As users begin migrating to the noncommercial fediverse, they need to reconsider their expectations for social media — and bring them in line with what we expect from other arenas of social life. We need to learn how to become more like engaged democratic citizens in the life of our networks.
- Nov 2022
-
www.noemamag.com www.noemamag.com
-
-
Because Mastodon is designed more for chatter than governance, we use a separate platform, Loomio, for our deliberation and decision-making.
social.coop uses Loomio for governance
-
We believe that it is time to embrace the old idea of subsidiarity, which dates back to early Calvinist theology and Catholic social teaching. The European Union’s founding documents use the term, too. It means that in a large and interconnected system, people in a local community should have the power to address their own problems. Some decisions are made at higher levels, but only when necessary. Subsidiarity is about achieving the right balance between local units and the larger systems.
Defining "subsidiarity"
The FOLIO community operates like this..the Special Interest Groups have the power to decide for their functional area, and topics that cross functional areas are decided between SIGs or are brought to a higher level council.
-
-
www.frontiersin.org www.frontiersin.org
-
Nevertheless, from the standpoint of learning theory, these and other authors have it backward, because a steep learning curve, i.e., a curve with a large positive slope, is associated with a skill that is acquired easily and rapidly (Hopper et al., 2007).
Steep learning curve
I don't think I'll ever hear this phrase the same again. A steep learning curve is a good thing...meaning over time that it was very easy to learn (less time on the x axis).
-
Nevertheless, even ardent proponents of the view that DID is a naturally occurring condition that stems largely from childhood trauma (e.g., Ross, 1994) acknowledge that “multiple personality disorder” is a misnomer (Lilienfeld and Lynn, 2015), because individuals with DID do not genuinely harbor two or more fully developed personalities
Multiple personality disorder
Use dissociative identity disorder since 1994.
-
There is no known “optimal” level of neurotransmitters in the brain, so it is unclear what would constitute an “imbalance.” Nor is there evidence for an optimal ratio among different neurotransmitter levels. Moreover, although serotonin reuptake inhibitors, such as fluoxetine (Prozac) and sertraline (Zoloft), appear to alleviate the symptoms of severe depression, there is evidence that at least one serotonin reuptake enhancer, namely tianepine (Stablon), is also efficacious for depression (Akiki, 2014). The fact that two efficacious classes of medications exert opposing effects on serotonin levels raises questions concerning a simplistic chemical imbalance model.
Chemical imbalance
We don't (yet) know what the proper balance of brain chemistry would be, so saying that mental illness is cause by a chemical imbalance is problematic. There are drugs that effectively treat depression that both decrease and increase serotonin, so because of these opposite effects it is hard to say what the proper amount should be.
-
Furthermore, there are ample reasons to doubt whether “brainwashing” permanently alters beliefs (Melton, 1999). For example, during the Korean War, only a small minority of the 3500 American political prisoners subjected to intense indoctrination techniques by Chinese captors generated false confessions. Moreover, an even smaller number (probably under 1%) displayed any signs of adherence to Communist ideologies following their return to the US, and even these were individuals who returned to Communist subcultures
Brainwashing
The techniques of "brainwashing" aren't that much different form other persuasion methods. This term originated in the Korean war, and subsequent studies suggested that there are no permanent alterations to beliefs.
-
numerous scholars have warned of the jingle and jangle fallacies, the former being the error of referring to different constructs by the same name and the latter the error of referring to the same construct by different names (Kelley, 1927; Block, 1995; Markon, 2009). As an example of the jingle fallacy, many authors use the term “anxiety” to refer interchangeably to trait anxiety and trait fear. Nevertheless, research consistently shows that fear and anxiety are etiologically separable dispositions and that measures of these constructs are only modestly correlated (Sylvers et al., 2011). As an example of the jangle fallacy, dozens of studies in the 1960s focused on the correlates of the ostensibly distinct personality dimension of repression-sensitization (e.g., Byrne, 1964). Nevertheless, research eventually demonstrated that this dimension was essentially identical to trait anxiety (Watson and Clark, 1984). In the field of social psychology, Hagger (2014) similarly referred to the “deja variable” problem, the ahistorical tendency of researchers to concoct new labels for phenomena that have long been described using other terminology (e.g., the use of 15 different terms to describe the false consensus effect; see Miller and Pedersen, 1999).
Jingle and Jangle Fallacies
Jingle: referring to different things by the same word
Jangle: referring to a single thing with different words
-
Lilienfeld, S. O., Sauvigné, K. C., Lynn, S. J., Cautin, R. L., Latzman, R. D., & Waldman, I. D. (2014). Fifty psychological and psychiatric terms to avoid: a list of inaccurate, misleading, misused, ambiguous, and logically confused words and phrases. Frontiers in Psychology. https://doi.org/10.3389/fpsyg.2015.01100
-
-
www.nature.com www.nature.com
-
The Great Depression and its aftermath offered Schmitz and a colleague one such opportunity. Poverty shrinks brains from birth By comparing markers of ageing in around 800 people who were born throughout the 1930s, the team observed that those born in US states hit hardest by the recession — where unemployment and wage reductions were highest — have a pattern of markers that make their cells look older than they should. The impact was diminished in people who were born in states that fared better during the 1930s.The cells could have altered the epigenetic tags during early childhood or later in life. But the results suggest that some sort of biological foundation was laid before birth for children of the Great Depression that affected how they would age, epigenetically, later in life.
Aging markers affected in utero.
Tags
Annotators
URL
-
-
www.canarymedia.com www.canarymedia.com
-
A 2020 study by the European Union found that contrails and other non-CO2 aircraft emissions warm the planet twice as much as the carbon dioxide released by airplanes.
From the intermediate linked blog post:
Using a derivative metric of the Global Warming Potential (100), the GWP, aviation emissions are currently warming the climate at approximately three times the rate of that associated with CO2 emissions alone.
pp. 35-36 of EASA report for European Commission, (2020). Updated analysis of the non-CO2 climate impacts of aviation and potential policy measures pursuant to the EU Emissions Trading System Directive Article 30(4). https://eur-lex.europa.eu/resource.html?uri=cellar:7bc666c9-2d9c-11eb-b27b-01aa75ed71a1.0001.02/DOC_1&format=PDF
-
-
themarkup.org themarkup.org
-
Meta collects so much data even the company itself sometimes may be unaware of where it ends up. Earlier this year Vice reported on a leaked Facebook document written by Facebook privacy engineers who said the company did not “have an adequate level of control and explainability over how our systems use data,” making it difficult to promise it wouldn’t use certain data for certain purposes.
Poor data controls at Facebook
-
Some of the sensitive data collection analyzed by The Markup appears linked to default behaviors of the Meta Pixel, while some appears to arise from customizations made by the tax filing services, someone acting on their behalf, or other software installed on the site. Report Deeply and Fix Things Because it turns out moving fast and breaking things broke some super important things. Give Now For example, Meta Pixel collected health savings account and college expense information from H&R Block’s site because the information appeared in webpage titles and the standard configuration of the Meta Pixel automatically collects the title of a page the user is viewing, along with the web address of the page and other data. It was able to collect income information from Ramsey Solutions because the information appeared in a summary that expanded when clicked. The summary was detected by the pixel as a button, and in its default configuration the pixel collects text from inside a clicked button. The pixels embedded by TaxSlayer and TaxAct used a feature called “automatic advanced matching.” That feature scans forms looking for fields it thinks contain personally identifiable information like a phone number, first name, last name, or email address, then sends detected information to Meta. On TaxSlayer’s site this feature collected phone numbers and the names of filers and their dependents. On TaxAct it collected the names of dependents.
Meta Pixel default behavior is to parse and send sensitive data
Wait, wait, wait... the software has a feature that scans for privately identifiable information and sends that detected info to Meta? And in other cases, the users of the Meta Pixel decided to send private information ot Meta?
-
-
themarkup.org themarkup.org
-
We’re not mandating content warnings. I think I’ve kind of had every single opinion that one can have about this. My first response, which I think is most journalists’ first response, was, “Who are these precious snowflakes?” Then a bunch of people said, “No, that’s not how to think about it; it’s really just the subject line of an email,” and if I had the right to send you an email where you had to see the whole thing, that’d be kind of annoying. But then a lot of people in the BIPOC community said, “The way this is being used on Mastodon is often to shield White people from racism and homophobia and other issues.” And so I’m very sympathetic to that as well. I think the solution Eugen came up with is the right solution: It’s a tool, and you can use it if you want to.
Content Warnings
What Davidson doesn't mention here is a Mastodon feature that I find fascinating. Sure, the person who creates the post can have a content warning, but the viewer also has the ability to set keywords that they want hidden behind a Content Warning (or simply blocked).
-
Everyone who goes through the exercise of “what is journalism?” quickly learns there are no obvious, uncontroversial answers. We had a conversation this morning about somebody who has a blog about beer. We said, well, this person does reporting, they actually interview people, they look at statistics, they’re not just sharing their opinion on beer. And it felt like, yeah, that’s journalism. Now, would we make that decision a month from now? I don’t know. I don’t think it’s appropriate for me to get into specifics, but we’ve had some tricky edge cases. Inherently, it’s tricky.
Distributed verification, or "What is Journalism?"
The admins of the journa.host server are now taking on the verification task. The example Davidson uses is a beer blog; the blog is more than opinion, so for the moment that person is added.
So what is the role of professional organizations and societies to create a fediverse home for recognized members? This doesn't seem sustainable...particularly since people set the dividing lines between their professional and personal interests in different places.
Spit-balling here...this reminds me somewhat of the Open Badges effort of Mozilla and IMS Global. If something like that was built into the Mastodon profile, then there would be transparency with a certifying agency.
-
The Twitter blue check, for all the hate I have given Twitter over the years, is a public good. It is good, in my view, that when you read a news article or view a post, you can know with confidence it’s the journalist at that institution. It doesn’t mean they’re 100 percent right or 100 percent ethical, but it does mean that’s a person who is in some way constrained by journalism ethics.
Twitter Blue Check as a public good
There was some verification process behind the pre-Musk blue check, and that was of benefit to those reading and evaluating the veracity of the information. Later, Davidson points out that "journalism had outsourced that whole process...to whoever happened to work at Twitter."
-
Davidson: I think the interface on Mastodon makes me behave differently. If I have a funny joke or a really powerful statement and I want lots of people to hear it, then Twitter’s way better for that right now. However, if something really provokes a big conversation, it’s actually fairly challenging to keep up with the conversation on Twitter. I find that when something gets hundreds of thousands of replies, it’s functionally impossible to even read all of them, let alone respond to all of them. My Twitter personality, like a lot of people’s, is more shouting. Whereas on Mastodon, it’s actually much harder to go viral. There’s no algorithm promoting tweets. It’s just the people you follow. This is the order in which they come. It’s not really set up for that kind of, “Oh my god, everybody’s talking about this one post.” It is set up to foster conversation. I have something like 150,000 followers on Twitter, and I have something like 2,500 on Mastodon, but I have way more substantive conversations on Mastodon even though it’s a smaller audience. I think there’s both design choices that lead to this and also just the vibe of the place where even pointed disagreements are somehow more thoughtful and more respectful on Mastodon.
Twitter for Shouting; Mastodon for Conversation
Many, many followers on Twitter makes it hard for conversations to happen, as does the algorithm-driven promotion. Fewer followers and anti-viral UX makes for more conversations even if the reach isn't as far.
-
-
www.wnycstudios.org www.wnycstudios.org
-
I just learned this idea of anchor institution at the Association of Rural and Small Libraries Conference. There are institutions that anchor communities. Right. So that the hospital is one. Lots of people work there. Everyone goes there at some point, has a role to play in the community and the library is similar. You'll often get people who will say that the library's are irrelevant, but that just means that they can afford not to use a public service. And I don't know why they are the people we ask to share their expertise on the use of public services. But most of us use the public library. Our kids get their picture books there. We maybe do passport services. Maybe the library has tech training. One of my first jobs at the public library was teaching senior citizens how to do mouse and keyboarding skills. So where else are you going to learn those things? You learn them at the library.
Libraries as anchor institutions
Public libraries, in particular, and the places where anyone in the community can go for services. The mission of the library is to serve the needs of the specific community it is in.
-
BROOKE GLADSTONE It's always framed as parents rights, but according to Summer Lopez, who's the chief program officer of free expression at PEN America, most of these book bans are on books that families and children can elect to read. They're not required to read them. They just exist. EMILY DRABINSKI One of the things I loved about libraries when I first started is that they are non-coercive learning spaces. You don't have to read anything. You can choose from anything on the shelf. And if your kid checks out something you don't want them to read, that's between you and your child and the way that you're parenting. And it just isn't something that the state needs to be involved in.
Libraries as non-coercive learning spaces
Citing parent's rights is a false choice. The parents do have the right to supervise what their children read. But the book is just on the shelf..."they just exist".
-
Well, librarians are professionals. We go through a library master's degree program, and we're trained on the job to make book selections for our communities. We build collections that are responsive to the needs of the people we serve. So right now, I'm talking to you from the Graduate Center in midtown Manhattan. My liaison responsibilities here to the School of Labor and Urban Studies and to our urban education program. I'm not going to choose Gender Queer to purchase for our library, not because I'm a censor, but because that's not a book that we need in our collection right now. But I think you can tell that it's not really about the books if you look to some of the particular cases. So, for example, attacks on the Boundary County Library in Northern Idaho. This was the same set of 300 books that they want banned. The extremist right in that part of the state came after the public library there. That library didn't own any of the books that were on the list.
