makes sure that both nodes sendtheir respective SYN packets at the same time.
SYN packet sent at the same time
makes sure that both nodes sendtheir respective SYN packets at the same time.
SYN packet sent at the same time
Hole punching succeeded for 86% of the attempts on TCP
hole punching success rate 86% for TCP
the relay serveris used to coordinate a hole punch through these two NATs.
= relays server - coordinates : a hole punch
Figure 3
.png)
Figure 2: Connection Reversal (after [ 6]): Node 𝑌 connects to therelay server (1.) and asks it to relay a connection to node 𝑋 (2.). Afterexchanging their respective addresses in the CONNECT messageof the DCUtR protocol, 𝑋 first dials 𝑌 directly (3.). This connectionattempt only succeeds if 𝑌 is a public node
= Connection Reversal connection attempt requires public node
.png)
Decentralized Hole Punching
=

at least a small fraction of nodes isnot located behind a firewall or a NAT.
nodes not behind firewall or a NAT
address discoveryand relaying protocols
=
at least one (anyarbitrary) node to bootstrap peer discovery. The key insight is thatthe protocols used for hole punching, namely address discoveryand relaying protocols, can be built such that their resource require-ments are negligible. This makes it feasible for any participant inthe network to run these, thereby enabling the coordination of holepunch attempts, assuming that at least a small fraction of nodes isnot located behind a firewall or a NAT.
ceenabled by default on IPFS nodes behind NATs and/or firewalls,we plan to conduct comprehensive measurements, evaluating holepunching success across the entire heterogeneous IPFS network
hole punching for IPFS nodes behind NATS and firewalls
Direct Connection Upgrade through Relay
https://hypothes.is/a/HR6TCnlQEe2Ll2dtpdwBsg
NAT hole-punching solutio
= in development https://hypothes.is/a/HR6TCnlQEe2Ll2dtpdwBsg
entirely decentralized content-addressable media objectstorage and retrieval platform.
storing andserving media objects at scale
storing and serving = media objects - at scale
provide greater control forusers
Give greater control for People, Players not users (of centralized services
PeerTube
= - video sharing
Mastodon
= - micro blogging
“Decentralized Web”.
growing movement = - colloquially referred to as =
The monetary costs incurred during outages
monetary cost - of = outages
question ?
whose losses Amazon's or all the affected eCommerce players?
widespread chaos during outages
= chaos - during = outages
single points of organizational failure
= services - represent = single points of organizatioinal failure
growing centralization of web systems
=
consolidation of ownership andoperation
=
CCS CONCEPTS
= CCS Concepts
https://hypothes.is/a/lvsxJHkoEe2i3F-7maxAKg

We further evaluate IPFS performance
performance = IPFS
acceptable : publication & retrieval delays - for a wide range of use cases
IPFS)— an open-source, content-addressable peer-to-peer network
= IPFS - open source - content-addressable - peer-to-peer network
provides - distributed data storage & delivery
IPFS has millionsof daily content retrievals
has = IPFS - millions of daily contentretrievals & - underpins dozens of third-party applications
This paper describes
describe : IPFS - design - implementation - = Decentralized Web Platform - largest & most widely used
“Decentralized Web” attempts to distribute ownershi
distribute = Decentralized Web - ownership & - operation of web services - more evenly
B. Y. Zhao et al. “Tapestry: A resilient global-scale overlayfor service deployment”
= Tapestry - resilient - global scale overlay - for = service deployment
Named Data Networking (NDN)
= Named Data Networking
Design and Evaluation of IPFS:A Storage Layer for the Decentralized Web
Design and Evaluation of IPFS:A Storage Layer for the Decentralized Web

One of the most important features of Plex is the ability to let you access your content whenever you want from wherever you are. That means not only at home, but also at work, at a friend’s house, on vacation, etc. To do that, you need to be able to access your Plex Media Server when away from your local network.
= Plex Media Server
= Plex TV
Plex, Inc. Stream without the struggle. Enjoy ALL your entertainment—plus 50,000+ free titles from us—with Plex. Entertainment Providers Los Angeles, California 9,894 followers
Amazon.com Goes Down, Loses $66,240 Per Minute
Obviously they talk about losses for Amazon
not consequential losses

