Alternatively, a simple public key canserve as an identifier, eliminating the DID/DIDDoc abstraction2
This would require having private key portable. Which is not secure.
Alternatively, a simple public key canserve as an identifier, eliminating the DID/DIDDoc abstraction2
This would require having private key portable. Which is not secure.
The Collapse of the Key Bridge by [[Martha S. Jones]]
A four drawer cabinetis as a rule ample for the purposes of the key cabinet.
Key cabinets are used to control the information found in other card indexes as well as for private business information which should be restricted within a firm.
The current issue revolves around an emerging disruption in mid-Atlantic supply chains. The major East Coast port is now paralyzed due to the mangled bridge blocking the only shipping lane in and out of the harbor.
Well, yes, when bridges fall in the water they block the water where they've fallen. They'll be able to focus on clearing the main channel first and get the port operating with cranes and scrapping crews once the investigation captures evidence on that section (likely scans and photographs of how they debris fell).
Not all of the bridge needs to be picked up for traffic to be restored. Highway travel impacts are likely to take longer, but adding car ferry service would be an option until a temporary span can be put in place until a permanent replacement can be erected.
In very rare circumstances, a German typewriter would be made with a dedicated swastika key, like this one at the United States Holocaust Memorial Museum.
What is the most that a working-class person could hope for from a net-zero future?
for - quote - working class - net zero - adjacency - working class - net zero - key insight - working class - net zero
quote - Chris Yates - within class - net zero - (see quote below)
it reveals that it’s those immediate experiences of the environment rather than global atmospheric concentrations of CO2 that affect people’s ideas about climate.
insight - hyperobjects
Comment - This of why a Deep Humanity approach that identifies and clarifies the fundamental issues is so important
If acting on climate change means sacrificing what little freedom I have left, then what value is that to me?
key insight - of all about the venison of individual liberty that modernization had sold is a companion bill of goods on
Then the other answered again, “Sir Gawain, so may I thrive as I am fain to take this buffet at thine hand,” and he quoth further, “Sir Gawain, it liketh me well that I shall take at thy fist that which I have asked here, and thou hast readily and truly rehearsed all the covenant that I asked of the king, save that thou shalt swear me, by thy troth, to seek me thyself wherever thou hopest that I may be found, and win thee such reward as thou dealest me to-day, before this folk.”
The Green Knight shows his excitement to take the hit from Sir Gawain's hand in response to his wanting to take on the challenge. This implies a feeling of loyalty and willingness to carry out their end of the bargain. But then the Green Knight secretly changes the terms of the first agreement struck with King Arthur by adding a new condition to their agreement. The Green Knight adds a sense of mystery as well as potential risk for Gawain when he asks him to vow on his honor to find him later and offer a prize equal to the one he received today.
Heidegger responds to this predicamentby proposing that there are, in fact, two modes of being-with-others in-the-world, one authentic and the other inauthentic. Predictably, the inauthenticmode consists in being lost in the “they.” The authentic mode, on the otherhand, consists in Dasein recovering its ownmost potentiality for Being, whichwas, from the start, “taken away by the Others.”
modes of being-with-others in-the-world
“being-there” (Dasein)
presence? being present?
“concern-for” the other (Fürsorge)
“shared world” (Mitwelt)
cogito
the principle establishing the existence of a being from the fact of its thinking or awareness.
being-with
preoriginary relation
rhetorical agency,
what’s at stake in distinguishing between a heroic theory of agency andLevinas’s agency of the host-age is the ethical relation itself.
différend
“‘response’-ability,” that “every action, discursive or otherwise, isonly born of an engagement with the set of conditions that produced it.”
we 00:11:13 have a media that needs to survive based on clicks and controversy and serving the most engaged people
for - quote - roots of misinformation, quote - roots of fake news, key insight - roots of misinformation
key insight - roots of misinformation - (see below)
quote - roots of misinformation - we have a media that needs to survive based on - clicks and - controversy and - serving the most engaged people - so they both sides the issues - they they lift up - facts and - lies - as equivalent in order to claim no bias but - that in itself is a bias because - it gives more oxygen to the - lies and - the disinformation - that is really dangerous to our society and - we are living through the impacts of - those errors and - that malpractice -done by media in America
The input format of the xargs command doesn't match what any other command produces.