Librarian training in material selection appropriate for the library's audience
-
BROOKE GLADSTONE In the Tennessee State Assembly last April, Representative Jerry Sexton took on this question. [CLIP] JERRY SEXTON Let's say you take these books out of the library. What are you going to do with them? You can put them on the street, let them on fire. JERRY SEXTON I don't have a clue, but I would burn them.
Tennessee State Representative would burn banned books
It's true: Representative says he would burn books deemed inappropriate by state – Tennessee Lookout
-
-
www.technologyreview.com www.technologyreview.com
-
“In a way, Twitter has become a kind of aggregator of information,” says Eliot Higgins, founder of open-source investigators Bellingcat, who helped bring the perpetrators who downed MH17 to justice. “A lot of this stuff you see from Ukraine, the footage comes from Telegram channels that other people are following, but they're sharing it on Twitter.” Twitter has made it easier to categorize and consume content from almost any niche in the world, tapping into a real-time news feed of relevant information from both massive organizations and small, independent voices. Its absence would be keenly felt.
Twitter's role in aggregating world news (and reactions)
-
For eight years, the US Library of Congress took it upon itself to maintain a public record of all tweets, but it stopped in 2018, instead selecting only a small number of accounts’ posts to capture. “It never, ever worked,” says William Kilbride, executive director of the Digital Preservation Coalition. The data the library was expected to store was too vast, the volume coming out of the firehose too great. “Let me put that in context: it’s the Library of Congress. They had some of the best expertise on this topic. If the Library of Congress can’t do it, that tells you something quite important,” he says.
Library of Congress' role in archiving twitter
-
Part of what makes Twitter’s potential collapse uniquely challenging is that the “digital public square” has been built on the servers of a private company, says O’Connor’s colleague Elise Thomas, senior OSINT analyst with the ISD. It’s a problem we’ll have to deal with many times over the coming decades, she says: “This is perhaps the first really big test of that.”
Public Square content on the servers of a private company
-
-
www.kcur.org www.kcur.org
-
Judith Cremer, the library director, said the book was added to the library after it made the William Allen White Award 2017-2018 Master List for grades 3-5, and has only been checked out four times.Cremer said parents have the option of filtering which books their children check out, and can speak to staff about limiting their children’s access to certain books. She stressed that she and her staff aren’t trying to fight the council and aren’t interested in divisive matters. She’s been at the library for almost 20 years, and just wants to serve the community.“We just are doing what public libraries do,” Cremer said. “We don’t really judge information, we are a reflection of the world and things that are in the world. We have information that has been published and mediated and checked for facts. So it’s a safe place that people can go to get access to that information. It’s not like we are handing out or advocating it in any way. It’s just there.”
Not advocacy...just there
-
St. Marys resident Hannah Stockman, a stay-at-home mom looking after 13 kids, said the move would be devastating for her and others like her.“At this point, it’s the only space left that we have for the public,” Stockman said. “We don’t have any pool or any other amenities through the community center. So people come here for many, many different reasons.”
Library as community space
-
-
morningconsult.com morningconsult.com
-
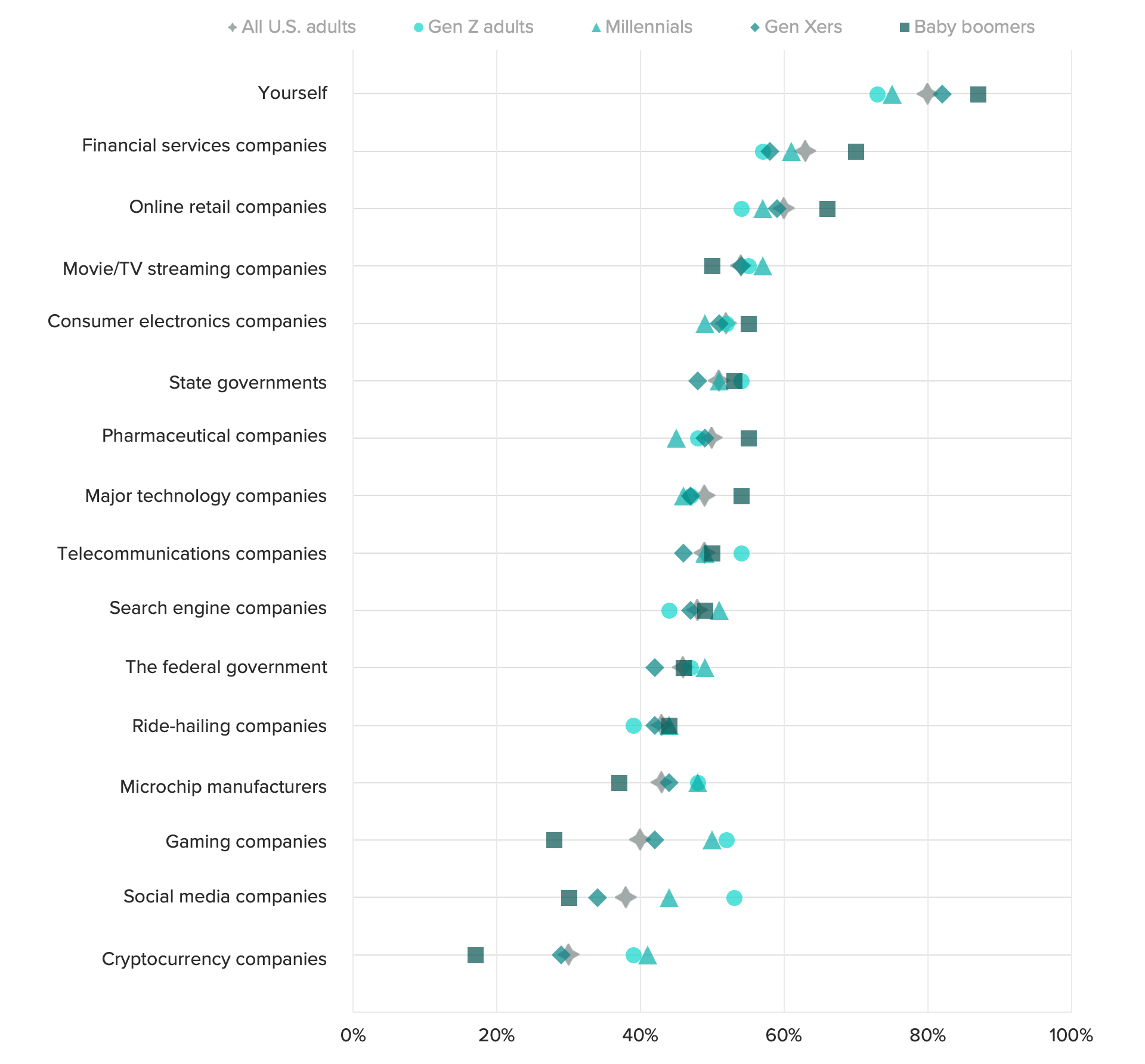
Although complicated, Gen Z’s relationship with data privacy should be a consideration for brands when strategizing their data privacy policies and messaging for the future. Expectations around data privacy are shifting from something that sets companies apart in consumers’ minds to something that people expect the same way one might expect a service or product to work as advertised. For Gen Zers, this takes the form of skepticism that companies will keep their data safe, and their reluctance to give companies credit for getting it right means that good data privacy practices will increasingly be more about maintaining trust than building it.
Gen-Z expectations are complicated
The Gen-Z generation have notably different expectations about data privacy than previous generations. "Libraries" wasn't among the industry that showed up in their survey results. That Gen-Z expects privacy built in makes that factor a less differentiating characteristic as compared to older generations. It might also be harder to get trust back from members of the Gen-Z population if libraries surprise those users with data handling practices that they didn't expect.
-
The notable exception: social media companies. Gen Zers are more likely to trust social media companies to handle their data properly than older consumers, including millennials, are.
Gen-Z is more trusting of data handling by social media companies
For most categories of businesses, Gen Z adults are less likely to trust a business to protect the privacy of their data as compared to other generations. Social media is the one exception.
-
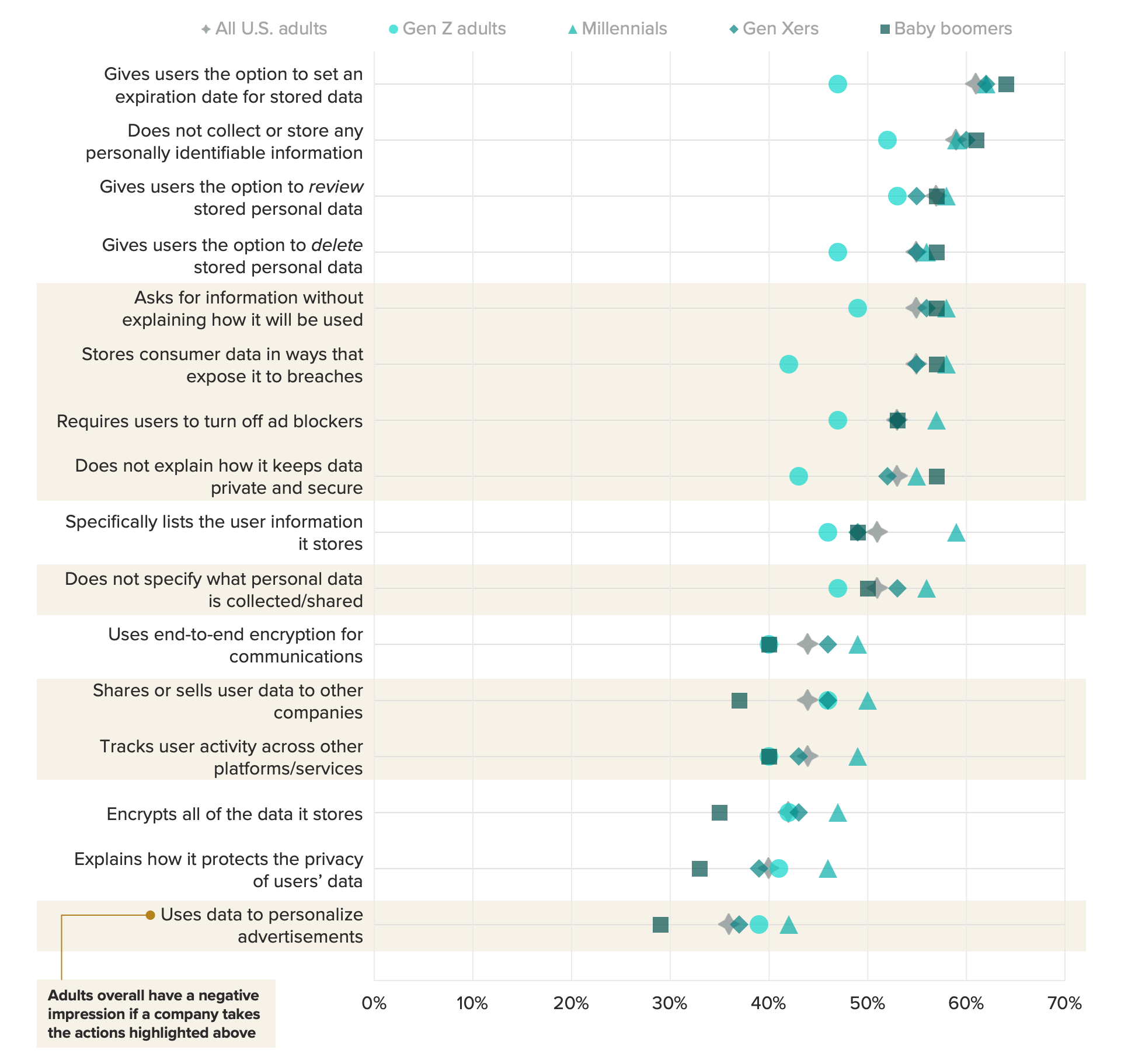
Furthermore, the youngest generation is more jaded than others on this topic, finding it less surprising if a company stores data in a way that exposes it to a breach or asks for information without explaining what it will be used for.
Disconnect between generations on privacy expectations
This chart from the article summarizes the responses of a survey across generations of adults. It shows that Gen-Z adults are less surprised by privacy-enhancing settings, tools, and techniques, and more surprised in situations when their data is used for advertising (as compared to other generations).
-
Gen Z came of age during a major moment in data privacy. The global conversation around the topic shifted following the Facebook/Cambridge Analytica scandal in 2018. The incident altered the public’s view of major technology companies from great innovators and drivers of the economy to entities that need more oversight. Massive regulatory efforts like the General Data Protection Regulation in Europe and the California Consumer Privacy Act have since gone into effect, with more on the way, representing a break in consumers’ trust in tech companies to sufficiently safeguard people’s data.
Gen Z expectations for data privacy are different
They came of age during the Facebook/Cambridge Analytica scandal. [[GDPR]] has been a thing for them and set expectations for how user data is treated (at least in Europe). These become table stakes for Gen Z users...what else is a company doing to differentiate itself.?