"An efficient method for checking object-orienteddatabase schema correctness,"
comment - the example given shows that the most important concept in the title - cannot be reflected in the classification scheme - considering the centrality of the concepts of schema scheme to the entire field it is not in the sclassification scheme as such
he more specific the concept thebetter.
the more specific the better
tension : - the more specific a term is the more likely to be relevant in many contexts
Identify the lowest branches ofthe tree that seem to apply to your particular paper.
identify lowest branches
HOW TO CLASSIFY WORKS USING ACM’S COMPUTING CLASSIFICATION SYSTEM
title :
Beware of a common pitfall
= pitfalls
The question to ask is, "Would someone look forthis key word or phrase in an index?"
comment
looking for a key word without indicating intent and context is not enough
For a PDF version
Naming and addressing
question - Why only in - Network Architectures & - Network Services
comment - naming is at the heart of computing everywhere
ACM Computing Classification System
from : IPFS DWeb Storage Layer

Networks
networks
It relies on a semantic vocabulary
relies on = Semantic Vocabulary - single source of categories & concepts
reflect the : state of the art of the computing discipline a
receptive to : structural change - as it evolves in the future.
The 2012 ACM Computing Classification System
= - a poly-hierarchical ontology - in semantic web applications
ranging from the learning
ranging from - learning of publicly available knowledge - by an individual knower - -to the = evolution of scientific knowledge
comments - what's missing is mutual learning through social interaction collaboration in a way that itself is stuigmergic, make the learning ltrails themselves permanent. re-callable, re-exeminable, extensible, re0mixable, re-usable and re-discover able, efforts are readily re-sumable as attention turns to them
paving the way to the accelerated growth of knowledge in trust networks for trust where the context of discovery and the justification is not separated but grow together
Dynamical-, Embodied-, Extended-, Distributed-, and Situ-ated- approaches
= DEED
no reference to : Michael Polanyi although uses the words : - knower & - dynamic tacit dimension
no reference to : - articulation
one use of the word : articulate
xref : DEEDS
termed the DEEDS
acronym = DEEDS
a loose and internally fluid - philosophical & - empirical coalition comprising
the
approaches to knowledge and cognition.
reject the cognitivist view of mind and itsemphasis on symbolic representatio
reject = cognitivist view of mind - emphasis on symbolic representation
from : https://sci-hub.se/10.1016/j.cogsys.2007.06.009
https://indyhub.files.fission.name/p/pdf/?Stigmergic%20Epistemology
articulate a stigmergic conception of socialcognitio
use word : articulate
exhibiting a bias towards - = knowledge without the knowing subject - = Artificial Cognition (AC) - instead of = Augmented Cognition - = Artificial Intelligence - vs - Augmented Intellect - = Knowledge acquisition & normative recapitulation - not aiming to make it contiguous with the procress of discovery
discovery
mention = discovery
equat-ing the relevant knowledge with its social dimension.
equating : relevance - with : its social dimension
outline ofan approach
= - will be implemented in further work
processesof social cognition
= processes of social cognition - ranging from - the learning of publicly available knowledge by an individual knower, - to = the evolu- tion of scientific knowledge.
PSO
gloss = PSO - algorithm for the optimization of a function - understood - as a useful tool for different processes of social cognition
the ‘‘particle’’ component in PSO
= denotes : - an individual & - the = ‘‘swarm’’ - in PSO denotes - a process or - grouping.
Particle Swarm Optimization (PSO)
= PSO
Particle Swarm Optimization
human intelligence resultsfrom social interaction
=
are inseparable manifestations of = human socialisty
communities of knowers
social epistemology = communities of knowers
If social epistemology - has the - formation, - acquisition, - mediation, - transmission & - dissemination of knowledge
in complex = communities of knowers - as its subject matter,
then its third party character - is essentially = stigmergic.
What’s in a Pod?A Knowledge Graph Interpretation For The Solid Ecosystem
propose a reconciliatory graph-centric inter ‐pretation wherein a pod is a hybrid, contextualized knowledge graph.
= graph centric interpretation of a = pod - = pod - is a = hybrid contextualized knowledge graph
The current document-centric interpretation
= document-centric interpretation - never been the right thing
The suggested broader interpretation
= - guide Solid through its evolution into a - heterogeneous yet - interoperable ecosystem - support - read/write access patterns - different use cases
server-to-server interactions where there isn’t really the distinction between who is the client and who is the server
server to server
no client
APIs are like waiters - part deux
fully-discoverable APIs that enable autonomous interoperability between machines.
= fully-discoverable APIs - - for = autonomous interoperability between machines
comment : - on closer inspection the model here is - conversational exchange - much like we do it for people as autonomous actors in their own(ed) networks
Introducing CoCo. Co-create, Code, Collaborate, Learn, Play—WITH PEERS IN REAL-TIME Watch video. Join the invite list: https://coco.build Builds on the hugely expressive @scratch @p5xjs environments. Being made with love by a tiny #PhD team @MIT @medialab @LLKgroup