It was left to a handful of keen British scholars, by no means part of themainstream, to encourage others to take up Continental philology. Murrayand his colleagues at the London Philological Society, especially its foundersEdwin Guest, Henry Malden, and Thomas Hewitt Key, were main players inenlivening the British linguistic scene and adopting the methods ofContinental philology. Now known as ‘the oldest learned society in GreatBritain dedicated to the study of language’, the Philological Society wasfounded in 1842 as a forum for discussion, debate, and work on developmentsin philology. But all this innovation came comparatively late, and theGrimms, who were made honorary members of the London PhilologicalSociety in 1843, were at the heart of the European innovations. Theyinfluenced Continental philology; they practised the application of historicalprinciples; they pioneered the descriptive method of defining and tracing aword’s meaning across time; and they forged the crowdsourcing techniquesand lexicographic policies and practices adopted by the OED editors.
What is more lacking, however, are approaches to transformation that can be applied in and adapted to multiple (and necessarily unique) contexts
for - key insight - movement of movements - What's missing - transformation catalyst - indyweb / Indranet
Doing that requires new approaches to organizing for transformation where multiple initiatives connect, cohere, and amplify their individual and collective transformative action
for - key insight - global movement requirements - new organising system - indyweb /Indranet - people-centered - interpersonal - individual collective gestalt - a foundational idea of indyweb / Indranet epistemology - Deep Humanity - epistemological foundation of indyweb / Indranet
Comment - indyweb / Indranet is ideally suited for this - seeing the mention of individual and collective in a sentence surfaced the new Deep Humanity concept of individual collective gestalt that is intrinsic to the epistemological foundation of the Indyweb / Indranet - This is reflected in the words to describe the Indyweb / Indranet as people-centered and interpersonal
one of the greatest martial arts artists ever was bruce lee who i actually read a lot of his writings
for - William Li influences - Bruce Lee - know yourself - key question to ask people - what do they really enjoy?
in general countries tend to excavate enormous volumes of earth and this earth is incredibly considered as a waste material
for - circular economy - building - excavation waste - circular economy - construction - excavation waste - key insight - repurpose excavation waste as building material
key insight - She makes an pretty important observation about the inefficiency of current linear construction process - The excavation part requires enormous amounts of energy, and the earth that is excavated is treated as waste that must be disposed of AT A COST! - Instead, with a paradigm shift of earth as a valuable building resource, the excavation PRODUCES the building materials! - This is precisely what BC Material's circular economy business model is and it makes total sense!<br /> - With a simple paradigm and perspective shift, waste is suddenly transformed into a resource! - waste2resource - waste-to-resource
new meme - Waste-2-Resource
i want to now uh introduce the key concept in in whitehead's mature metaphysics concrescence
for - key insight - concrescence - definition - concrescence - Whitehead - definition - The many become the one - Whitehead - definition - Res Potentia - Tim Eastman - definition - superject - Whitehead - definition - moment of satisfaction - Whitehead - definition - dipolar - Whitehead - definition - ingression - Whitehead definition - CONCRESCENCE - is the description of the phases of the iterative process by which reality advances from the past into the present then into the future - this definition is metaphysical and applies to all aspects of reality
Concrescence is the process by which
There's another domain that whitehead makes reference to
Whitehead describes the process of concrescence or each drop of experience as DIPOLAR, having two poles:
Each concrescence or drop of experience begins with the physical pole
and what the ingression of eternal objects do is provide each occasion of experience, each concrescence with
If the physical pole is what initiates the experience of each concrescing occasion
The subjective form is how the occasion fills the past
And so this is the most general account in Whitehead's view that we can offer
Experience is always in the present and the satisfaction that is achieved by each moment of concrescence is enjoyed in the present
once you dissolve that boundary you can't tell whose memories or who's anymore that's kind of the big thing about um that that kind of memory wiping the the wiping the identity on these 00:06:18 memories is a big part of multicellularity
for - key insight - multicellularity - memory wiping
investigate - salience of memory wiping for multicellularity - This is a very important biological behavior. - Perform a literature review to understand examples of this
question - biological memory wiping - can it be extrapolated to social superorganism?
bound by values rather than beliefs.
for - key insight - spiritual collectives - bound by values instead of beliefs
for - climate crisis - U.S. intra-country migration - key insight - climate migration - towards disaster zones
If there’s a commonality between far Left and far Right,
for - quote - commonality between far left and far right - key insight
If there’s a commonality between far Left and far Right, says Lyons,
we need to make the transition acceptable and attractive for the vast majority of citizens, and the only way to do that, is to make the changes easy to adopt. This requires strong engagement with society at large, and policies that make sustainable life choices not only easier, but also cheaper and more attractive. Or, put it the other way around, it must be more expensive to destroy the planet or the health of our fellow citizens".
for: meme - make it expensive to destroy the planet, quote - Johan Rockstrom, quote - make it expensive to destroy the planet, key insight - make it expensive to destroy the planet
key insight
As like-minded people organized, the three governance styles manifested into the three sectors (government, corporate, and NGOs). The sectors are emergent qualities of society, not a planned model.