-
-
-
-
In other words, the community of early users were super serious about consent. They don’t like their utterances circulating in ways they don’t like. You could say, “well, tough; you’re posting stuff in public, right?” But since this is Mastodon, users have powerful tools for responding to actions they don’t like. If the folks on server A don’t like the behavior of people on server B, they can “defederate” from server B; everyone on server B can no longer see what folks on A are doing, and vice versa. (“Defederating” is another deep part of Mastodon’s design that is, ultimately, powerfully antiviral.)
Defederation to combat breaches of norms
I wonder if this sort of thing would happen if someone created an ActivityPub node that did exhibit some of these viral behaviors. Would that node be shunned by the rest of the fediverse? Will that answer be the same a year from now when the fediverse is more mainstream?
-
Another big, big difference with Mastodon is that it has no algorithmic ranking of posts by popularity, virality, or content. Twitter’s algorithm creates a rich-get-richer effect: Once a tweet goes slightly viral, the algorithm picks up on that, pushes it more prominently into users’ feeds, and bingo: It’s a rogue wave.On Mastodon, in contrast, posts arrive in reverse chronological order. That’s it. If you’re not looking at your feed when a post slides by? You’ll miss it.
No algorithmic ranking on Mastodon
To drive the need to make the site sticky and drive ads, Twitter used its algorithmic ranking to find and amplify viral content.
-
For example, Mastodon has no analogue of Twitter’s “quote-tweet” option. On Mastodon, you can retweet a post (they call it “boosting”). But you can’t append your own comment while boosting. You can’t quote-tweet.Whyever not? Because Mastodon’s original designer (and the community of early users) worried that quote-tweeting on Twitter had too often encouraged a lot of “would you look at this bullshit?” posts. And that early Mastodon community didn’t much like those dynamics.
No Quote-Tweet equivalent on Mastodon
-
As Beschizza said …“I wanted something where people could publish their thoughts without any false game of social manipulation, one-upmanship, and favor-trading.”It was, as I called it, “antiviral design”.
Definition of "antiviral design"
Later, Thompson says: "[Mastodon] was engineered specifically to create _friction — _to slow things down a bit. This is a big part of why it behaves so differently from mainstream social networks."
The intentional design decisions on Mastodon slow user activity.
-
-
storage.courtlistener.com storage.courtlistener.com
-
CASE NO. 2:22-cv-2470 docket #29
UNITED STATES DISTRICT COURT SOUTHERN DISTRICT OF OHIO EASTERN DIVISION
OCLC ONLINE COMPUTER LIBRARY CENTER, INC., PLAINTIFF,
vs.
CLARIVATE, PLC, ET AL., DEFENDANTS.
TRANSCRIPT OF TELEPHONIC STATUS CONFERENCE PROCEEDINGS BEFORE THE HONORABLE JAMES L. GRAHAM FRIDAY, JUNE 24, 2022; 10:00 A.M. COLUMBUS, OHIO
From OCLC Online Computer Library Center, Inc. v. Clarivate, Plc, 2:22-cv-02470, the PACER mirror on CourtListener.com.
-
-
-
By the mid-2010s, Chinese people in big cities had generally switched from using cash to using Alipay and WeChat Pay. By the end of 2021, about 64 percent of Chinese people were using mobile payment systems, according to a report by Daxue Consulting, with Alipay and WeChat Pay handling most payments. For city dwellers, the figure was 80 percent. One reason China’s government is pushing the digital yuan is to try to gain more control of how citizens make payments. For years, big tech companies were able to operate almost like public utilities, creating and effectively regulating large parts of the financial industry.
Already high adoption of commercial digital payment systems
Previously in the hands of companies, the governmental digital cash system could usurp those systems.
-
The central bank is building the infrastructure needed to enable sweeping adoption in years to come, signing up merchants, adapting the banking system, and developing applications such as a way to earmark money for health care or transit, he says. That lays the groundwork for eCNY to be China’s default payment system in 10 to 15 years, and it has been enough to put the project ahead of any other government-backed digital currency.
Infrastructure for controlling spending
Not only is the government putting the raw transaction infrastructure in place, but this sentence makes it sound like they will be able to control how money is spent. Perhaps the government could make a cash transfer to a citizen, but limit where the citizen can use that cash.
-
Unlike a cryptocurrency like Bitcoin, the digital yuan is issued directly by China’s central bank and does not depend on a blockchain. The currency has the same value as its analog equivalent, the yuan or RMB, and for consumers the experience of using the digital yuan is not that different from any other mobile payment system or credit card. But on the back end, payments are not routed through a bank and can sometimes move without transaction fees, jumping from one e-wallet to another as easily as cash changes hands.
Not a cryptocurrency, not a bank card
-
The hope for government-sanctioned digital currencies is that they will improve efficiency and spur innovation in financial services. But tech and China experts watching the country’s project say that eCNY, also known as the electronic Chinese yuan or digital yuan, also opens up new forms of government surveillance and social control. The head of UK intelligence agency GCHQ, Jeremy Fleming, warned in a speech last month that Beijing could use its digital currency to monitor its citizens and eventually evade international sanctions.
Improve economic efficiency, but also surveillance
-
Government officials are urging citizens to adopt the official digital currency in a bid to gain more control over the economy.
-
-
www.epsilontheory.com www.epsilontheory.com
-
This circular process of issuing new shares to employees and then buying those shares back with company money – MY money as a shareholder – is called ‘sterilization’.
Definition of stock “sterilization“
-
-
theintercept.com theintercept.com
-
“There is growing evidence that the legislative and executive branch officials are using social media companies to engage in censorship by surrogate,” said Jonathan Turley, a professor of law at George Washington University, who has written about the lawsuit. “It is axiomatic that the government cannot do indirectly what it is prohibited from doing directly. If government officials are directing or facilitating such censorship, it raises serious First Amendment questions.”
Censorship by surrogate
Is the government using private corporations to censor the speech of Americans?
-
Under President Joe Biden, the shifting focus on disinformation has continued. In January 2021, CISA replaced the Countering Foreign Influence Task force with the “Misinformation, Disinformation and Malinformation” team, which was created “to promote more flexibility to focus on general MDM.” By now, the scope of the effort had expanded beyond disinformation produced by foreign governments to include domestic versions. The MDM team, according to one CISA official quoted in the IG report, “counters all types of disinformation, to be responsive to current events.” Jen Easterly, Biden’s appointed director of CISA, swiftly made it clear that she would continue to shift resources in the agency to combat the spread of dangerous forms of information on social media.
MDM == Misinformation, Disinformation, and Malinformation.
These definitions from earlier in the article: * misinformation (false information spread unintentionally) * disinformation (false information spread intentionally) * malinformation (factual information shared, typically out of context, with harmful intent)
-
The stepped up counter-disinformation effort began in 2018 following high-profile hacking incidents of U.S. firms, when Congress passed and President Donald Trump signed the Cybersecurity and Infrastructure Security Agency Act, forming a new wing of DHS devoted to protecting critical national infrastructure. An August 2022 report by the DHS Office of Inspector General sketches the rapidly accelerating move toward policing disinformation. From the outset, CISA boasted of an “evolved mission” to monitor social media discussions while “routing disinformation concerns” to private sector platforms.
High-profile hacking opens door
In response to the foreign election interference in 2016 and high-profile hacking of U.S. corporations, the 2018 Cybersecurity and Infrastructure Security Agency Act expanded the DHS powers to protect critical national infrastructure. The article implies that the social media monitoring is grounded in that act.
-
DHS’s mission to fight disinformation, stemming from concerns around Russian influence in the 2016 presidential election, began taking shape during the 2020 election and over efforts to shape discussions around vaccine policy during the coronavirus pandemic. Documents collected by The Intercept from a variety of sources, including current officials and publicly available reports, reveal the evolution of more active measures by DHS. According to a draft copy of DHS’s Quadrennial Homeland Security Review, DHS’s capstone report outlining the department’s strategy and priorities in the coming years, the department plans to target “inaccurate information” on a wide range of topics, including “the origins of the COVID-19 pandemic and the efficacy of COVID-19 vaccines, racial justice, U.S. withdrawal from Afghanistan, and the nature of U.S. support to Ukraine.”
DHS pivots as "war on terror" winds down
The U.S. Department of Homeland Security pivots from externally-focused terrorism to domestic social media monitoring.
-
-
docdrop.org docdrop.org
-
the container ship was simply becoming so large so unwieldy that much of the infrastructure around them is struggling to cope a lot of the decisions to build Supply chains were really based on
Impact of cheap transportation
production costs and transport costs
With transportation costs so low and logistics assumed, manufactures chased cheaper production costs. They would outsource manufacturing to low-cost countries without considering the complexity risks.
-
the industry agreed that the standard container sizes would be 20
Standardization effort
feet and 40 feet.
In 10 years of negotiation, the standards committee agreed on the container specifications, including dimensions, corner post attachments.
-
at the same time the US Army had been experimenting and seeing success with their smaller container Express or context boxes during the Korean war
U.S. Army containerization efforts in the Korean War
Somewhere I read about how containerization was driven by the U.S. Army's needs to standardize transport to Korea, and the Oakland, California, docks were the first to see container cranes. I can't find the source of this anymore, though.
-
he understood that rather than adapting the container to suit the industry it was the industry and its entirety that would have to adapt trucks trains and ships ports and dockyards would all have to
Containerization's disruptive innovation
fit the container not the other way around.
McLean's big contribution is the need for an upheaval in the industry—that the standardized container was the building block and everything else around it had to change.
The resulting disruption affected dock workers, the support infrastructure around ports, and even the port cities themselves.
-
he'd over time built a very large trucking company in the United States he became worried in the
Malcom McLean
early 1950s because there was an automotive boom in the United States there were a lot more cars on the road this was slowing down his lorries and he thought that maybe if he were able to put his trucks onto a ship and carry them down the Atlantic coast that he'd have lower costs and more reliable delivery.
Malcom's thought was to put the whole truck on a ship, but that wasn't effective. Instead, he put the just container from the truck body on the ship. The multimodal innovation between truck and ship proved crucial to the standardization of shipping containers. He built on earlier work by Keith Tantlinger to modernize containers.
-
it took about 11 and a half days to actually go across the Atlantic and it took about six or four days to actually unload it all in Germany
About 12% of the cost was the actual ship movement while almost 40% was the work of the longshoremen on either end.
-
break both shipping tended to be slow a vessel could spend a week or more at the dock
Breakbulk Cargo defined
being unloaded and reloaded as each of the individual items in the hole had to be removed and then each of the individual outgoing items had to be stowed away in the hold
The inefficiencies caused international shipping to be slow, expensive, subject to damage and theft. The U.S. government conducted a study in 1954 that quantified the problems with breakbulk shipping. Not only was the act of loading and unloading the cargo ship inefficient, but the need to warehouse, palletize, and store the inconsistently-shaped items was a problem.
-
Mark Levinson who has literally written the book on the shipping container called The Box how the shipping container made the world smaller and the
Marc Levinson
world economy bigger
-
How Shipping Containers Took Over the World (then broke it) by Calum on YouTube
Oct 5, 2022
The humble shipping container changed our society - it made International shipping cheaper, economies larger and the world much, much smaller. But what did the shipping container replace, how did it take over shipping and where has our dependance on these simple metal boxes led us?
-
- Oct 2022
-
www.washingtonpost.com www.washingtonpost.com
-
Mastodon gained 22,139 new accounts this past week and 10,801 in the day after Musk took over, said Mastodon chief executive Eugen Rochko. The site now has more than 380,000 monthly active users, while Twitter has 237.8 million daily active users.
Comparison of Mastodon and Twitter active user counts
Several orders of magnitude different.
-
-
www.thebureauinvestigates.com www.thebureauinvestigates.com
-
Claudia requested support through the Teleperformance scheme, which had to be approved by a supervisor, but she did not receive any help for two months. When the company’s mental health support staff finally did get in touch, they said they were unable to help her and told her to seek out support through the Colombian healthcare system.
Company redirects employees to national healthcare system for mental health support
-
Some social media platforms struggle with even relatively simple tasks, such as detecting copies of terrorist videos that have already been removed. But their task becomes even harder when they are asked to quickly remove content that nobody has ever seen before. “The human brain is the most effective tool to identify toxic material,” said Roi Carthy, the chief marketing officer of L1ght, a content moderation AI company. Humans become especially useful when harmful content is delivered in new formats and contexts that AI may not identify. “There’s nobody that knows how to solve content moderation holistically, period,” Carthy said. “There’s no such thing.”
Marketing officer for an AI content moderation company says it is an unsolved problem
-
-
www.bankinfosecurity.com www.bankinfosecurity.com
-
Advocate Aurora Health says it embedded pixel tracking technologies into its patient portals and some of its scheduling widgets in a bid to "better understand patient needs and preferences."
Alternate: “Springfield USA Library says it embedded pixel tracking technologies into its discovery portals and some of its contact-a-librarian widgets in a bid to ’better understand customer needs and preferences.’”
-
A Midwestern hospital system is treating its use of Google and Facebook web tracking technologies as a data breach, notifying 3 million individuals that the computing giants may have obtained patient information.
Substitute “library” for “hospital”
In an alternate universe: “A Midwestern library system is treating its use of Google and Facebook web tracking technologies as a data breach, notifying 3 million individuals that the computing giants may have obtained search and borrowing histories.”