Design and Evaluation of IPFS: A Storage Layer for the Decentralized Web
IPFS - Content Addressed, Versioned, P2P File System
Novum Organum

The inventoried self? Flippant backronyms?Join our Discord
The inventoried Self
Ability to connect directly with the Others?
Learn how hashgraph and Hedera network services work together for you to create an entirely new class of applications.
=
Hedera is designed for fast, fair, and secure applications to take advantage of the efficiency of hashgraph on a decentralized, public network you can trust
=
Immutable events Provide proof
= Manage and verify information with immutable, decentralized trust. Hedera Consensus Service offers flexibility to decentralize any application or bring public trust to permissioned blockchains.
Having googled this a ton, I’ve determined that it is not presently possible to sync localStorage between the multiple instances of Safari or Chrome that a user is logged into.
Several, Web3Storage, Fission, Fission, Peergos and even and of course the IndyWeb/Net/Lab that can even use Perkeep that is built with these, and designed to make that storage layer interchangeable to any other Web 3 storage layers. I have a fully operational end to end validated prototype that is capable to integrate with any Networked Thinking Tool with small adapters needed standardised on MarkDown as a possible exchange format. It is a full realization of Matt Saiia's Dream Space. It is a minimal workable prototype. Preparing to launch on Open Collective under Open Learning Commons. Looking for sponsors and collaborators. Everything in this space is intend to be Open Capability easy to emulate compelling to do. Looking for a grant or crowed funding. It is just what Collective Sense Commons, OGM and dozens others like Kernel is after
represent a sufficiently interesting experiment, because it accepts too much as settled
Mastodon accepts too much settled.
Yes it is not a compromise it is a bloody surrender
account
The problem is with the idea of creating accounts
When you tell me about Twitter vs. Mastodon, I hear that you got rid of the flesh-eating piranhas and replaced them with federated flesh-eating piranhas. No thanks, I’m still not swimming in that pool!
= federated flesh eating piranas
Don't settle for Mastodon
=
Let 2023 be a year of experimentation and invention!
started the experimentation 5 years ago re-imagining the Web based on
the Permanent Hypermedia Protocol for the Web IPFs
from a Named Data Network to Named Everything Networ connectiong people ideas and machine capabilities
what won't work would be a total disaster is 00:15:24 I'm gonna make up a term here API
API on the Web won't ever work

Need a new conceptualization of how the web works
It is possible to devise a Named Intent Layer over the HyperMedia Protocol for the Pernanent Web IPFs
Where Does Growth Come From? | Clayton Christensen | Talks at Google
It is revolutionizing human to human communication in group work we call it inter personal computing.

