌐 ⚓ ℹ️ 📋 📧 📍 🖇️ ✂️ 🔒 💻 🖨️ 📱 ⛓️ 🔩 ⚙️ 🧷 📎 🤝 📌 ♾️ 🪝
-
-
emojipedia.org emojipedia.org
-
PushpinA thumbtack (drawing pin), as used to pin documents on a bulletin (notice) board. Depicted at a 45° angle with its red, flat head to the upper right.
📌
-
-
emojipedia.org emojipedia.org
-
BullseyeA dart board with dart hitting the center / bullseye region.
🎯
-
-
emojipedia.org emojipedia.org
-
Nazar Amulet
🧿
target goal
-
-
emojipedia.org emojipedia.org
-
Rosette
🏵️
-
-
emojipedia.org emojipedia.org
-
Linked Paperclips
🖇️
-
-
emojipedia.org emojipedia.org
-
Mahjong Red Dragon
🀄
-
-
emojipedia.org emojipedia.org
-
Mirror Ball
🪩
-
-
emojipedia.org emojipedia.org
-
Control Knobs
🔩
-
-
www.unicode.org www.unicode.org
-
listing of characters for testing the display of emoji characters.
〰︎ ‼︎ ⁉︎ *︎⃣ #︎⃣ 〽︎ ©︎ ®︎ ↔︎ ↕︎ ↖︎ ↗︎ ↘︎ ↙︎ ↩︎ ↪︎ ⌨︎ ⏏︎ ⏭︎ ⏮︎ ⏯︎ ⏱︎ ⏲︎ ⏸︎ ⏹︎ ⏺︎ ▪︎ ▫︎ ▶︎ ◀︎ ◻︎ ◼︎ ☀︎ ☁︎ ☂︎ ☃︎ ☄︎ ☎︎ ☑︎ ☘︎ ☝︎ ☠︎ ☢︎ ☣︎ ☦︎ ☪︎ ☮︎ ☯︎ ☸︎ ☹︎ ☺︎ ♀︎ ♂︎ ♟︎ ♠︎ ♣︎ ♥︎ ♦︎ ♨︎ ♻︎ ♾︎ ⚒︎ ⚔︎ ⚕︎ ⚖︎ ⚗︎ ⚙︎ ⚛︎ ⚜︎ ⚠︎ ⚧︎ ⚰︎ ⚱︎ ⛈︎ ⛏︎ ⛑︎ ⛓︎ ⛩︎ ⛰︎ ⛱︎ ⛴︎ ⛷︎ ⛸︎ ⛹︎ ✂︎ ✈︎ ✉︎ ✌︎ ✍︎ ✏︎ ✒︎ ✔︎ ✖︎ ✝︎ ✡︎ ✳︎ ✴︎ ❄︎ ❇︎ ❣︎ ❤︎ ➡︎ ⤴︎ ⤵︎ ⬅︎ ⬆︎ ⬇︎ 🌡︎ 🌤︎ 🌥︎ 🌦︎ 🌧︎ 🌨︎ 🌩︎ 🌪︎ 🌫︎ 🌬︎ 🌶︎ 🍽︎ 🎖︎ 🎗︎ 🎙︎ 🎚︎ 🎛︎ 🎞︎ 🎟︎ 🏋︎ 🏌︎ 🏍︎ 🏎︎ 🏔︎ 🏕︎ 🏖︎ 🏗︎ 🏘︎ 🏙︎ 🏚︎ 🏛︎ 🏜︎ 🏝︎ 🏞︎ 🏟︎ 🏳︎ 🏵︎ 🏷︎ 🐿︎ 👁︎ 📽︎ 🕉︎ 🕊︎ 🕯︎ 🕰︎ 🕳︎ 🕴︎ 🕵︎ 🕶︎ 🕷︎ 🕸︎ 🕹︎ 🖇︎ 🖊︎ 🖋︎ 🖌︎ 🖍︎ 🖐︎ 🖥︎ 🖨︎ 🖱︎ 🖲︎ 🖼︎ 🗂︎ 🗃︎ 🗄︎ 🗑︎ 🗒︎ 🗓︎ 🗜︎ 🗝︎ 🗞︎ 🗡︎ 🗣︎ 🗨︎ 🗯︎ 🗳︎ 🗺︎ 🛋︎ 🛍︎ 🛎︎ 🛏︎ 🛠︎ 🛡︎ 🛢︎ 🛣︎ 🛤︎ 🛥︎ 🛩︎ 🛰︎ 🛳︎ 0︎⃣ 1︎⃣ 2︎⃣ 3︎⃣ 4︎⃣ 5︎⃣ 6︎⃣ 7︎⃣ 8︎⃣ 9︎⃣ 🅰︎ 🅱︎ ℹ︎ Ⓜ︎ 🅾︎ 🅿︎ ™︎ 🈂︎ 🈷︎ ㊗︎ ㊙︎
-
-
apps.timwhitlock.info apps.timwhitlock.info
-
INBOX TRAY
📥
-
OUTBOX TRAY
📤
-
-
www.compart.com www.compart.com
-
Circled Division Sign[1]
⨸
utf8.icon-for - holon
-
-
ipfs.indy0.net ipfs.indy0.net
-
The Intertwingularity is near: When humans transcend print ...O'Reilly
-
-
ipfs.indy0.net ipfs.indy0.net
-
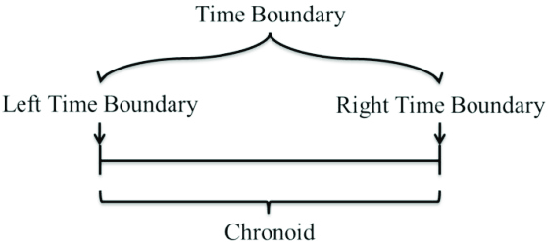
A Chronoid time interval and its boundaries along the time ...ResearchGate

-
-
ipfs.indy0.net ipfs.indy0.net
-
google.search - cronoid
-
-
www.google.com www.google.com
-
google.search - nexialist ted nelson
-
-
kangarookoncepts.tripod.com kangarookoncepts.tripod.com
-
for - nexialist
-
-
kangarookoncepts.tripod.com kangarookoncepts.tripod.com
-
for nexialist
-
-
anselmog.medium.com anselmog.medium.com
-
the word Poetry is derived from the Greek term poiesis, which means “creating”
greek term poiesis creating
understand - why I wanted to combine study of literature (poetry) and mathematics understood as 'that can be learned' - why attracted to learn the ways of creating software
-
Poiesis and the Origin of PoetryHow Poetry became what it is
-
-
www.google.com www.google.com
-
Poiesis and the Origin of Poetry - Anselmo Guarneros - MediumMedium · Anselmo Guarneros160+ likes · 2 years agoMedium · Anselmo Guarneros160+ likes · 2 years agoPoetry derives from the word poiesis, which means creation. Poiesis is understood to be any creative process. It is a form of knowledge and also ...
-
google.search - poesis poetry
-
- Dec 2023
-
docdrop.org docdrop.org
-
must be formed fields that contain these things
Former fields?
-
a field of potential which can change 00:44:41 and collapse in certain circumstances and can move and communicate and so on
Matter as a .
-
no limit to what it is capable of of 00:35:25 embracing and overturning
?
-
whiteheads God um bringing the cosmos into being and in that process there is a reciprocation between God and His creation
whitehead
reciprocation
-
.png)