for: elephants in the room - financial industry at the heart of the polycrisis, polycrisis - key role of finance industry, Marjorie Kelly, Capitalism crisis, Laura Flanders show, book - Wealth Supremacy - how the Extractive Economy and the Biased Rules of Captialism Drive Today's Crises
Summary
meme
is maximum returns really what we insist upon if that is the force that's driving our fragility and ecological crisis
for: key question - maximizing returns
key question
some of the biggest investors in private equity are pension funds. Those are pensions? Do we need to take our money if we have, if we're lucky enough to have a pension, out of the private markets like that? And if so, where do we put it? - Yeah, I would love to see this conversation 00:23:48 happen among institutional investors. I mean, what they have been flocking into private equity and it's the least transparent, the least accountable, the least responsible of the sectors.
for: key insight - adjacency - polycrisis - pension funds investing in private equity are a driving force
key insight
for: James Hansen - 2023 paper, key insight - James Hansen, leverage point - emergence of new 3rd political party, leverage point - youth in politics, climate change - politics, climate crisis - politics
Key insight: James Hansen
reference
Washington is a swamp it we throw out one party the other one comes in they take money from special interests and we don't have a government that's serving the interests 01:25:09 of the public that's what I think we have to fix and I don't see how we do that unless we have a party that takes no money from special interests
for: key insight- polycrisis - climate crisis - political crisis, climate crisis - requires a new political party, money in politics, climate crisis - fossil fuel lobbyists, climate change - politics, climate crisis - politics, James Hansen - key insight - political action - 3rd party
key insight
question
In the neoliberal era, individuals are forced to assume sole responsibility for navigating “every hardship and every difficulty—from poverty to student debt to home eviction to drug addiction.” When the pandemic exacerbated these hardships, it was an uphill battle to build solidarity and convince people to support collective solutions. After a lifetime of being told they were on their own, “a subset of the population” doubled down on individualism. It does not, now, seem surprising to Klein that they essentially said, “Fuck you: we won’t mask or jab
for: key insight - anti-vaxxers, key insight - conspiracy theories, key insight - maga, key insight - neoliberalism and failure at collective action
key insight: neoliberalism and failure of collective action
we need to build this this again this bridge and it's obviously not going to be written in the 00:50:41 same style or standard as your kind of deep academic papers if you think this is uh U unnecessary or irrelevant then you end up with is a scientific 00:50:56 Community which talks only to itself in language that nobody else understands and you live the general Republic uh uh prey to a lot of very 00:51:09 unscientific conspiracy theories and mythologies and theories about the world
for: academic communication to the public - importance, elites - two types, key insight - elites, key insight - science communication
comment
key insight
references
what you're referring to is the idea that people come together and through language culture and story they have narratives that then create their own realities like the 00:12:04 sociologist abely the sociologist wi Thomas said if people think people believe things to be real then they are real in their consequences
for: Thomas Theorem, The definition of the situation, William Isaac Thomas, Dorothy Swain Thomas, definition - Thomas Theorem, definition - definition of the situation, conflicting belief systems - Thomas theorem, learned something new - Thomas theorem
definition: Thomas Theorem
If men define situations as real, they are real in their consequences.[1]
In other words, the interpretation of a situation causes the action. This interpretation is not objective. Actions are affected by subjective perceptions of situations. Whether there even is an objectively correct interpretation is not important for the purposes of helping guide individuals' behavior.|
key insight: polarization
adjacency between:
adjacency statement
reference
This 1% of humanity uses its awesome power to manipulate societal aspirations and the narratives around climate change. These extend from well-funded advertising to pseudo-technical solutions, from the financialisation of carbon emissions (and increasingly, nature) to labelling extreme any meaningful narrative that questions inequality and power.
for: quote - Kevin Anderson, quote - elite positive feedback carbon inequality loop, climate crisis - societal aspirations, elites - societal aspirations, societal aspirations, key insight - societal aspirations
quote
comment
I tell my researchers look for the 00:57:41 positive feedbacks these are not good feedbacks these are self-reinforcing feedbacks where you get a cycle of of causation that causes it to reinforce itself those 00:57:52 positive feedbacks which may cross several systems like climate economic pandemic Health Systems those positive feedbacks are where you're getting the synchronization if you can find those 00:58:04 then you're making real Headway on the synchronization effect
for: adjacency - synchronization - clues - positive feedbacks, key insight - synchronisation - positive feedbacks
adjacency between
Whatever one thinks of Sultan Al Jaber, one statement he’s made repeatedly makes perfect sense: “We cannot unplug the world from the current energy system before we build a new energy system.” The focus, then, has to shift.