-
-
scholarship.law.georgetown.edu scholarship.law.georgetown.edu
-
It is the work itself that is copyrighted, not the form.56 While works mustbe in a fixed form to qualify for copyright protection, that protection is for the workitself. Some forms are necessarily part of some types of works (e.g., sculpture), butthis cannot be said of most printed works.57 The form in which a work is fixed isirrelevant, and Congress recognized the importance of media neutrality when itadopted the language in the Copyright Act.58 Digitization changes only the form,and “the ‘transfer of a work between media’ does not ‘alte[r] the character of ’ thatwork for copyright purposes.”
Content, not form, is Copyrighted
Wu's comment on New York Times Co. v. Tasini: "Digitization changes only the form, and 'the transfer of a work between media does not alter the charachter of that work for copyright purposes.'"
-
First, digitization and distributionwould not be done for commercial gain and would be handled in a manner com-pletely consistent with a library’s function. Because the library would not beincreasing the number of copies available for use at any given time, the digital copywould not serve as a substitute for an additional subscription or purchase. Shoulddemand be so great that multiple copies were needed simultaneously, TALLOwould need to purchase or license additional copies or individual libraries withinthe consortium would need to make local purchases.
Origin of own-to-loan concept
-
Instead of the current practice of forming regional or bilateral agreementsfor resource sharing, law libraries could form a national consortium through whicha centralized collection would be established. The TALLO consortium would serveas a kind of jointly owned acquisitions department for member libraries. The dis-cussion here is limited to a collection of print and microform acquisitions anddonations
TALLO's vision included a "jointly owned acquisitions department"
The jointly owned acquisitions department would have dedicated staff, centralized storage and collection development policies (including preservation), and digitization capabilities.
-
With each purchase decision,libraries risk either losing future access to databases (including retrospective con-tent) and experiencing greater restrictions on use through license terms than are
Library acquired information at long-term risk
available to publishers under copyright, or keeping materials in print even though they might not be used as often as an online equivalent.
-
I believe it is possible to build a digital library thatrespects both of the intended beneficiaries of the Copyright Clause—copyrightowners and society—while testing commonly held assumptions about the limita-tions of copyright law. In balancing these goals, TALLO permits circulation of theexact number of copies purchased, thereby acknowledging the rights inherent incopyright, but it liberates the form of circulation from the print format.
Liberating purchased information from the form in which it was purchased
-
academic law libraries pool resources, through a consortium, to create a centralizedcollection of legal materials, including copyrighted materials, and to digitize thosematerials for easy, cost-effective access by all consortium members. For the sake ofexpediency, this proposal will be referred to here as TALLO (Taking Academic LawLibraries Online) and the proposed consortium as the TALLO consortium.
Coining "TALLO" (Taking Academic Law
Libraries Online)
The [[Controlled Digital Lending]] theory was first proposed as a way for academic law libraries to form a consortium to share the expense of collection-building.
-
Metadata page: "Building a Collaborative Digital Collection: A Necessary Evolution in Libraries" by Michelle M. Wu
103 Law Libr. J. 527-551 (2011)
-
-
calpaterson.com calpaterson.com
-
An oracle is a conventional program which runs off the blockchain and which periodically publishes information about the world onto the blockchain. The problem is trust. Using an oracle turns your clever blockchain program into a fairly pointless appendage to the much more important (and subjective) conventional program: the one which is interpreting the world and drawing conclusions.
Almost all smart contracts require an oracle
The oracle becomes the trusted centralized entity that advocates wanted to be removed. Can you trust the oracle? Can the oracle be subverted...even for just a short time needed to execute an encoded contract program on the blockchain?
-
If people have been doing international transfers for a thousand years, why are they still so complicated? The reason is largely KYC/AML, the compliance processes that the world financial system uses to ensure you aren't transferring money to economically sanctioned individuals, criminals, terrorists, etc. Banks won't send money to just anywhere, they first want to check that it's not at risk of going to the baddies. This can take a long time and often requires exchange of lots of complicated documents. Any blockchain-based financial transfer system that grows in popularity will be pressured by governments to implement KYC/AML and will then start to resemble traditional international transfers, except with higher charges and smaller economies of scale. Many Bitcoin brokerages have long since required identity verification for the account owner. Some are starting to require details of who you're sending money to.
Bank transfers require compliance processes
Know-your-client and anti-money-laundering compliance are based on laws that sanction individuals and criminal organizations. A blockchain version of bank transfers would require the same compliance workflows. As more money moves by blockchain, there will be more pressure on the intermediaries to comply with these laws. Unless you support the funding of criminal enterprises, I suppose.
-
When is a blockchain solution right and when is it not?
-
-
icolc.net icolc.net
-
The best way to ensure that you’re licensing a solution that will interoperate with other solutions and conform tonecessary standards is to build that understanding into your signed contract.
Contract riders for standards compliance and 3rd-party data sharing
The Strategies for Collaboration whitepaper includes sample contract language supporting (and enforcing mechanisms) for standards compliance and dealing with 3rd-party data sharing arrangements.
-
Include a CC0 or CC-BY statement in the data (including MARC records) you create. Here’s an example from theUniversity of Florida:588 _ _ $a This bibliographic record is available under the Creative Commons CC0 “No Rights Reserved”license. The University of Florida Libraries, as creator of this bibliographic record, has waived all rights to itworldwide under copyright law, including all related and neighboring rights, to the extent allowed by law.
Sample MARC 588 CC0 statement from University of Florida
-
Libraries should reestablish a professional investment in technology. This requires a shift in mind-set, where the “waitand see” approach of library led projects within the open source arena should be instead fed and funded within thepublic funding model, otherwise we will perpetually delay our own empowerment. As stated earlier in this report,libraries should be asking “why not open source?” as a primary question early in the procurement process. If it’s notfeasible to develop in-house resources, partnering with a vendor who supports open source (so long as that vendorhas a commitment to the long-term success of the overall open source community) may be a good option. Or workwith groups of libraries, consortia, or collaborations between consortia to build investment in skills
Libraries should invest in technology
Move beyond wait-and-see; libraries should be active participants.
-
This shift in funding may require shifts inlibrary procurement rules (e.g., rethinking RFP requirements to consider open source solutions; exploring models tofund open source development pre-adoption), so in the short term we recommend working within existingorganizations.
Support for funding pre-adoption development of open source
The problem of how to use the RFP process to compare open source and proprietary systems—when you can get a vendor response for an open source system—is well known; changing procurement requirements is hard, but would be valuable.
The other part stated here—models for funding pre-adoption feature development of open source—is new to me. This is a good way for a library to get involved in an open source community. It invigorates the community with new ideas and new people, and it can fund work that the collective needs.
-
We cannot continueoperating with a status quo mentality and expect to achieve a different result. A paradigm shift is needed in howlibraries allocate our increasingly limited funds. Our budgets are currently beholden to maintaining the status quo,usually with vendors whose pricing increases annually. Rather than continuing to fund proprietary development, wepropose reallocating a portion of what we expend with those vendors for deliberate investment in library-created orcommunity-owned solutions.
Decide to move beyond status quo allocations
The status quo leads to dwindling resource and dwindling control over the library's future. Libraries can chose to spend on "library-created or community-owned" solutions instead of funding proprietary—and private—development.
-
In addition, open source solutions are “community-owned” or licensed by a community with a direct stake in thatsolution’s remaining open and available to others.
Community-owned open source in library field
This is generally true in the library field, but is not generally true outside of libraries. There are many cases where a company supports an open source solution but has a more advanced or more feature-rich version that is available with a proprietary license or only available on the vendor's hosting platform. The counter-example in libraries, I think, is the U.S. PTFS handling of their [[Koha]] extensions.
-
Providers supporting open source systems can be a useful entry point for libraries thatmay not have the resources to do in-house development but still wish to move to an open source solution. It is criticalto ensure that those vendors support the larger open source project community and contribute their work back to theoriginal code base.
Importance of vendors providing open source support contribute back to the community
-
These trends are further exacerbated by a dwindling supply of library personnel and the professional expertisenecessary to support library infrastructure in-house. Even the largest and most successful information technologycompanies struggle to hire and keep the technologists and software developers they need; libraries aredisadvantaged in attracting and retaining individuals and software support from this same pool of talent. This perfectstorm has led to a critical lack of capability and capacity and “learned helplessness” in the face of increasinglyprivatized information, the politicization of knowledge, and the commoditization of analytics and other services.
Dwindling supply of library personnel and professional expertise
Library technologists are in short supply; it is hard to attract talent as compared to other information technology fields. To what extent have companies in the library field also cannibalized talent from libraries?
-
In the United States, funding is woefully inadequate across the library sector. The global Covid-19 pandemic hasexposed everything that was not working well (or at all) but was papered over with good intentions. The blunt traumaof decades of disinvestment in the public sector, particularly in education, has left libraries lacking many of the coreresources necessary to function effectively. While libraries can and should continue to advocate for additional funding,current political climates, an uncertain economy, the declining number of high school graduates across many regions,and the continuing fallout from the pandemic mean that increased funding is unlikely in most cases. Library workersdedicated to the profession of literacy and equal access to information are now called on to defend traditionalprinciples with few resources to ward off assaults.
Covid exposes systemic under-support
The effects of the Covid pandemic have brought to the surface the underlying reduction in support that has affected libraries for the past few decades.
-
Underpinning all these strategies is a recognition that libraries – even the largest, best-funded ones – mustcollaborate to accomplish their missions. Conversely, even the smallest, poorly-funded libraries can be valuedcontributors to these efforts. Consortia can play a unique role in this undertaking, working with all their libraries –however big or small, no matter their funding – to identify strategies that work for their libraries and bring themtogether to regain collective agency, power, and control.
Libraries of all sizes can take part
There are few "largest, best-funded" libraries and many "smallest, poorly-funded" libraries. And important point of recognition is that libraries of all circumstances have something to contribute—a lot or a little.
-
Linked from Strategies for Collaboration: Opportunities and Challenges to Build the Future We Need | ICOLC Website.
-
-
pluralistic.net pluralistic.net
-
They propose a bunch of vectors for this: like, the attacker could control an otherwise reliable site that generates biased summaries under certain circumstances; or the attacker could work at a model-training shop to insert the back door into a model that someone downstream uses. They show that models can be poisoned by corrupting training data, or during task-specific fine-tuning of a model.
Backdoor to ML algorithms with poisoned training data
-
There's no market for a machine-learning autopilot, or content moderation algorithm, or loan officer, if all it does is cough up a recommendation for a human to evaluate. Either that system will work so poorly that it gets thrown away, or it works so well that the inattentive human just button-mashes "OK" every time a dialog box appears.
ML algorithms must work or not work
-
-
journals.library.ualberta.ca journals.library.ualberta.ca
-
Valentine, Greta, and Kate Barron. 2022. “An Examination of Academic Library Privacy Policy Compliance With Professional Guidelines”. Evidence Based Library and Information Practice 17 (3):77-96. https://doi.org/10.18438/eblip30122.
Abstract
Objective – The tension between upholding privacy as a professional value and the ubiquity of collecting patrons’ data to provide online services is now common in libraries. Privacy policies that explain how the library collects and uses patron records are one way libraries can provide transparency around this issue. This study examines 78 policies collected from the public websites of U.S. Association of Research Libraries’ (ARL) members and examines these policies for compliance with American Library Association (ALA) guidelines on privacy policy content. This overview can provide library policy makers with a sense of trends in the privacy policies of research-intensive academic libraries, and a sense of the gaps where current policies (and guidelines) may not adequately address current privacy concerns.
Methods – Content analysis was applied to analyze all privacy policies. A deductive codebook based on ALA privacy policy guidelines was first used to code all policies. The authors used consensus coding to arrive at agreement about where codes were present. An inductive codebook was then developed to address themes present in the text that remained uncoded after initial deductive coding.
Results – Deductive coding indicated low policy compliance with ALA guidelines. None of the 78 policies contained all 20 codes derived from the guidelines, and only 6% contained more than half. No individual policy contained more than 75% of the content recommended by ALA. Inductive coding revealed themes that expanded on the ALA guidelines or addressed emerging privacy concerns such as library-initiated data collection and sharing patron data with institutional partners. No single inductive code appeared in more than 63% of policies.
Conclusion – Academic library privacy policies appear to be evolving to address emerging concerns such as library-initiated data collection, invisible data collection via vendor platforms, and data sharing with institutional partners. However, this study indicates that most libraries do not provide patrons with a policy that comprehensively addresses how patrons’ data are obtained, used, and shared by the library.
-
-
www.washingtonpost.com www.washingtonpost.com
-
After cornering the market on entertainment, TikTok began offering its model of behavioral tracking and algorithmic suggestion to advertisers, promising them a way to know which ads people find most compelling without having to ask. It was an instant hit: The company’s ad revenue tripled this year, to $12 billion, according to eMarketer estimates, and is expected to eclipse YouTube at nearly $25 billion by 2025. In the United States, the cost to advertisers for TikTok’s premium real estate — the first commercial break a viewer sees in their feed, known as a “TopView” — has jumped to $3 million a day.