Gilder is outraged by Google’s lack of attention to security, in multiple senses of the word — customer security, software security, military security. Blockchain will fix all of this — somehow. It just does, okay?
Yes it does
creativity cannot result without human consciousness
Yes, and consciousness is more than electric signals in brain matter
“The new era will move beyond Markov chains of disconnected probabilistic states to blockchain hashes of history and futurity, trust and truth,” apparently.
APIs are like waiters - or are they?
Metaphors We Live By: George Lakoff and Mark Johnson
An example of a holonomic constraint can be seen in a mathematical pendulum.
pendulum degree 1
We cannot rewrite this to an equality, so this is a non-holonomic, scleronomous constraint.

estrictedmathematics to the study of concrete operations on finite or potentially (butnot actually) infinite structures
potentially but not actually infinite
The term is employed here to encompass a wide spectrum of views, including strict finitism,intuitionism, and predicativism. Poincaré adhered to the latter standpoint, while Weyl began as apredicativist but later embraced a form of intuitionism
nuPRL John Derric 1990? Leeds University John V. Tucker
And fi-nally constructivists,5 including Hermann Weyl and Henri Poincaré, restrictedmathematics to the study of concrete operations on finite or potentially (butnot actually) infinite structures; completed infinite totalities, together with im-predicative definitions that made implicit reference to such, were rejected, aswere indirect proofs based on the Law of Excluded Middle
constructivist
= strict finitism
for mathematical truth – and indeed for the very existence of mathematicalentities – was that of the consistency of the underlying systems, since theypresumed that any consistent, complete theory would be categorical, that is,would (up to isomorphism) characterize a unique domain of objects.
categorical unique objects
Strict Finitism and the Logic of Mathematical Applications
Strict Finitism and the Logic of Mathematical Applications [electronic resource] / by Feng Ye. By: Ye, Feng.
EP 48 – INTERVIEW – BORIS MANN – CO-FOUNDER AND CEO – FISSION
individualist nature of intelligence
=
do collective action and decision making at scale 00:35:54 um and could that you know is that an intentional super could it does an intentional super organism is it possible well i think that
Collective action at scale
Super organism
if you can execute a task that is intelligence
I thought it was maximizing future choices
collectivism for the 00:30:04 decentralized web
=
collective navigation of large amounts 00:29:39 of data in ways that are curated but credibly neutral
Curated but credibly neutral
how do we make a like button for the internet
= like button for the internet
Ambient conversations
persuasive is the notion of indirect 00:28:19 coordination so because we all happen to be interested in the same topic and to be working on it along different dimensions doesn't mean that we have to agree on anything or collapse our projects into one or impose one upon the
indirect coordination
enhancing wisdom in web 3 organizations
Wisdom in web 3 organisations
kind of visionary guy but the truth is that i'm more an actionary
Actionary
participatory generative action research where we explore 00:26:21 through inquiry and action what are the qualities that we need to develop for collective wisdom
Action research
Develop wisdom