for: quote - Sultan Al Jabber, quote - energy replacement instead of phase out, key point - focus on energy transition instead of just fossil fuel phase out
quote
date : Dec 6, 2023
key point
the overwhelming majority of people support are not on the political agenda which is why this whole the idea that there is a center in politics is a complete fiction
for: quote - there is no center, it's a fiction, quote - James Schneider - Progressive International
quote
Although there are manyinitiatives, they have not yet reached the scale necessary to respond effectively to the crises; they oftenlack a stable and facile organisation of collaboration and a clearly structured process of joint decisionmaking
for: key insight - community capacity
key insight - community capacity
it took leadership and circumstance to ultimately 00:08:08 get a public truly mobilized
there must be a dozen bodies around the world who are trying to rethink it to some extent economics and 00:47:49 capitalism my issue with all of that is it's still within the frame that our last election was in 14 parties basically saying our future 00:48:03 is fundamentally modern now some of them might say and we want a new kind of capitalism but they're still in a modern frame and so I want to go back to your comment about Donald Trump 00:48:16 and others that there are people who kind of intuitively get it that that we do need to shake up the systems in a really serious way that we've got 00:48:29 but you see it actually took that idea seriously I mean it's just for the moment you and I agree and and anybody who's listening to this agree what we've done in effect 00:48:41 is by agreeing to be oblivious to the systems that we're actually in we have left to people who want to shake 00:48:55 up systems for their own good and in service of their own ego you end up with the Daniel Smiths on Donald Trump's and Eragon in turkey and the Prime Minister the 00:49:08 prime minister of Hungary um and Johnson who was prime minister in England uh I mean you end up with people who are thoroughly destructive yes they're perfectly willing to shake 00:49:21 things up but in a sense to no good end
Alberta is not a humble place we are not people we are extraordinarily male dominated 00:09:00 you know as well as I do that Alberta did not was not really a place where Europeans showed up uh until late in the 19th century
for: key insight - Alberta
comment
sadly the now global sustainability industry is mostly stuck with the very 00:05:03 mindset that is the root cause of the wickednesses we are in over six decades
for key insight - sustainability industry is stuck
key insight
This is key for classes and modules that are cached in places that survive reloads, like the Rails framework itself.
one of the things that is true of us I 01:13:59 dare say it is true of all of us in our own ways who are listening to this at whatever time we're listening to it and that is there are voices within as we know when we've been dismissed as a person we know when other people have 01:14:13 seen us merely as a function or have taken a quick glance of us and see nothing there a value and they just and we know how much that shrivels us up you know as we know as persons rather 01:14:26 than as functions we're taught in the modern world to take ourselves as functions to work but not your whole person and so one of the things we know as persons is that we light up like 01:14:38 lightbulbs when other persons recognize us as whole persons as a value as a person
in our modern way of thinking the dominant metaphors 01:10:43 are mechanical and in mechanical system is literally the case if you can make the system more efficient you get rid of waste so if you have parts that duplicate each other they're not needed you can get rid of one of them and 01:10:57 that's true for mechanical systems so that waste and mechanical systems can is something you can get rid of and decrease efficiency but in living human 01:11:08 and even biological systems duplication is not waste its resilience
for: key insight - modernity - inefficiency - biological system - resilience
key insight
comment
the official fantasy of the 20th century after the war but now also the 21st century is this that of course they will 00:53:15 all become like us and after the war we called it development and they were then third world countries would become first world some second world countries as well and the interesting thing is is 00:53:30 that fundamentally that really hasn't changed if you scratch under the paint of the UN's sustainable development goals what you find is they want to take the very best fruits of modernity and 00:53:42 make them in a fair way distribute them more evenly across the planet so that everybody has the advantages of a modern life and as billa suggested that's a 00:53:56 fantasy that isn't going to happen there isn't enough planet for that to happen but nevertheless this is the official fantasy it drives the OECD and the folks at Davos and the UN and most 00:54:08 universities
for: key insight - modernity framework is the major narrative, quote - modernity framework is the major narrative
key insight: modernity framework is the major narrative
we've got to leave the bottom left-hand corner and that only gives you three other spaces to go to and I've already noted that one of those spaces may be a place that has a certain utility short-run 00:50:27 but don't try to build your culture there because you can't do it it's a place that you want to be in for a while but then you wanna leave so it really only gives you two places
for: major cultural paradigms, modernity - leaving, cultural transition, cultural evolution, MET, Major Evolutionary Transition, kiey insight - 4 major cultural paradigms
comment
key insight: 4 major cultural paradigms
Due to its nature, phenomenology focuses on experiences and emphasizes the sense thatsurrounds the everyday, the meaning of the human being, that is to say, the experience of whatwe are. Phenomenology is sensitive to the problems around the world of life.The world of life represents the reality of daily life, which is investigated under a non-naive eye. This world without categories or explanations, coming from science, is the life's pre-scientific dimension, characterized by being extremely rich, a world of experiences andexperience. In this world, objective sciences are examined as cultural facts. It is the sum of bordersand horizons in which worldly facts are born and established, and which have to be regeneratedby experience. This study corresponds to the worldly phenomenology.
