Context: Sonia was watching Leah Remini: Scientology and the Aftermath: Season 3: "Episode 1" and had previously been watching a documentary One of Us about people who had left oppressive seeming Hassidic Jewish communities.
I can't help but that that every culture could be considered a "cult" in which some percentage of people are trapped with comparison to all other cultures on Earth. Based on one's upbringing and personal compass, perhaps living and submitting to one's culture can become oppressive and may seem particularly unfair given power structures and the insidiousness of hypocrisy.
Given this, could there logically be a utopian society in which everyone lives freely?
Even within the United States there are smaller sub-cultures withiin which people feel trapped and which have the features of cults, but which are so large as to not be considered such. Even the space in which I freely live might be considered a cult by others who don't agree with it. It's only the vast size of the power of the group which prevents the majority who comfortably live within it from viewing it as a bad thing.
A Democrat may view the Republican Party as a cult and vice versa, something which becomes more apparent when one polarizes these communities toward the edges rather than allowing them to drift into each other in a consensus.
An African American may think they're stuck in a broader American cult which marginalizes them.
A Hassidic Jew may feel they're stuck in a cult (of religious restrictions) with respect to the perceived freedoms of broader American Culture. Some may feel more comfortable within these strictures than others.
A gender non-comforming person living in the deep South of the United States surrounded by the Southern Baptist Convention may feel they're stuck in a cult based on social norms of one culture versus what they experience personally.
What are the roots of something being a cult? Could it be hypocrisy? A person or a broader group feeling as if they know "best" and creating a rule structure by which others are forced to follow, but from which they themselves are exempt? This also seems to be the way in which authoritarian rules arise when privileging one group above another based solely on (perceived) power.
Another potential thing at play here may be the lack of diversity within a community. The level of cult within a society may be related to the shape of the bell curve of that society with respect to how large the center is with respect to the tails. Those who are most likely to feel they're within a "cult" (using the broader definition) are those three or more standard deviations from the center. In non-diverse communities only those within a standard deviation of the norm are likely to feel comfortable and accepted and those two deviations away will feel very uncomfortable while those who are farther away will be shunned and pushed beyond the pale.
How can we help create more diverse and broadly accepting communities? We're all just people, aren't we? How can we design communities and governments to be accepting of even the most marginalized? In a heavily connected world, even the oddball teenager in a small community can now manage to find their own sub-community using the internet. (Even child pornographers manage to find their community online.)
The opposite of this is at what point do we circumscribe the norms of the community? Take the idea of "Your freedom to strike me ends at my nose." Perhaps we only shun those extreme instances like murder and pornography, and other actions which take extreme advantage of others' freedoms? [This needs to be heavily expanded and contemplated...] What about the over-financialization of the economy which takes advantage of the unprivileged who don't know that system and are uncapable of the mathematics and computation to succeed. Similarly hucksters and snake oil salesmen who take advantage of their targets' weaknesses and lack of knowledge and sophistication. Or the unregulated vitamin industry taking rents from millions for their superstitions? How do we regulate these to allow "cultural freedom" or "religious freedom" without them taking mass-scale advantage of their targets? (Or are some of these acculturated examples simply inequalities institutionally built into societies and cultures as a means of extracting power and rents from the larger system by those in power?)
Compare with Hester Prynne and Nathaniel Hawthorne's The Scarlet Letter.

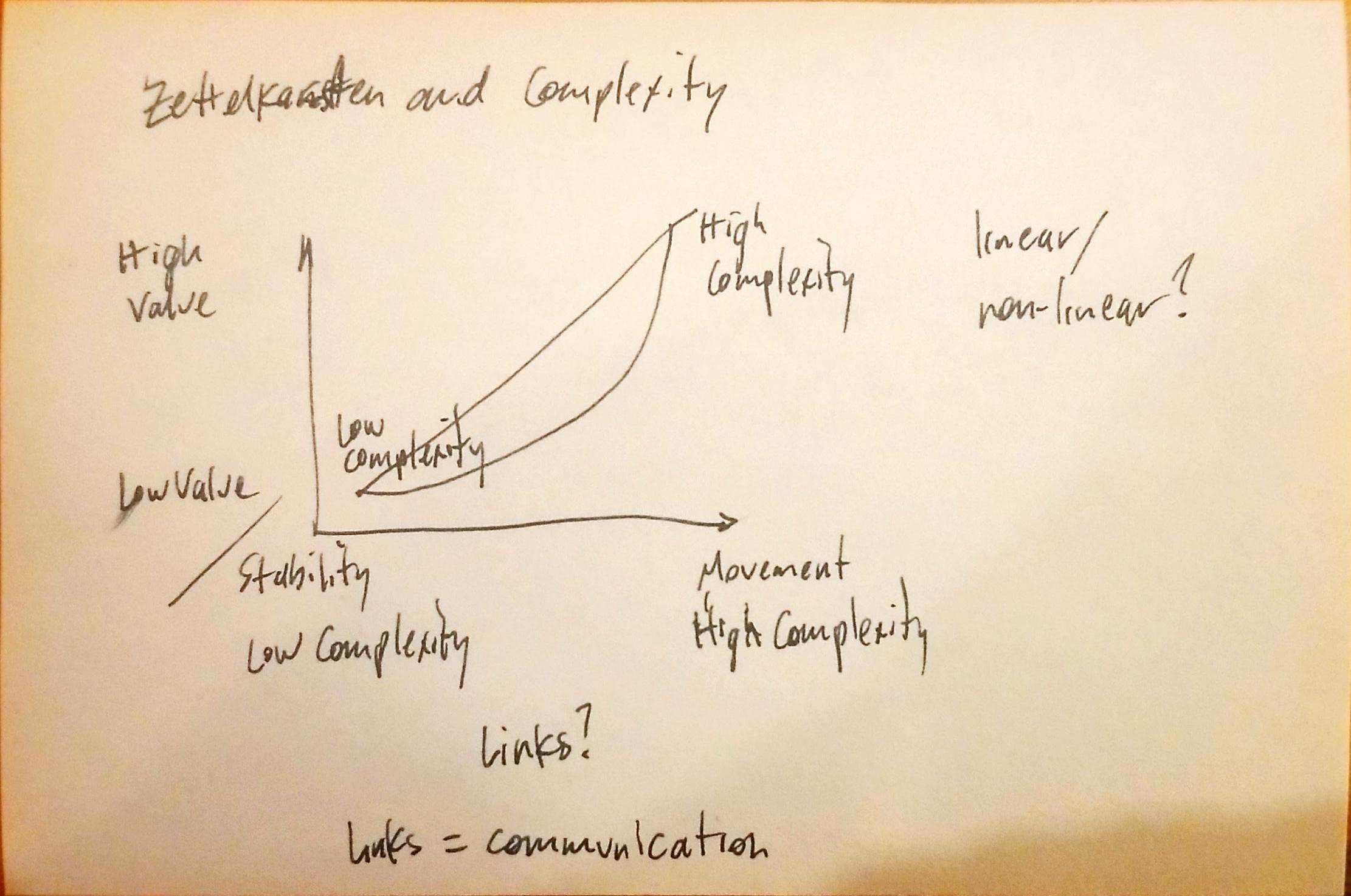
 It's a clever reworking of
It's a clever reworking of  Niklas Luhmann, Zettelkasten II,
Niklas Luhmann, Zettelkasten II, 