i'm a refugee from the collective intelligence camp where i spent 40 years studying sometimes contributing to the to the field
refugee from the collective intelligence camp
environmental modifications indirect coordination and trust networks
-
links between them as synapses then then that's to me what's interesting trust networks come out of that delegation collective decision making etc so that's that's something 00:20:02 i'm really interested in exploring thank you so much so that th
People as synapses
actually marking other people
=
stigmargic markers uh are sort of traces of human attention like they're not the full human attention but there's some trace some like part of human attention that we can sort of capture in 00:09:09 a digital environment
stigmargic markers
tracers of human attention
talk about the open source attention there's this idea you know people will 00:08:46 talk about like we need to free our attention online we need like autonomy or freedom uh of attention but then trying to operationalize that like what is attention
open source attention
how to operationalize it
we have no control over that so the ground is sort of yeah 00:08:21 it's we don't own it and we don't really understand it so these platforms are providing this kind of ground that is not conducive necessarily just to sense making um and that is part of the reason like why 00:08:33 why they're yeah what brad was saying like why why there's issues with these platforms
don't own it
problems with platforms
why am i not seeing other people's attention like people that are sort of relevant why am i not seeing like where have they been once they were on this webpage like the trails that they left
trails they left on this page
= TrailMarks & Web Annotation
shared attention is this kind of prerequisite for any kind of effective learning between a teacher and students you have shared attention where you're following the teacher's gaze or you're following their hand 00:05:59 pointing or you're just following what they're looking at or what they're interested in so different levels of like uh following someone's attention
shared following atteention
Ronen Tamari
describing collective behavior as well as long-term threads in 00:01:05 developing [Music] wise groups and how that all comes together in kernel
how we then have a onus to like curate and allocate our attentions 00:02:10 and how we integrate different asynchronous all of these different kinds of question
onus to curate different asynchronous
Kernel Building Kernel - 11/4/22
Kernel Building Kernel - 11/18/2022
=
https://indylab-2022.fission.app/hyp?slayers&user=gyuri
The Art of Hosting Good Conversations Online By Howard Rheingold
from : https://social.coop/@hrheingold@mastodon.social/109453273022629642
In conceptualization context is king.
=
permannotation contrast : if content is King then context is Queen
history : https://docs.google.com/document/d/19pghcYh2KOuAX2_u8ojnLxfmo6BMmUTTsgybCl6W3us/edit
last edited : February 23, 2014, 2:36 PM
content is king, context is queen
if : content is king, context is king
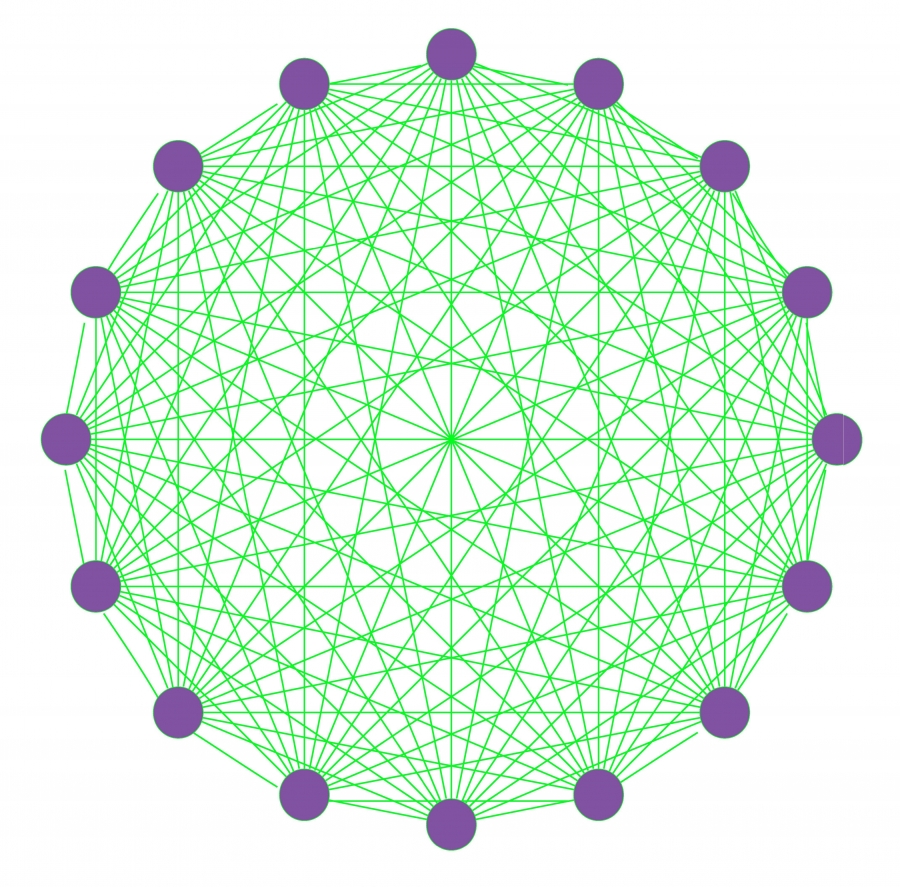
Complete Graph
gloss = Complete Graph
Adjacency Matrix
= Adjecency matrix - for = complete graph
complete graph
=
network is a complete graph and all nodes belong to a single component
gloss = complete graph - all nodes belong to a single component
All you need is links
The path of evolution is always through the adjacent possible