for: key insight - phenomenology as life's pre-scientific dimension
key insight
the main reason for this lack of 00:11:50 awareness is that our attention is almost completely absorbed into the content the what or object of our experience to the detriment of the experience itself
for key insight: object overshadows subject
paraphrase
geomorphology. That's my favorite word. I always tell my students this, I'm like, "If there's just one thing I want you 00:29:44 to learn in this class, if you do never come back, and you're just here the first two days of class, geomorphic, conforming to the shape of the land." This is, in my opinion, the fundamental flaw of our civilization is that our political boundaries and our land management units, property boundaries are not conforming to the shape of the land. Because if they did, then decisions we made would 00:30:15 have an integrated holistic landscape scale impact instead of a fragmented or fractured impact
for: key insight, key insight - Andrew Millison, key insight - geomorphology, quote, quote - Andrew Millison, quote - geomorphology
definition: geomorphology, geomorphic
quote: Andrew Millison
Take Alter's treatment of the cycle of stories in which the first two matriarchs, Sarah and Rebekah, conspire against elder sons for the benefit of younger ones. Sarah insists that Abraham drive Ishmael, his firstborn, and Ishmael's mother, Hagar, into the desert to die, to protect the inheritance of Sarah's son, Isaac. Rebekah tells her son Jacob to trick his father, the now elderly Isaac, into giving him a blessing rightfully owed to Esau, Jacob's ever-so-slightly older twin brother. The matriarchs' behavior is indefensible, yet God defends it. He instructs Abraham to do as Sarah says, and after Jacob takes flight from an enraged Esau God comes to Jacob in a dream, blesses him, and tells him that he, too, like Abraham and Isaac before him, will father a great nation.Alter doesn't try to explain away the paradox of a moral God sanctioning immoral acts. Instead he lets the Bible convey the seriousness of the problem. When Abraham balks at abandoning Ishmael and Hagar, God commands, "Whatever Sarah says to you, listen to her voice." Rebekah, while instructing Jacob on how to dress like Esau so as to steal his blessing, echoes God's phrase -- listen to my voice" -- not once but twice in an effort to reassure him. As we read on in Alter's translation, we realize that the word "voice" ("kol" in Hebrew) is one of his "key words," that if we could only manage to keep track of all the ways it is used it would unlock new worlds of meaning. In the story of Hagar and Ishmael, God's messenger will tell Hagar that God will save them because he has heard the voice of the crying boy. And the all but blind Isaac will recognize the sound of Jacob's voice, so that although his younger son stands before him with his arms covered in goatskin (to make them as hairy as Esau's), and has even put on his brother's clothes (to smell more like a hunter), Isaac nearly grasps the deceit being perpetrated against him.
Something fascinating here with respect to orality and associative memory in ancient texts at the border of literacy.
What do others have to say about the use of "key words" with respect to storytelling and orality with respect to associative memory.
The highlighted portion is an interesting example.
What do other examples look like? How common might they be? What ought we call them?
Alter's translation puts into practice his belief that the rules of biblical style require it to reiterate, artfully, within scenes and from scene to scene, a set of "key words," a term Alter derives from Buber and Franz Rosenzweig, who in an epic labor that took nearly 40 years to complete, rendered the Hebrew Bible into a beautifully Hebraicized German. Key words, as Alter has explained elsewhere, clue the reader in to what's at stake in a particular story, serving either as "the chief means of thematic exposition" within episodes or as connective tissue between them.
I'm going to kind of give you my 00:04:56 take on what I believe to have been the natural history of or what I believe is the natural history of awareness a sort of a sequence of innovations that occurred that facilitated the appearance 00:05:09 of consciousness on Earth
In this paper, we reconsider the major events in the history of life on Earth, from the first cells to the recent technological developments of human societies. We focus primarily on which METs identified by Maynard Smith and Szathmáry (1995) have produced MSTs, either directly or in combination with MCTs and catalysts. In reexamining these major transitions, we also highlight the importance of information for both the METs and the resulting MSTs, and speculate upon the role that Level V dark information may play in a future major transition.
for: research goal, research goal - METs that produce MST for life on earth
key research goal
We currently have a climate movement and a biodiversity movement. These are for the most part, two separate movements. As our understandings grow and spread of how important biodiversity is to climate, these two movements can merge and synergize.
for: key insight, climate movement, biodiversity movement, adjacency, adjacency - climate movement - biodiversity movement
key insight
AI turns semantic relationships into geometric relationships
How are the potentially selfish interests of individuals overcome to form mutually dependent cooperative groups? We can then ask whether there are any similarities across transitions in the answers to this problem.