A "TopView" advertisement runs $3 million a day
-
TikTokers are increasingly using the app as a visual search tool; 40 percent of Generation Z respondents to a Google survey this year said they had opened TikTok or Instagram, not Google, when searching for nearby lunch spots. (One tweet in June, “I don’t Google anymore I TikTok,” has been ‘liked’ 120,000 times.)And as Americans’ trust in news organizations has fallen, TikTok’s role as a news source has climbed. One in three TikTok viewers in the United States said they regularly use it to learn about current events, Pew Research Center said last month. In the United Kingdom, it’s the fastest-growing news source for adults.
TikTok as an information tool and a news tool
-
The average number of hours each American user spent every day on TikTok exploded 67 percent between 2018 and 2021, while Facebook and YouTube grew less than 10 percent, investment analysts at Bernstein Research wrote in an August report. TikTok has replaced “the friction of deciding what to watch,” the researchers said, with a “sensory rush of bite-sized videos … delivering endorphin hit after hit.”
A "sensory rush of bite-sized videos"
The quote is from a Bernstein Research article, which doesn't seem to appear as open source on the internet but was referred to in an August 23rd article on Business Insider: TikTok Compared to Crack Cocaine by Top Wall Street Internet Analysts
-
TikTok starts studying its users from the moment they first open the app. It shows them a single, full-screen, infinitely looping video, then gauges how they react: a second of viewing or hesitation indicates interest; a swipe suggests a desire for something else. With every data point, TikTok’s algorithm narrows from a shapeless mass of content to a refined, irresistible feed. It is the ultimate video channel, and this is its one program.The “For You” algorithm, as TikTok calls it, gradually builds profiles of users’ tastes not from what they choose but how they behave. While Facebook and other social networks rely on their users to define themselves by typing in their interests or following famous people, TikTok watches and learns, tapping into trends and desires their users might not identify.
TikTok uses user-interaction signals, not stated preferences or friend relationships, in its recommendation algorithm
The article describes how users are "surprised and unsettled" by the algorithm's choices for next videos. The system rewards interaction by serving up videos that are more desirable to users—a kind of virtuous cycle of surprise and delight.
-
Even as the app has transformed into a public square for news and conversation, TikTok’s opaque systems of promotion and suppression fuel worries that China’s aggressive model of internet control could warp what appears there. Many users already are self-censoring, adopting a second language of code words — “unalive,” not dead; “procedure,” not abortion — in hopes of dodging the app’s censors and preserving their chances at online fame.
Anecdotes of self-censorship to avoid algorithmic censors
A few paragraphs later in the article there is a story from a high school literature teacher that wont use the word "death" lest it might "stunt his reach."
-
former TikTok employees and technical experts argue that the company’s fixes do nothing to address its biggest risk: that its top decision-makers work in a country skilled at using the web to spread propaganda, surveil the public, gain influence and squash dissent. That crisis of trust has led to an ongoing debate among U.S. regulators: whether to more closely monitor the app or ban it outright.
ByteDance's leadership is steeped in practices of the Chinese government
-
No app has grown faster past a billion users, and more than 100 million of them are in the United States, roughly a third of the country. The average American viewer watches TikTok for 80 minutes a day — more than the time spent on Facebook and Instagram, combined.
TikTok adoption and usage
-
How TikTok ate the internetThe world’s most popular app has pioneered a new age of instant attention. Can we trust it?By Drew HarwellOct. 14
-
-
www.washingtonpost.com www.washingtonpost.com
-
The paper, published Wednesday in Nature Communications, represents the first findings of an ongoing study into long covid — the Long-CISS (Covid in Scotland Study).
Hastie, C.E., Lowe, D.J., McAuley, A. et al. Outcomes among confirmed cases and a matched comparison group in the Long-COVID in Scotland study. Nat Commun 13, 5663 (2022). https://doi.org/10.1038/s41467-022-33415-5
-
A study across the population of Scotland researched the affects of covid by comparing those with a positive PCR test with a control group that did not have covid. Vaccinations were shown to decrease symptoms. There are concerns about long-term effects as the virus becomes endemic.
-
-
storage.courtlistener.com storage.courtlistener.com
-
THE COURT: No, but they want -- you are using it as apromotional advantage by providing the service to yourcustomers. I think that's -- I think that's really obvious,isn't it?MS. RODMAN: We're using it because our customers areasking for it, and by giving our customers the tools that theyare asking for, we build good --THE COURT: And you make it -- if you make yourcustomers happy, presumably you'll get more customers.MS. RODMAN: Exactly, but that's not --
Clarivate's motivation
The court sees through the "free-out-of-the-goodness-of-our-hearts" argument.
-
THE COURT: All right. In fact, what you are doing, Ithink, is you are developing a database of information toprovide to libraries in competition with OCLC.MS. RODMAN: No, Your Honor, absolutely not
"MetaDoor is not, absolutely not, a database"
MetaDoor is not, absolutely not, a database. We are not developing a database for libraries. What MetaDoor is is a software solution that lets one library share with another library. No information ever goes into MetaDoor, ever goes to the defendants as a result of MetaDoor. It simply facilitates that library-to-library transfer which is already allowed to happen, and it gives libraries a way to do it that is not a one-by-one clunky way of doing it like they currently do.
-
And given that we're talking about this interference interms of a contract claim, we have to keep going back to thelanguage of the policy at issue, and that language says -- andI'm going to quote it if the Court will bear with me because Ithink it's important -- that the members have the right -- andit uses the word "right" in the rights section -- members whohave extracted WorldCat data representing, or enriching therecords for, their own holdings from the WorldCat database havethe right to: transfer or make available such data to other
Records use policy
libraries and educational, cultural, or scholarly institutions, whether these institutions are members or nonmembers of OCLC for these organizations' institutional or collaborative reuse.
Here the Clarivate lawyer points to the Member Rights and Responsibilities document that says members can share records. This also goes to the question of what Metadoor is — is it a compilation of records or a pointer to where records can be found elsewhere?
Note also the subtle shift from discussions of subscribers to members.
-
And I'm having trouble with a lack ofspecificity as to which records your subscribers are free toprovide -- because they created them or someone other than OCLCcreated them and -- and how the Court is going to be able todetermine in a -- in a group of data, even with an OCN numberattached to it, whether it is something that the -- yoursubscriber is -- has freedom to release or does not under yoursubscriber agreemen
What is an OCLC record
The court does seem to have its finger on the pulse of the problem. There is a mixture of data in a record—some from the subscriber, some that OCLC has added from outside sources, some that OCLC has likely generated with algorithms. The OCN provides a provenance of sorts at the record level, but there is nothing visible at the field level to say where data came from.
-
OCLC has no proprietary interest in this metadata. Ithas no proprietary interest in the OCN number. In fact, OCLChas been very clear over the years that it wants the OCN numberto remain attached to records even when they are in thesubscriber's own catalog and they are not WorldCat records, andit wants that so that it can always go back to that record,that OCN number can pull in any additional information thatwill enhance the WorldCat record, and OCLC has declared thatthe OCN number can be treated as they are in the public domainsince 2013, and at the same time, since 2013, OCLC expresslydisavowed the OCN number being used as an indication that arecord originated with OCLC and was, therefore, subject to itsmember agreement.
OCN in the public domain?
2013 was roughly the time of the record use policy debate. Was there something said about the OCN at that time?
-
the term "enhancement" I think is a bit of a misnomer. Youhave to understand where this data comes from.When OCLC creates a record, it is pulling metadata fromother sources, from public sources, from libraries themselves,from the Library of Congress, from publishers. Almost all ofthe metadata in an OCLC record comes from sources other thanOCLC. OCLC pulls that in, and they add an OCN number, which isjust a sequential number.
Ah, yes, here we go. The OCN is an identifier and not necessarily a signal that a process has been applied to the metadata.
-
Do you assign OCN numbers to all the data that you have,including data created by your subscribers?MS. MARTINEZ: We put an OCN number on any record thatOCLC enhances.So if it comes into their database and they are going toenhance it by -- kind of similarly to what I talked about onTuesday to the Court, you know, if they are going to addheadnotes or footnotes -- I'm sorry -- head notes, you know,pagination, they are going to change the way that the record issearched.
Are OCNs assigned to subscriber metadata records?
This is an interesting question. It sounds like an OCN is added to a record as soon as it enters into OCLC's database. Are there records from subscribers that have not been touched by OCLC's automated or manual processes yet still have an OCN?
-
THE COURT: How would you define a catalog?MS. MARTINEZ: So it depends, I think, on thesubscriber, because they can be different, but initiallywhen -- before a customer comes to WorldCat, obviously, theywill have their own records that haven't been touched orenhanced or cared for through the WorldCat process.
OCLC customer or member
I don't know if this is meaningful, but OCLC"s representative describes WorldCat users as "customers" and not "members". I don't know if it is possible for a library to get cataloging services without being a member of OCLC.
Later on in the answer, the lawyer refers to "the consortium" and "subscribers within the consortium".
-
-
biblioracle.substack.com biblioracle.substack.com
-
Your book is going to meet the fate of most books, and be barely read. Reportedly one-percent of books sell more than 5000 copies.
1% of books sell more than 5,000 copies?
Would be interesting to see data about whether this is true.
-
The structure and economics of publishing make absolutely no sense as a business at any level. We pretend that this isn’t the case, but as the PRH/S&S trial turned to what happens to books that go up for “auction,” it became clear that all the valuations attached to particular books are simply made up. If a publisher decides they want a book, they just keep offering more until they have it. PRH, the company with the biggest war chest, is the winner most often. If it absorbs Simon & Schuster, it will win even more often. The merger itself is a highly rational move to create an entity that is simply larger, capable of making more big bets, reaping the rewards of the good guesses, and being better cushioned for the bad ones.
The structure and economics of publishing
-
I’m actually attempting to run this newsletter on a patronage model. All of the content is free and subscriptions are purely voluntary, expressions of support for the work that receive no additional goods in exchange. The Substack algorithm tells me that if I made the content exclusive to subscribers, rather than making it free, I would increase my revenue by somewhere around 50%. At the same time, my readership would be maybe 1/8th its current size. I’ve consciously chosen readership over revenue because, A. the additional money wouldn’t really make a significant difference to my day-to-day existence, and B. knowing that I might have a few thousand people read this (as opposed to a few hundred) helps motivate me to do the work.
Newsletter patronage model
The author is choosing to put the newsletter out for free and take voluntary donations—"subscriptions". In that way the author made a conscious decision of "readership over revenue."
-
While money derived from markets is necessary at some point, the support of the art and artist is not subject to markets, but instead falls under the category of “patronage,” where the artist with the second job is a kind of self-patron.
Art and markets intersect in the form of patronage
Even when it is "self-patronage" of an "artist with a second job."
-
there is a similar exchange going on when you borrow a book from the library. In fact, libraries are specifically designed to remove the market from the equation entirely, which is why people who use libraries - even though libraries are free - are referred to as “patrons.”
On the origin of library "patron"
I'm not sure this is exactly true, but it does make for nice imagery.
-
The most prominent public patrons of books in my lifetime are Dolly Parton and Oprah Winfrey. Dolly Parton’s Imagination Library has gifted over 185 million books to children. Oprah’s Book Club not only moved millions of copies, but helped build a reading culture are big, literary books. Oprah’s book club episodes were routinely among her lowest rated, but she didn’t care.
Dolly Parton and Oprah Winfrey patronage models
-
-
link.springer.com link.springer.com
-
When I began researching the publisher-library e-lending relationship, I expected it to be straightforward. However, as I dug into the data from dozens of sources, I realized the literature on this topic is largely disjointed. I also found myself asking question after question about the supposed facts I was uncovering. I noticed conflicting information, and opinions inserted into publications that should have been reporting the facts. Data was cherrypicked, and articles were not reporting the whole truth.Whether it has been intentional or not, the library community and general media have portrayed the libraries’ side of the story as indisputable fact instead of what it really is—opinion. It became clear as I researched that, historically, libraries seem to have much more of an issue with the Big Five publishers than most of those publishers have with libraries.I have attempted to correct the error in the current literature by objectively analyzing the publisher-library e-lending events, news, policies, and research from the 2010s, in the hope that readers will gain a comprehensive overview of all sides of the story—not just one side—and see the full, complex picture of what e-lending was like during the decade.
Conclusion
The author attempts to reframe the relationship between publishers and libraries over ebooks as antagonism misunderstood. There are a number of crucial areas that she does not take into account or, I think, misinterprets.
-
They both publicly stated how much they valued libraries, and were merely trying to protect the value of ebooks (not only for themselves, but for their authors) as they became mainstream.
(Need a citation here about the the rise or fall of profit and profit margins from the Big publishers here.)
-
In March 2011, after the Vernor v. Autodesk verdict, HarperCollins made a historic change to their library contracts: rather than sell ebooks to libraries on perpetual terms, they would license their ebooks for a maximum of 26 loans, after which libraries could choose to repurchase a license to that ebook at a discounted price.Footnote 24 This applied only to new ebooks.
Neither the cited Publishers Weekly article nor the New York Times article state that Vernor v. Autodesk was the cause of the historic change, as this sentence seems to imply.
-
The 2010 court case Vernor v. Autodesk disrupted this business model by challenging the “you bought it, you own it” notion that had long been the standard for physical books.Footnote 23 Resulting from this case, ebooks were deemed computer software that only needed to be licensed, rather than physical products owned by the purchaser. This verdict meant publishers did not need to sell ebooks to libraries with the same freedoms and rights as print books.