Coevolution creates living complexity
coevolution living complexity
Enter StigFlow; think of automation tools like Zapier, but for collective sensemaking.
zapier for collective sense making
Let the stigmergy flow

Meaningful Nouns
= what's in a name
Meaning-First semantic data models the subject-predicate-object construct is called a triple, the foundational structure upon which semantic technology is built.
meaning first data models
exhortation = design for simplicity and interoperability
Tyler Angert @tylerangertim losing my fucking mind let's redesign git step by step:
Life will knock us down, but we can choose, whether or not, to get back up.

We’ve just completed a $25M Series A led by Polychain and key backers in the decentralized storage ecosystem. We’re announcing Fleek Network to patch a missing piece of the web3 infra stack - content delivery. We’re announcing a brand new Fleek platform to be THE development platform for web3 - protocol agnostic, non-custodial, and open-source.
unlike the previous session I don't have any prizes to give out I'm just going to tell you how to live your 00:00:12 life
no prizes
just going to tell you how to live your life

articulate a stigmergic conception of socialcognitio
use word : articulate
articulate a stigmergic conception of social cognition comment :
but leaving out of scope the role of individual articulation the growth of individual knowing through mutual learning symmathesy exhibiting : bias towards cognition/knowledge without the knowing subject#use word : articulate
comment : - but leaving out of scope the role of individual articulation - the growth of individual knowing - through mutual learning symmathesy - exhibiting : bias towards cognition/knowledge without the knowing subject
Fundamentals of computational swarm intelli-gence
= computational swarm intelligence
comment = bias towards knowledge without the knowing subject
located agent
comment :
“The Russians have been pounding away at Bakhmut for about four weeks and they’re trying to attack it from the east, the north and it looks as though they’ve made some progress from the south of Bakhmut,” Michael Clarke, professor and former director-general of RUSI, told Sky late Tuesday.He described the fighting in the area as “very ferocious.”
RUSI
that is why i wrote this (and apparently need to refresh it): https://datatracker.ietf.org/doc/html/draft-taylor-uuid-ncname… everything within the organization gets a uuid; if it's a fragment, the uuid's representation is converted to that compact form. i have stuff for managing human-friendly overlays as well.
Human Friendly Overlays

end users
reimagining the First Amendment
: essay - series - reimagining = the First Amendment - in the digital age
Protocols, Not Platforms: A Technological Approach to Free SpeechAltering the internet's economic and digital infrastructure to promote free speech
slogan = Protocols, not Platforms
stigmergic cognition
tools
Stigmergic epistemology
=
communities of knowers
= social epistemology = communities of knowers
If social epistemology - has the - formation, - acquisition, - mediation, - transmission & - dissemination of knowledge
in complex = communities of knowers - as its subject matter,
then its third party character - is essentially = stigmergic.
ocated agent
comment : - the use of the term agent is pervasive - prefer the use of the term actor a human - as opposed to a machine agent
accommodate the dynamic tacit dimensionto the acquisition and perpetuation of social knowledge
accommodate - dynamic = tacit dimentions
Knowledge GardenA collection of others' work that has inspired ours
= Stigmergiv Epistemology, Stigmergic Cognition
It’s time to stop behaving like“users.” Instead, let’s become“makers”
= "makers" - not = "users" - take on responsibility
communities of knowers
= communities of knowers
Stigmergic epistemology, stigmergic cognition
= Stigmergic - epistemology - cognition
Accepting our responsibility for how we shape our tools
accepting responsibility - for : how we shape tools
resonate with : - https://hyp.is/7kr0InCCEe2iRx8JRzYefw/bafybeif4oorhvnpwsnjuwoggprdeqcoi4xcbsiptpr75h5b4akzqsri7je.ipfs.w3s.link/Common%20Sense[makers].pdf
Welcome to the Omni Win Project Podcast

provides secure validation while still offering near real-time coordination capabilities at large scales.
= Holochain - provides :
= IndyWeb - contrasted with = HoloChain - operates at ***human scales - high dunbar numb participants - within designated time periods: week, months, years - limiting number of concurrent channels to 42! - keep within limits of individual human attention
-- subtitle : - George Gilder sees bitcoin as the next step in currency - comment - until he sat down and had a long conversation with Craig, then it dawned on him that it's not that good