Bash doesn't do word expansion on quoted strings in this context. For example: $ for i in "a b c d"; do echo $i; done a b c d $ for i in a b c d; do echo $i; done a b c d
Electrons, protons, quarks, and so on, what they turn out to be is just inferences that we do from marks on the screens of our apparatuses in the laboratory essentially.
for: key insight, science - key insight, science - epoche
key insight
The Chord-Scale Theory and Jazz Harmomny Netles & Graf 1997 (not searchable)
blues progressions - p 101
DKIM has proven to be a highly effective means by which a receiver can verify that the signed fields of an email have not been modified in transit. DKIM is as secure as the weakest link - the private key, though. The private key of a DKIM keypair is vulnerable to being stolen if an attacker is able to compromise the system in which it is stored. Therefore, to minimize the risk of active DKIM keys being compromised, they should be changed frequently. This is a practice known as DKIM key rotation. Each time a key is rotated, a new {selector, private key, public key} tuple is created. Then the public key will need to be published in the DNS, and you need to re-configure the outgoing email server to use the new private key. After this is done, the outgoing email server will use the new private key to sign all outgoing email messages.
In order to solve this paradox, we need to explain two aspects of consciousness: How there could be natural phenomena that are private and thus independent of physical processes (or how come they seem private), and what the exact relationship between cognitive content and phenomenal consciousness is.
Given that intelligent behavior does not require traditional brains [16,18], and can take place in many spaces besides the familiar 3D space of motile behavior (e.g., physiological, metabolic, anatomical, and other kinds of problem spaces), how can we develop rigorous formalisms for recognizing, designing, and relating to truly diverse intelligences?
Exigence
the reason why a writer is writing on a particular subject
In response to this problem, we might want to develop something like a reading ethics that is not themoralized imperative about reading all the things but a productive practice for how we read, especiallytexts that are academic or philosophic in nature.
Ah yes, because Ethics always solves what morals cannot...
we read in a linearfashion that allows the author of a written work to set the pace
Do we though? I think it's interesting that the author would begin introducing their arguement by making a reference to "ADHD-prone kids" then proceed to make a claim about how they read.
It is not uncommon to hear talk about how lucky we are to live in this age of scientific and medical advancement where antibiotics and vaccinations keep us living longer, while our poor ancient ancestors were lucky to live past the age of 35. Well this is not quite true. At best, it oversimplifies a complex issue, and at worst it is a blatant misrepresentation of statistics. Did ancient humans really just drop dead as they were entering their prime, or did some live long enough to see a wrinkle on their face?
we were designed by you know evolution through evolution we have become we were i really every organism as we'll 00:45:01 talk about in a minute is a problem-solving organism and if i can't solve problems there's like a you know like fundamentally going against the grain of what it means to be an organism
there's 00:08:43 nothing there that could be secured and here's the important point I think we experienced that we experience it as a sense of lack 00:08:58 that is to say the sense that something is wrong with me something is missing something isn't quite right I'm not good enough and the reality is I think all of us to 00:09:14 some degree have some sense of that some sense of lack even though we might ignore it or cover it up there's there's some sense of that but because it's mostly sort of unconscious in the sense that we don't 00:09:29 really know where it comes from
If you are using UUIDs instead of integers as the primary key on your models, you should set Rails.application.config.generators { |g| g.orm :active_record, primary_key_type: :uuid } in a config file.
In AET, this process results in a species that is prone to niche construction and ecosystem engineering, and the scale of these processes continues to increase as the population rises. This increasing scale coupled with human propensity for niche construction leads to human unsustainability
Ludwig firebach has this idea that religion is a place where human 00:12:22 beings sort of um alienate their intrinsic superpowers right they they turn them inside out and they push them into some kind of Heaven which is basically the future
-quote - religion is a place where human beings alienate their intrinsic superpowers - author - Timotny Morton, quoting Ludwig Feuerbach
if we want to end up with a world that is shaped by the best of us, rather than very often the worst of us, we have to think carefully, we have to engineer a system.
Why is it that despite incredible 21st century advances in every realm of medicine and science and so on, we still are stuck with all the wrong people in charge of our lives?