Vernor v. Autodesk
I've read a little about this case, and I don't think it says that licensing is the only way to sell ebooks. The case does affirm that the licensing provisions trump copyright rights, but it is still possible to "sell" copies of an ebook and be covered by first-sale rights.
-
MacmillanFootnote 21 did not start e-lending until 2013.
Trying to reconcile this with what the author stated earlier:
This leaves Macmillan as the only publisher placed solely in the resister category, as they were the only publisher in the late 2010s to take an aggressive step away from e-lending.
-
This leaves Macmillan as the only publisher placed solely in the resister category, as they were the only publisher in the late 2010s to take an aggressive step away from e-lending.
The meaning of this sentence is unclear. Macmillan is the only publisher in the "resister" category and they were the only publisher to "step away" from e-ending? See comment below.
-
But over the years, the technology and process have significantly improved, reaffirming the validity that there is not enough friction in the e-lending process.
"Not enough friction" according to who?
-
Sisto, M.C. Publishing and Library E-Lending: An Analysis of the Decade Before Covid-19. Pub Res Q 38, 405–422 (2022). https://doi.org/10.1007/s12109-022-09880-7
-
Ebooks are a software product; they never deteriorate, so libraries theoretically never need to buy a new copy.
"Ebooks never deteriorate"
The author states that there is a theoretically endless supply of ebooks. She does not take into account the implementation and maintenance costs of systems needed to serve ebooks to patrons.
-
-
media.dltj.org media.dltj.org
-
And what what I like to do in the show and in the book is have people notice those things so that they are aware of all the design decisions that are made around them to make their life a little bit better because it is really easy to not see these things and really think that you're on your own in the world, but you're not, you know, there's a bunch of people that thought about a problem that you've never even thought about and solved it before. You even had to encounter it. And it makes the world more clearly reflect that we are like interconnected group of people that are trying to create a place where we can all live and thrive. And those breakaway bolts are a great example of this.
Unnoticed design
The intention of design can go unnoticed, and people may not think of the factors and the expertise that went into making that conscious design choice.
-
sidewalks became, you know, places for us to sit and congregate when they used to just be the domain or you know, even into the roads that used to just be the domain of roads, like no one took away a road from anybody. But, but like all of a sudden you could form a cafe and people accepted that. And the thing that I love about thinking about cities is that when you're in them, there's a habit of thinking these this thing is the way it is, it was this way when I was born into this world and noticed it and it's very hard to change. But they've always been these evolving entities that reflected our values.
Design in cities as a reflection of values
At a time when space to meet outdoors was valued more than as a venue for cars to pass through, streets were given over to cafes to put outdoor seating. The intended use of a space can change over time.
-
Tony Schwartz. He had this theory that if done well, radio would be more compelling than television because it had more power over the imagination
Radio more compelling than television
-
this story of the Montgomery ward complex, that's that's along the river. And Montgomery Ward is, you know, kind of long gone as a company. But there's this one, the headquarters building was this kind of generic, um, rectangular, modernist building. But they had these four concrete post on the corner and I passed this building all the time. I'd never cared much for it. And then the architecture of the curator on the boat, the docent said that, Well, the reason why that building is the way it is, is that the Montgomery Ward Company sort of prided itself on its egalitarian hierarchy. And they wanted to build their headquarters so that there were no um, VPs fighting over who got the corner office. And so they made a building with no possibility of a corner office at all.
Montgomery Ward complex built with no corner offices
In a reflection of the company's values, its headquarters was built without the possibility of corner offices. The design of the building eliminated them as possibilities.
-
From the smallest details to the large scale infrastructure, every piece of the city was thought about designed and built by someone to make one large living thing we could all inhabit together when it all works well. It enables our society to work well too.
The City as complexity-built-on-complexity
-
-
www.newyorker.com www.newyorker.com
-
N.T.P. works by telling computers to send tiny, time-stamped messages to time-checking devices superior to them in a hierarchy. The hierarchy’s uppermost layer consists of servers that are closely connected to highly accurate clocks kept in tight synchronization with Coördinated Universal Time. The time then trickles, from strata to strata, to the machines at the bottom of the hierarchy, such as ordinary laptops. The protocol tracks the instants that elapse as a time-checking message is sent, received, returned, and received again by its original sender. All the while, a collection of algorithms—the “popcorn spike suppressor,” the “huff-n’-puff filter”—sifts through the data, singling out falsetickers and truechimers and instructing the clocks on how to adjust their times based on what the time-stamped messages tell them.
NTP description
-
He started work at COMSAT, where he had access to funding from the Department of Defense, some of which was earmarked for the ARPANET. “It was a sandbox,” he later told an interviewer. “We just were told, ‘Do good deeds.’ But the good deeds were things like develop electronic mail, and protocols.”
Early ARPANET: Do Good Deeds
-
Vital systems—power grids, financial markets, telecommunications networks—rely on it to keep records and sort cause from effect. N.T.P. works in partnership with satellite systems, such as the Global Positioning System (G.P.S.), and other technologies to synchronize time on our many online devices. The time kept by precise and closely aligned atomic clocks, for instance, can be broadcast via G.P.S. to numerous receivers, including those in cell towers; those receivers can be attached to N.T.P. servers that then distribute the time across devices linked together by the Internet, almost all of which run N.T.P. (Atomic clocks can also directly feed the time to N.T.P. servers.) The protocol operates on billions of devices, coördinating the time on every continent. Society has never been more synchronized.
“Society has never been more synchronized”
-
“I always thought that was sort of black magic,” Vint Cerf, a pioneer of Internet infrastructure, told me.
Vint Cerf on NTP
If Vint Cerf thinks it is black magic, you know it is going to be deeply complex code. The rest of the article bears this out.
-
- Sep 2022
-
-
On the part of the searcher one move that a lot of people now use is they will use google with the keywords that they have to search for but tell it to only search Reddit increasingly people are turning to Reddit to search for information but they're using google to do it because read its own search function is supposedly not very good.
Google site search Reddit for higher quality results
Use the
site:reddit.comphrase to search just Reddit. -
Search engines like google so often missed their mark is because unlike say a librarian's approach, which might be more like here are 10 books you could read to try to figure out on your own, Google tries to give you the most popular quote, unquote best search results. In other words, a direct answer, it can sort of understand what's on a web page. Find the information that it thinks you're looking for based on its statistical analysis of all of the billions and billions of searches that it sees all the time and feed you an answer and we now have come to think, oh well that must be the answer then.
Google Search is not like a reference interview
Google Search tries to give you the answer. A reference interview guides you to sources where you learn your own answer.
-
It felt like we had finally made it to the very top of human knowledge and it felt like not a constrained experience. It felt like, oh that's done, that's fixed. It works. In fact the google search bar with all of its millions of data points is so good. It changed our expectations of what search is and today that's part of the problem. We were all trained very well to think well now search bars are just like the google search bar everywhere and everywhere. I see a search bar, it's going to be just as good as a google search bar is and then you try that on amazon. For many of us when we type a query into an e commerce website, we expect that the results will be ranked for us by relevance to our search but that is not how it works. So a place that's trying to sell something is trying to sell. Like if it has more of one thing in its warehouses than another, it'll try to push that onto you. If it has something that's on sale, it might show you that first. If it has a product where the people who make it have a pay for play deal with the e commerce site, it'll show you that stuff first. The result is that the thing you search for that you're trying to buy will be buried by results for stuff that the company wants you to buy.
Applying the Google search experience to other services
Google's Page Rank algorithm might be good for searching information, but Amazon's search service has different priorities: selling you something that it wants to sell you. This is just one example of how translating the Google search experience to other domains is problematic. Another example is when there is lack of relevance context, like searching email; emails are not inter-linked with each other.
-
they get billions and billions and billions of searches every day and only about 15% of the searches that they've seen a given day. Our new that they've never seen before. So 85% of the searches that the world does on Google every day are things they've already seen.
15% of daily searches are unique
Or, put another way 85% of searches are something that Google has seen before. There is no citation for this, and I think it is more complex than this because Google uses signals other than the keyed search to rank results. Still, an interesting tid-bit if the source could be tracked down.
-
The same way that ants tell each other there's food over there, but not over there. If an ant walks over the trail and leaves pheromones on it again and again and again, that trail becomes more important to the colony pretty soon with the help of page rank google became a verb.
Google Page Rank compared to ant pheromone trails
-
Whereas searching by topic like you would in a library is similar to looking through the table of contents of a book. Keyword search is like using the index. It is much more precise and searching by keyword worked well for a time when you type in a word and get only a couple of dozen results.
Topical subject (table of contents) versus Index (search)
-
So in 1945, van ever took to the page and dreamed up an imaginary futuristic solution to the problem of search. A machine called mimics. The mimics would make search easier. It would look like a desk. There'd be a keyboard, viewing screens and storage space for all of human knowledge as long as it was on microfilm and could fit into a dust drawer on the left side there would be all the information in the universe and it would all have links. And then on the right side you would follow those links for the information you wanted. So the search became about connections within the what you were looking for theoretically the user could teach the mimics which words were relevant to each other. So if the word vulture and one document makes me think of death, I could tell the mimics to connect those two words. Then when I search for the word vulture, all the documents featuring death that I previously linked would show up, I could scroll through all the results by turning a crank. In essence, the mimics user could build their own little analog algorithm for search.
Vannevar Bush's 1945 Memex machine
Memex - Wikipedia for more details. Including creating "trails" of items and linking entries together.
-
Google was essentially a person, a reference librarian. If you wanted to find something on say growing vegetables, you could go to the gardening or farming sections of the library. But in the thousands of books in that huge section you'd quickly get overwhelmed. That's where reference librarians and archivists come in. They take your topic and help you narrow it down even further, applying their own nuanced knowledge and specialized training to help you search better and find exactly what you're looking for. That's how search operated for centuries by topic mediated by human to human interaction and it works pretty well.
Reference librarians compared to Google
Oh, yes, the classic reference interview...asking open-ended questions, probing for more details about what is being sought, then directing the user to the most appropriate resources.
-
She was a librarian. They were really well organized. The books held all the knowledge that Adam's grandmother wanted to access. It was arranged by topic and author, complete with important search tools, notes and tabs stuck into all the various volumes that she could reference when looking to pull up some tidbit of information.
Librarian's old-school Zettelkasten
This has hints of a printed-on-cards Zettelkasten index. And [[Roman Mars]] is comparing the forgetting of the structure to how leaning on digital search systems has decreased our ability to find stuff.
-
-
-
Some children could adapt better without them than others. Throughout his career in education, Pederson has never heard a single parent complain about data protection. But after the Google ban, he did receive complaints—mostly from parents of dyslexic students, who rely on Chromebook tools such as AppWriter.
Children miss the Chromebook capabilities
Students that were using accommodations on the Chromebook were now without them.
-
The Google ban was partly imposed because the data protection regulator discovered Helsingør never carried out a full risk assessment for Google’s school products before using them, as required under Europe’s GDPR privacy law, according to Allan Frank,
School district did not conduct a risk assessment
School districts did not have the resources to conduct the assessment. There was a go-with-the-flow attitude, but since we’re concerned about the extent that personal data was being shared with an American company. Done of those we’re concerned about the US government’s ability to access that data.
-
Denmark’s data protection regulator found that local schools did not really understand what Google was doing with students’ data and as a result blocked around 8,000 students from using the Chromebooks that had become a central part of their daily education.
Danish data regulator puts a temporary ban on Google education products
-
-
pluralistic.net pluralistic.net
-
That hypothetical "interoperable Facebook" is the subject of a new white paper and narrated slideshow I've just launched with EFF, called "How to Ditch Facebook Without Losing Friends."
"How to Ditch Facebook Without Losing Friends"
New effort by [[Cory Doctorow]] and EFF.
-
Now, digital technology has intrinsically low switching-costs, because the only digital computer we know how to build – a Turing-complete Von Neumann machine – can run every program we know how to write. Someone can always figure out how to plug something new into something old.
Digital technology has intrinsically low switching costs
I usually say this as "it's all ones-and-zeros, it just matters how we slosh the ones and zeros around the 'net". But invoking Turing-complete is a much more academic way of saying this.
-
Facebook users claim to hate the service, but they keep using it, leading many to describe Facebook as "addictive." But there's a simpler explanation: people keep using Facebook though they hate it because they don't want to lose their connections to the people they love.
Facebook isn't addictive; people don't want to face the switching cost
-
-
bam.kalzumeus.com bam.kalzumeus.com
-
They found out that there are truths evident on maps which distances do not full capture which influence customer behavior. One, extremely relevant in Chicagoland and having no rational explanation, is that users prefer not to drive through forest preserves on the way to their bank branch; they’ll go substantially out of their way to avoid mixing greenery with their money.
People won't drive through forest preserves to a bank (?)
The author describes the work of John Melaniphy in locating bank branches and states that "users prefer not to drive through forest preserves on the way to their bank branch." A cursory Google search didn't bring up anything relevant, but this would seem to be a fascinating thing to research.
-
A curb cut is authority granted to you by the owner of the road (often the state government) to make a physical change to your property and the road to allow customers access. Curb cuts alter the properties of traffic management at a block-by-block engineering level.