Human knowledge provides a formal understand-ing of the world.
Human Knowledge provides a formal understanding = of the world =
Relation Path Reasoning:
=
For knowledge acquisition, KGCis reviewed under embedding-based ranking, relationalpath reasoning, logical rule reasoning, and meta relationallearning;
= knowledge acquisition - embedding-based ranking, - relational path reasoning, - logical rule reasoning, and - meta relational learning
path inference
= path inference
A Survey on Knowledge Graphs:Representation, Acquisition and Applications
Teodora Petkova@TheodoraPetkovaA brief history of knowledge bases. In: A survey on knowledge graphs: Representation, acquisition, and applications” Dive in :) https://arxiv.org/pdf/2002.00388.pdf
A Tools for Thought Ecosystem
A Tools for Thought Ecosystem — Open Thoughts
Tool for Thought Ecosystem

= noosphere
= researching = Indy Wiki Threads - indy annotation - permanent : https://bafybeiecy42cfpv464sup5d3eelhvav32y26cp7jgefalmlzc7hfh2nfd4.ipfs.w3s.link/This%20is%20a%20Wiki%20_%20MacRumors%20Forums.pdf
WikiPost History
= WikiPost History

.png)
Testing attachments

Excellent idea! Finally no more hideously long threads from which you have to weed out the details on (I'm looking at you All The Little Things)!
The first post of this thread is a WikiPost and can be edited by anyone with the appropiate permissions. Your edits will be public.
= wiki threads
= WikiPost + associated Thread
A wiki thread is a normal discussion thread where the 1st post is an editable wiki. That means other users can edit the contents of the post. The purpose is to help the management of long running guides or collections of knowledge.
= wiki threads - is a normal discussion thread - where the first post is an editable wiki - other users can edit the contents of the post - purpose : help management of - long running guides - management of knowledge
New Feature: Wiki Threads
Wiki Threads
= Wiki Threads
Wiki Threads - Linking Within A Single Post - Discourse Metahttps://meta.discourse.org › wiki-threads-linking-within...https://meta.discourse.org › wiki-threads-linking-within...Wiki Threads - Linking Within A Single Post · support · Mulsiphix October 1, 2019, 10:05am #1. I have some very long posts that are in Wiki format.1 answer · Top answer: Yup: [image] Deep Linking to Headings (Anchors) faq (as of 29 May 20
= Wiki Threads
Wiki Threads - Linking Within A Single Post
= Wiki Threads
- linking within a single post
- why not everywhere
= Indy Wiki Threads
(as of 29 May 2020) Unfortunately there is currently no standard markdown way of creating a heading with an anchor, so if you wish to link directly to an anchor in a post, you have to use regular HTML. Simply create a heading with an id that begins with heading-- like so: <h3 id='heading--link-to-me'>Link to me</h3> And then any time you link to the post, you can add #heading--link-to-me in the URL and it’ll jump directly to that spot once it loads. (To prevent abuse of styling on the site, y…
= Wiki threads - documented example of a need - kludgy solution - for the lack of standard markdown way of creating a heading with an anchor
also add that you're making a wiki so you have to make the threads to then put them on the wiki
![]()
There are three main objects in LiquidThreads. They are, in descending order of size, Channels, Topics and Posts

Standard "talk" pages are an extremely high barrier-to-entry for new users
talk pages high barrier of entry
LiquidThreads is a threaded-model discussion system intended as an alternative to standard MediaWiki talk pages. LiquidThreads is designed to be familiar and easy to use to most internet users and to provide a smooth on-ramp for participation and collaboration.

= WikiThreads, Wiki Threads

Monero Means Money Private, decentralized cryptocurrency that keeps your finances confidential and secure.