I found that a deep dive into death work profoundly clarified my priorities, and has helped me spend time in ways more aligned with those priorities thanks to the soul-shaking understanding that our time here is truly limited.
what is 00:02:17 history it's many parallel streams of events which meet at certain points so why not create them as parallel structures
The trouble with planning is that it only works for achievements you can describe in advance.
Reflect.
Everyone in education has a responsibility to harness thegood to serve educational priorities while also protecting against the dangers that may arise as aresult of AI being integrated in edtech
*
Annotations will be coded as shown below for easy understanding as to why notes were made. 1. Identify the Genre 2. Examine/Contrast Translation Choices 3. Assess/Contrast Modern Retellings 4. Analyze Rhetorical Strategies 5. Assess Audience Expectations
ssh-keygen -R bitbucket.org
I just did this part, then verified the fingerprint manually when repeating step 1.
Three decades of complacency has meant technology on its own cannot now cut emissions fast enough. A second, accompanying phase, must be the rapid reduction of energy and material consumption
Key observation
Clients interact with a service by exchanging representations of resources.
due to the critical role of information in phase-transitions, the primary pathway to global systemic transformation will depend on our ability to process information on our current predicament coherently in order to translate this into adaptive action.
Key observation - due to the critical role of information in phase-transitions, - the primary pathway to global systemic transformation - will depend on our ability to process information on our current predicament coherently - in order to translate this into adaptive action.
Dass das ägyptische Wort p.t (sprich: pet) "Himmel" bedeutet, lernt jeder Ägyptologiestudent im ersten Semester. Die Belegsammlung im Archiv des Wörterbuches umfaßt ca. 6.000 Belegzettel. In der Ordnung dieses Materials erfährt man nun, dass der ägyptische Himmel Tore und Wege hat, Gewässer und Ufer, Seiten, Stützen und Kapellen. Damit wird greifbar, dass der Ägypter bei dem Wort "Himmel" an etwas vollkommen anderes dachte als der moderne westliche Mensch, an einen mythischen Raum nämlich, in dem Götter und Totengeister weilen. In der lexikographischen Auswertung eines so umfassenden Materials geht es also um weit mehr als darum, die Grundbedeutung eines banalen Wortes zu ermitteln. Hier entfaltet sich ein Ausschnitt des ägyptischen Weltbildes in seinem Reichtum und in seiner Fremdheit; und naturgemäß sind es gerade die häufigen Wörter, die Schlüsselbegriffe der pharaonischen Kultur bezeichnen. Das verbreitete Mißverständnis, das Häufige sei uninteressant, stellt die Dinge also gerade auf den Kopf.
Google translation:
Every Egyptology student learns in their first semester that the Egyptian word pt (pronounced pet) means "heaven". The collection of documents in the dictionary archive comprises around 6,000 document slips. In the order of this material one learns that the Egyptian heaven has gates and ways, waters and banks, sides, pillars and chapels. This makes it tangible that the Egyptians had something completely different in mind when they heard the word "heaven" than modern Westerners do, namely a mythical space in which gods and spirits of the dead dwell.
This is a fantastic example of context creation for a dead language as well as for creating proper historical context.
Die Auswertung solcher Materialmengen erwies sich als prekär, und im Falle der häufigsten Wörter, z.B. mancher Präpositionen (allein das Wort m "in" ist über 60.000 Mal belegt) oder elementarer Verben mußte man vor den Schwierigkeiten kapitulieren und das Material aussondern.
The preposition m "in" appears more than 60,000 times in the corpus, a fact which becomes a bit overwhelming to analyze.
Auch das grammatische Verhalten eines Wortes nach Flexion und Rektion ist der Sammlung vollständig zu entnehmen. Und schließlich und vor allen Dingen lag hier der Schlüssel zur Bestimmung der Wortbedeutungen. Statt jeweils ad hoc durch Konjekturen einzelne Textstellen spekulativ zu deuten (das Raten, von dem Erman endlich wegkommen wollte), erlaubte es der Vergleich der verschiedenen Zusammenhänge, in denen ein Wort vorkam, seine Bedeutung durch systematische Eingrenzug zu fixieren oder doch wenigstens anzunähern. Auch in dieser Hinsicht hat sich das Zettelarchiv im Sinne seines Erstellungszwecks hervorragend bewährt.
The benefit of creating such a massive key word in context index for the Wörterbuch der ägyptischen Sprache meant that instead of using an ad hoc translation method (guessing based on limited non-cultural context) for a language, which was passingly familiar, but not their mother tongue, Adolph Erman and others could consult a multitude of contexts for individual words and their various forms to provide more global context for better translations.