Definition of "Curb Cut"
-
The branch network is an extension of advertising, sometimes extremely literally; there are branches which exist for no purpose other than “had a city-approved large billboard adjacent to a thoroughfare with hundreds of thousands of desirable commuters daily.” The bank built the branch and staffed it with about half a dozen professionals as the cost of being able to put their logo on the billboard for half a century.
Branch banks as foci for advertising
The author describes a situation where a branch was situated so it had control over a prominent billboard; the story is unattributed, but seems plausible.
-
Bank branches are not destinations. Like Starbucks and cell phone shops, they rely on capturing your day-to-day custom when you’re out and about. In the U.S., that mostly means being maximally accessible by cars. (In Japan, and other places with different transit behavior, bank branches are among the most likely user for large parcels directly adjacent to hub train stations, with smaller light branches and ATM-only locations being deployed close to far-from-station workplaces.)
Bank branches are not destinations
Banks situate themselves along the paths that people travel...they are not destinations in and of themselves. So placement of branches are guided by modes of transportation: easy car access when cars at the main mode of transport; near transit stops when public transportation is the main mode.
-
-
banks are privately funded public infrastructure.
Banks as privately-funded public infrastructure
Earlier the author described banks as an institution that "touches most people, particularly in the middle class and above." This has me wondering about the testing program to have post offices in the U.S. offer banking functions for lower income people. That would be quasi-public infrastructure filling a gap in the privately funded offerings.
-
-
icolc.net icolc.net
-
When contracting with vendors that support open source, ensure that they commit to support future development of the underlying system and contribute their developments back to the community.
Use contracting to align vendor values with library values
Put in place agreements with open source support vendors that ensures a long-term commitment to the project by contributing spec development back to the community.
-
We recommend a three-pronged approach that combines both local and larger-scale actions.
Recommendations:
- STRATEGY ONE – Radically Rethink Our Operations to Build the Future We Need
- STRATEGY TWO – Reframe Contracts for Proprietary Services
- STRATEGY THREE – Design, Support, and Fund Alternative Solutions Now (“Alternative solutions” include open source, collaborative, and community-driven initiatives.)
-
libraries of all types must be able to select the services, platforms, and technology providers that match organizational values and meet both long and short-term needs. To that end, we argue that libraries must empower themselves by reestablishing agency and reasserting control over the technical infrastructure critical to libraries' success.
Importance of organization values
The first paragraph of the [[ICOLC]] call-to-action has libraries taking control of their destiny (my words). That libraries must be active participants in their technical infrastructure and not passive consumers.
-
The “Library First Principles” identified by BTAA call for libraries to become the “long-term guardian and preservers of research products” and support “egalitarian access to the tools of knowledge creation.” BTAA’s call for the effective in-housing of library systems through collaboratively owned and supported infrastructure is pivotal in building a sustainable future for libraries.
Library First Principles
As described by the Big Ten Academic Alliance, libraries have a "guardian" and "preserver" role for "research products". This includes not only the content itself, but the systems that store and provide access.
-
-
radiolab.org radiolab.org
-
SONIA BEN OUAGRHAM-GORMLEY: Yeah, that's—that's the impression it gives. And my point is that the thought experiment is just a thought experiment. It just shows that it is possible to identify new molecules, but there's a long way between the idea and the production of an actual drug or an actual weapon.
Creating compounds is not as simple as knowing their components
The producers interview Sonia Ben Ouagrham-Gormley in the bio-defense program at George Mason University. ("I study weapons of mass destruction, particularly biological weapons.") She notes that there is more to creating a compound than knowing its ingredients. There is a science and an art to it as well. So although the source code and the data sets are open access, it still takes chemistry know-how to create the compounds.
-
FABIO URBINA: Just did a couple of copy-and-paste changes. Typed a '1' where there was a '0' and a '0' where there was a '1.' SEAN EKINS: It was that simple. It was literally that simple. LATIF: He hit 'Run' on Mega-Syn.
Selecting for harmfulness rather than eliminating it
As was noted in the paper, they reversed the filter for selecting compounds — selecting for harmfulness rather than eliminating harmful compounds. As the interview goes on, the paper authors reveal that Mega-Syn "discovered" VX and other similarly harmful compounds.
-
paper
Urbina, F., Lentzos, F., Invernizzi, C. et al. Dual use of artificial-intelligence-powered drug discovery. Nat Mach Intell (2022). https://doi.org/10.1038/s42256-022-00465-9
-
-
locusmag.com locusmag.com
-
For example, it explains why Web3 – notionally a project to remake the web without Big Tech chokepoints – is so closely associated with cryptocurrency. It’s not just the ideological notion that if we paid for things, companies would abandon surveillance and sensationalism (a dubious proposition!); it’s the idea that the internet could be remade as something that can only be used by people who have cryptocurrency tokens. The internet is not a luxury. It’s a necessity, as the pandemic and the lockdown proved. Without the internet, you are cut off from family life, healthcare, employment, leisure, access to government services, political discourse, civic life, and romance. Those are all things you need, not just things you want. If you need cryptocurrency to access these services on a replacement, transactional internet built on the blockchain, then you will do work and sell goods in exchange for cryptocurrency tokens. They will become the new hut-tax, and the fact that everyone who wants the things the internet provides has to trade work or goods for cryptos will make cryptos very moneylike.
Web3 creates a need for cryptocurrencies
If cryptocurrencies become required to do any transaction on the internet, then "everyone who wants the things the internet provides has to trade work or good for crypto".
-
Money, then, is intrinsically linked to liabilities: something is moneylike if you need it to settle some kind of obligation.
Money is tied to liabilities: the need to settle an obligation
-
thought experiment devised by economist Warren Mosler, one of the foremost proponents of Modern Monetary Theory (MMT, the theory built upon this understanding of money): Sometimes when Mosler is explaining money to an audience, he’ll hold up a handful of his business-cards and ask, “Who will stay after the lecture and help stack the chairs and mop the floor in exchange for one of my cards?” When no hands go up, Mosler adds, “What if I told you that there were gun-toting security guards at the all the exits, and they will only let you leave in exchange for one of my cards?” Every hand shoots up. Mosler has just turned his cards into money, through the creation of a non-discretionary door-tax. Now, Mosler didn’t need to get his business-cards from the audience before he could levy this tax. He is the sole supplier of his cards, and while the audience will treat them as money, Mosler won’t. Mosler doesn’t need business-cards – he needs people to help clean the lecture hall and stack the chairs. At the end of the night, when the security guards turn over all the collected cards to him, he doesn’t need them – he can’t pay for his airfare to the next lecture using his cards, or pay for his hotel room with them. Indeed, given how cheap business cards are to produce, he can just dump all those used cards in a shredder. When people say, “Government budgets aren’t like household budgets,” this is what they mean. Mosler isn’t a currency user in this thought-experiment, he’s a currency issuer. Mosler needs your work, not your “money.” He has all the money (Mosler’s business cards). You can’t get money (Mosler’s business cards), except from Mosler. When you pay your door-tax to Mosler’s armed agents, you aren’t giving him your money – you’re giving him his own money back.
Mosler's payment-in-business-cards explanation
Mosler issues the business cards and his students find them valuable. They aren't valuable to Mosler—he can just print more. But it becomes Mosler's job to keep the economy of business cards in check—too many and no one will help stack the chairs; too few and there will be students left in the room who can't leave.
-
Debt describes our best, most evidence-supported historical understanding of the origin of money in the needs of the empires of the Axial Age (800 BCE to 600 CE). As imperial armies went a-conquering, they needed some way to provision the soldiers garrisoned in their far-flung territories. The solution was elegant – and terrible. Soldiers were paid in coin, minted and controlled by the state, which punished counterfeiters with the most terrible torments. Conquered farmers were taxed in coin, on penalty of violence and expropriation. Thus: the soldiers had coin and the farmers needed it. This meant that farmers would be willing to trade their produce for coin, which meant that soldiers would be provisioned. Tax-bills were nondiscretionary liabilities: failure to pay your tax would lead to violence and ruin. The value of money, then, came from taxation – from the fact that farmers needed coins. This need rippled out through society: Even if you didn’t farm, you would accept coins in exchange for your own labor and goods, because the farmers would accept coins in exchange for food (which everyone needs), because farmers needed coin to settle their tax-debts. Coins became money because there was a nondiscretionary, terrible obligation that you could only fulfill with coins.
Doctorow summarizes the origin of money as imperial debt
Cory Doctorow is summarizing the research of David Graeber's Debt: The First 5,000 Years. A government needed to pay its soldiers, so they were paid in coins. Conquered farmers needed to pay taxes in coins, so they would exchange with the soldiers for food. Others in the village saw that coins were valuable (in exchange for food), so they exchanged their labor for coins too.
There is also a story about the British Empire imposing a "hut tax" in Africa.
-
-
www.zylstra.org www.zylstra.org
-
so I save web archive links too as an annotation
I do a similar thing—everything I annotate in Hypothesis (or simply bookmark with Pinboard) is saved in Wayback. I've considered adding a perma.cc subscription, but $170/year seems a little steep for 100 links/month.
Grabbing a local Markdown copy of articles to store locally is an interesting idea...one worth considering; thanks!
-
If you use h., I’d be interested to hear about it.
I do! 525 annotations since 2012, but I took a long break and only started re-using it late last year. The social part of annotations has been useful for me in a few cases, but for the most part I annotate to get quotes and my thoughts about them into my own Obsidian vault. (I don't use an Obsidian plugin...instead I side-load the Markdown files with a Python script.) I haven't yet added Hypothesis to my blog, but it is on my list of things to do.
I'll second what Colby said in an earlier comment: Peter Hagen's work on annotations.lindylearn.io has been invaluable in expanding the quality content that crosses my screen.
-
-
techcrunch.com techcrunch.com
-
thought to be a potential approach to create a better consensus in a world where multiple truths sometimes seem to co-exist. Today, each side argues only their “truth” is true, and the other is a lie, which has made it difficult to find agreement. The bridging algorithm looks for areas where both sides agree. Ideally, platforms would then reward behavior that “bridges divides” rather than reward posts that create further division.
Bridging-based Ranking definition
Ranking higher comments in which multiple groups can agree.
-
-
-
These records were not created for the purpose of corporate gain or fiscal sustainability, though corporations may develop enhanced services that rely on this data.
Conflicting values of libraries versus the co-op
This is the inherent conflict, I think—libraries are expressing their values through the open sharing of bibliographic data to improve services to their own patrons and to patrons of other libraries. The cooperative has similar values, but its actions appear to prioritize its own enrichment over the benefit of the whole.
-
While libraries pay substantial fees to OCLC and other providers for services including deduplication, discovery, and enhancement, they do not do so with the intent that their records should then be siloed or restricted from re-use. Regardless of who has contributed to descriptive records, individual records are generally not copyrightable, nor is it in the public interest for their use to be restricted.
Libraries are not contributing records to the intent that access can be restricted
This is the heart of the matter, and gets to the record use policy debate from the last decade. Is the aggregation of catalog records a public good or a public good? The second sentence—"nor is it in the public interest for their use to be restricted"—is the big question in my mind.
-
-
eprint.iacr.org eprint.iacr.org
-
Squint Hard Enough: Evaluating Perceptual Hashing with Machine Learning
Jonathan Prokos, Tushar M. Jois, Neil Fendley, Roei Schuster, Matthew Green, Eran Tromer, and Yinzhi Cao
Preprint: Cryptology ePrint Archive
Abstract
Many online communications systems use perceptual hash matching systems to detect illicit files in user content. These systems employ specialized perceptual hash functions such as Microsoft's PhotoDNA or Facebook's PDQ to produce a compact digest of an image file that can be approximately compared to a database of known illicit-content digests. Recently, several proposals have suggested that hash-based matching systems be incorporated into client-side and end-to-end encrypted (E2EE) systems: in these designs, files that register as illicit content will be reported to the provider, while the remaining content will be sent confidentially. By using perceptual hashing to determine confidentiality guarantees, this new setting significantly changes the function of existing perceptual hashing -- thus motivating the need to evaluate these functions from an adversarial perspective, using their perceptual capabilities against them. For example, an attacker may attempt to trigger a match on innocuous, but politically-charged, content in an attempt to stifle speech.
In this work we develop threat models for perceptual hashing algorithms in an adversarial setting, and present attacks against the two most widely deployed algorithms: PhotoDNA and PDQ. Our results show that it is possible to efficiently generate targeted second-preimage attacks in which an attacker creates a variant of some source image that matches some target digest. As a complement to this main result, we also further investigate the production of images that facilitate detection avoidance attacks, continuing a recent investigation of Jain et al. Our work shows that existing perceptual hash functions are likely insufficiently robust to survive attacks on this new setting.
-
-
s3.amazonaws.com s3.amazonaws.com
-
This research suggests that the greatest challenges faced by library systems maintainers are ageneral ignorance about the nature of this work and an unpredictable swing from invisibility tohypervisibility within the library. When the hypervisibility results from stress-inducing bugs whichare outside their control, this hypervisibility leads to negative affective experiences, apparentlyat a higher-level among women. In some cases, the affective strain results from harshcommunications from stressed coworkers. It can also be caused by the maintainer'sdissatisfaction with their inability to help others and questioning their own competence.
The personal toll of wild, unpredictable swings from invisibility to hyper-visibility
-
Vendor support, or the lack thereof, was a consistent pain point in the network. Participants feltthey could not rely on the vendor to solve bugs in the ILS in a timely manner. Most expressed alevel of dissatisfaction with the support they received. A particular theme was that of a ticketlanguishing for weeks in the tier-one support queue before escalation to someone who would fixit.
Importance of competent tier-1 support from the vendor
-
Participants identified a lack of understanding of what it is that they do as a key contributor tothe invisibility of their work. Communicating about technology can be time-consuming work andcut into one's time to accomplish other things. Nor are such communications requested. Thesense that only technology workers can or should be familiar with technology can be damagingat all levels of the library.
Relationship between invisible work and necessity of communication
If there is not an understanding in the non-technical library staff about what it is that the technical staff do, the work is effectively "invisible". Making non-technical staff aware of the work takes communication, which is an added duty. Non-technical staff may also actively avoid becoming familiar with the technical activities…perhaps a "somebody else's problem" blinder.
-
Five themes emerged from the coding: unpredictability, invisibility/time, collaboration,communication, and affective impact. Just as few jobs can be broken into truly discrete tasks,none of these themes stands by itself. The fifth theme, affective impact emerged in discussionsof the four other themes.
Themes from the library system maintainers interviews
-
A legacy ILS is one which is still used by many libraries but is no longer the focus of the vendor's activedevelopment work. In this study, that includes Aleph, Symphony, and Voyager and, with Ex Libris'spurchase of III, may soon include Sierra.
Defining "Legacy ILS" based on a company's development actions
I've found that "legacy" is often viewed from the perspective of the user/operator. This definition relies on the development activities of the creator, which is a more universal attribute (instead of the perceptions of the software status in each library).
-
In this article, maintenance is defined to include regular system upgrades, updating systemsettings, addressing bugs and issues, upkeep of integrations with other institutional systems,and minor tasks to improve user experience or support existing functions. The latter type ofwork spans maintenance and innovation,5 but when it consists of bringing existing systems intoalignment with expectations and work already being performed, it aligns closely with other areasof maintenance included here.
Working definition of ILS maintenance
-
Tillman, Ruth Kitchin. Indispensable, Interdependent, and Invisible: A Qualitative Inquiry into Library Systems Maintenance. College and Research Libraries Journal. January 2023
-
-
-
Modbus is a different protocol - you'll notice that it says request, reply, request, reply. You have to ask for data from the other end before it will be sent back. What this means is you can't cut one of those wires. You've got to have the ability to transmit data from one end to the other.
Modbus requires transmit and receive
In this jump box, the controller sends a request for a specific piece of data and the system returns it: transmit and receive. This uses the modbus protocol.
-
it turns out it was using conventional serial: you've got a receive and a transmit pair. The thing is with a lot of serial systems like this, what you can do, is you can
Security by only allowing transmit over serial; no receiving
just cut one of the lines, so the data's being transmitted from the bridge systems through to the monitoring system. There is literally no way for me to get data back in the other direction. So in this case the system was secure.
There is a stream of serial data going down the wire to the jump box, but the receive line was cut so no commands could possibly go back.
-
The thing is that people add these jump boxes - pivots between different networks - they want to get data out from the control system to the business network. They want to be able to monitor things.
Jump boxes
Devices that are intentionally added to the industrial control system network to allow access from the business network. These cross the security "air gap" set up between the networks. This is useful, though, for getting performance data from the industrial control system to the monitors and resource trackers on the business network.
-
much of hacking is about understanding systems better than those who built them and using that knowledge to do what is supposed to be "impossible"
Knowing the system you are attacking better than the builders
-
So they're vertical divisions and this has an impact on how you design the networks on them. You have what are called "RDPs" - remote distribution points - massive network switches in each one of those fire zones. And to get all of these different signals into the cabins you have what are called "cabin switches" - so every pair of cabins will have a cabin switch that does the TV, the VoIP, the water, the lighting - all of those different things.
Cruise ships are divided into vertical "fire zones"
So they go vertically down the ship, so you don't have to make holes going across to carry those cables.
Vertically down these zones are a series of cabin switches, and the cabin switch does the job of handling the VLAN trunking for access to services.
-
-
pluralistic.net pluralistic.net
-
"Any time someone puts a lock on something that belongs to you, and won't give you the key, that lock is not for your benefit."
Doctorow's First Law
In this case, that Audible is selling audio books and requiring producers to use its DRM. This, of course, makes it impossible to take your purchased/licensed content to another audio book provider.
-
-
davidgerard.co.uk davidgerard.co.uk
-
The real central control point in Ethereum is Infura — an interface to the Ethereum blockchain owned by ConsenSys. Almost 100% of useful Ethereum transactions go through Infura, because coding to Infura is vastly easier than coding directly to the blockchain. Infura has been Ethereum’s central point of control for many years.
Centralized Ethereum interface layer
Because Infura's level of abstraction is easier to code then directly on the blockchain.
-
Staking is already as centralised as mining. The Lido staking pool plus the Coinbase exchange plus the Kraken exchange add up to over 54% of total stake. Thems what has, gets.
Proof-of-stake is already centralized
Public records of the staked Ether shows that three entities have over 54% of the total stakes. These entities will reap the ongoing benefit of proof-of-stake with every block that is verified.
-
You throw away computing power as fast as possible to show you deserve the bitcoins. Your chance of winning the bitcoin lottery is in direct proportion to how much you waste. Bitcoin mining now uses over 0.5% of all the electricity in the world — for the same seven transactions per second it managed to do in 2009. Bitcoin is the most inefficient payment system in human history.
Proof-of-work effects
-
-
docdrop.org docdrop.org
-
The processing systems fee is generally fairly low, around one 10th of a percent of the total purchase. There's a large market the merchant can choose from, which can keep this cost down. Then there's the credit card's network fee, around a quarter of a percent. And the largest fee of the system also happens here. The interchange fee, it's usually around two to 3%.
Credit card fees
The interchange fee is variable, and is paid to the bank. If a merchant wants to accept a network's cards, it must accept all of the variable interchange fees.
Tags
Annotators
URL
-
-
docdrop.org docdrop.org
-
George Erasmus
Community requires common memory
Georges Erasmus, an Aboriginal leader from Canada, said, "Where common memory is lacking, where people do not share in the same past, there can be no real community. Where community is to be formed, common memory must be created." Mark Charles: Our common memory from our traumatized past. I can't find an original source for this quote.
-
they both agreed our past our history which included the enslavement of African people and the genocide of native peoples and our foundations which are based on the
Can America be great when its foundation includes the Doctrine of Discovery
doctrine of discovery and the lie of white supremacy they both agreed those things were great they disagreed if we were great in 2016 Donald said no and Hillary said yes
Make-America-Great-Again versus America-is-already-great...is this an acceptance of the fundamental unfairness of everything that hinges on the Doctrine of Discovery? From the speaker's eyes, it can't be. He goes on to say: "but the truth is we are white supremacist, racist, and sexist as a nation because of our foundations and we don't know what to do with that."
-
we only have what's called the right of occupancy to the land like a fish would occupy water our bird would occupy the air and Europeans have the right of discovery to the land the fee title to the land
"Right of Occupancy" versus "Right of Discovery"
In the 1823 Supreme Court decision of Johnson vs. M'Intosh, the court determined that the "Right of Discovery"—where title to the land flowed from the government's discovery action—trumped the "Right of Occupancy"—where the native tribe transferred title to the land. This created the legal precedent for [[land titles]].
-
a few years later our founding fathers wrote another document they started this one with words we the people of the United States this of course is the preamble to the Constitution
Inequity in the U.S. Constitution
The speaker goes on to describe the inherent inequities in the U.S. Constitution, which also says "we the people". Notably, the lack of rights for women (pointing out "51 gender specific male pronouns"), no mention of natives, and counting Africans as three-fifths.
-
this of course makes our Declaration of Independence a systemically white supremacist document that assumes the dehumanization of indigenous peoples
Declaration of Independence as a systemically white supremacist document
Whereas the Declaration calls the native people "savages" and the drafters of the Declaration wanted to maintain the ability to colonize additional lands, "All men are created equal" is only true for the "all men" that looked like the drafters.
-
few years later they wrote a letter of protest in their letter they accused the king of raising the conditions of new appropriations of land
Declaration of Independence pushes back on the right to take indigenous lands
One of the complaints in the Declaration of Independence is that the King of England changed the conditions under which settlers were taking lands from native inhabitants. The settlers wanted to keep taking land and were upset that the king no longer allowed it.
In the talk, the speaker is juxtaposing this with the "All men are created equal" statement at the beginning of the Declaration.
-
you cannot discover lands already inhabited
Fatal flaw in the Doctrine of Discovery
Papal Bulls written from 1450 to 1493 that gave permission to European Christian explorers to claim land that was not already claimed and ruled over by European explorers. It assumes the dehumanization of the existing inhabitants.
-
wherever I go around the country first just to honor them and to thank them for the years they've steward hid these lands and second to remind myself to remind us to be more humble as we walk
A Native American's view of land acknowledgement statements
on these lands acknowledging that there is a story that though that goes beyond the history that we've read and that we were taught in our schools
-
the Navajo culture when you introduce yourself you always name your four clans or a maitre lineal people and our identities come from our mother's mother
Names in Navajo Culture
-
-
bam.kalzumeus.com bam.kalzumeus.com
-
Bank branches are no longer self-contained entities. They are feeders into a lather conglomeration of services intended to draw in new customers and sell new services to existing customers.
-
In the past, branch managers were far more akin to CEO of their branch, with substantial authority to influence underwriting decisions on loans or make accommodations for customers; this is largely on the wane. At most banks they are sales player-coaches with some vestigial customer service and regulatory functions.
Bank personnel are now primarily salespeople
-
Bank branches exist to sell new accounts. They are sited to maximize new accounts and the value of those accounts. They are staffed to maximize new accounts and cross-sells to existing customers (which will often be called “relationships” at a bank). Everything down to the physical layout of branches and sometimes even the relative paucity of non-branch options ("channels" in the lingo, li
Bank branches exist to sell new accounts
-
-
bam.kalzumeus.com bam.kalzumeus.com
-
Wonder why everyone under the sun wants you to have an account on their site? One major reason is that it gives customers a history that allows a business to direct more of its anti-fraud attention to (more risky) first-time users than (less risky) multi-year regular customers. Allowing guest checkouts is a business decision to accept more fraud (and less ability to market to the customer) in return for marginal sales.
E-commerce site accounts factor into anti-fraud algorithms
-
Trust, though, is an immensely socially useful technology. Human civilization has a fundamental limitation in that all humans can be trivially killed while sleeping. Huge portions of society’s efforts go toward establishing conditions where this trivial vulnerability virtually never gets exploited.
Trust is a valuable societal concept
Civilizations spend enormous effort ensuring that trust exists.
-
That $10 to $20 billion number we threw around earlier? This is what happens to it, in the ordinary course of business. This allocation of loss is mostly automatic, virtually never involves a court or lawyer, and only sometimes takes human effort at the margin at all.
Companies accept consumer fraud as a cost of doing business
Fraud is built into the business model as an expense.
-
Fraud is a unique subset of crime which occurs, to a major degree, subject to the enforcement efforts of non-state actors. A commanding majority of all fraud which is stopped, detected, adjudicated, and even punished (!) gets those done to it by one or more private sector actors. And the private sector has, in this case, policy decisions to make, which, like the public sector’s decisions, balance the undesirability of fraud against the desirability of social goods such as an open society, easy access to services, and (not least!) making money.
Fraud in modern society is handled by non-state actors
-
Fraud is an unavoidable part of commerce in a society that values any sort of lower friction transactions. Companies accept differing amounts of fraud depending on the nature of the business. Fraud prevention and punishment is more external to government than other types of crime.
-
- Aug 2022
-
cacm.acm.org cacm.acm.org
-
"A lot of the [future] applications get tied via marketing to 5G or 6G, but in reality, they may run mostly over Wi-Fi, because with Wi-Fi 6, the [technology] went from OFDM to OFDMA, which is more like 6G," says Phil Solis, research director for IDC's Enabling Technologies team for wireless and mobile connectivity technologies and semiconductors. OFDMA (orthogonal frequency-division multiple access) is a technology in Wi-Fi 6 enabling concurrent uplink and downlink communication with multiple clients by assigning subsets of subcarriers called Resource Units (RUs) to the individual clients, supporting larger data transmission channels and greater security. "So the point is that Wi-Fi is getting better and better, too," Solis adds.
Convergence of mobile and Wi-Fi technologies
WiFi 6 introduced some technologies under consideration for 6G, so there may be a natural convergence.
-
In addition to needing to support higher data rates, sending data via air interfaces generally requires higher frequencies than are used for 4G or 5G networks. Whereas today's 5G signals tend to operate in the 3.4Ghz to 3.8Ghz range, with future 5G implementations operating up to about 5Ghz, wireless 6G networks likely will use frequencies located in the terahertz or sub-terahertz range, roughly 95Ghz to 3Thz.
Proposed frequency ranges of 95Ghz to 3Thz
At this high frequency level, propagation will become an issue, and there are experiments involving passive and active reflective surfaces in combination with higher density electronics.
-