Other dictionaries like the Oxford English Dictionary attempt to help do this as well as provide the semantic shift of words over time because the examples used in creating the dictionary include historical examples from various contexts.
Dem Konzept nach ist dies ein key word in context (KWIC) Index, ein Typus von Indices, wie sie heute immer noch als Grundoperation der Textdatenverarbeitung erzeugt werden.
The method used for indexing the Wörterbuch der ägyptischen Sprache and the Thesaurus Linguae Latinae is now generally known as a key word in context (KWIC) index.
Our findings raise the issue of global policy choices, with this research confirming that targeting the high emitters will be key. Staying within temperature limits of 1.5 °C or 2.0 °C is difficult without addressing the consequences of wealth growth.
key finding - staying within 1.5 or even 2 deg C will be difficult without addressing wealth growth - a significant share of the remaining carbon budget risks being depleted by a very small group of human beings
In this estimate, US$2020 millionaires will deplete 72% of the 1.5 °C carbon budget (400 Gt CO2, 67% chance of staying within temperature range), or 25% of the 2 °C budget (1150 Gt CO2, 67% chance) over the next 30 years.
key finding - Elite consumption has the potential to make 1.5 Deg C target unreachable - US$2020 millionaires will deplete 72% of the 1.5 °C carbon budget (400 Gt CO2, 67% chance of staying within temperature range), - or 25% of the 2 °C budget (1150 Gt CO2, 67% chance) - over the next 30 years.
The wealthy thus have a significant influence on remaining carbon budgets.
key observation
do our fears cause us to perceive the world the way we do, and might someone experience the world differently if they were brave enough to face the thing we avoid most?
Quote - do our fears cause us to perceive the world the way we do, and might someone experience the world differently if they were brave enough to face the thing we avoid most? key question - could we imagine a world where we are free of these fears?
unconscious motivations have not been eradicated by rational analysis.
The resulting focus on saving the world as a consumer, onegreen-lifestyle action at a time, blocks inspirational avenues to work-ing collectively as citizens toward the good life.
// key observation
underestimates by scientists have potentially devastating consequences for humanity’s efforts to react to this threat to our survival.
= Key point
Underestimates by scientists
The reason is Rails only reads and creates the session object when it receives the request and writes it back to session store when request is complete and is about to be returned to user.
I am Cuauhtémoc
Throughout the poem, Joaquin embodies various historical figures from Mexican history, including Cuauhtémoc (the last emperor of Tenochtitlan), Miguel Hidalgo (the father of Mexican Independence), Jose Maria Morelos (military leader during the Mexican War of Independence), Vicente Guerrero (2nd president of Mexico), Benito Juárez (26th president of Mexico), Pancho Villa (General in the Mexican Revolution which overthrew Porfirio Diaz), and Emiliano Zapata (key leader in the Mexican Revolution). All of these people are shown to care deeply about their people and their country, and their lives and deaths are seen as important parts of the story of Mexico and its path to independence and freedom.
https://www.britannica.com/biography/Cuauhtemoc https://www.britannica.com/biography/Miguel-Hidalgo-y-Costilla https://www.britannica.com/biography/Jose-Maria-Morelos https://www.britannica.com/biography/Vicente-Guerrero https://www.britannica.com/biography/Benito-Juarez https://www.britannica.com/biography/Pancho-Villa-Mexican-revolutionary https://www.britannica.com/biography/Emiliano-Zapata
we have individual capitalists who try 00:48:45 to make the most profit and this is linked to their capital and productivity so to achieve more in less time and 00:48:57 productivity is linked to energy [Music] the only source of energy to increase profit is carbon oil and gas and this has resulted in a change in our 00:49:15 atmosphere we have to put an entities if we wish to live in our planet can our capitalism do this based on the current data we won't be able to do so 00:49:28 therefore perhaps we should do the following reflection if capitalism is unable to do so either Humanity will die with it or 00:49:42 Humanity will overcome capitalism so that we can live in our planet
!- Urrego : Key Point - Can capitalism rapidly detour away from fossil fuels? The current data indicates no. So either Humanity does our it drops capitalism
Cartesian
cartesian thinking views the mind as being seperate from the physical body.
replicating an experience is not the same as replicating an exact depiction
Inthis world, stars hang in the sky but do not shine; lamps hang from ceilingsbut do not glow . The light is like a messenger that deli vers stars and lampsto the doors of your perception, but magically vanishes at the moment youlet them in
defining in terms of the negative space?
seems to emphasize the importance of context when it comes to perception
Despiteappearances, tunicates are more closely related to us than any other invertebrate — they are ourstrange, spineless cousins
The things we chose to focus on (appearances, species, habits, etc) in order to differentiate "us from them" are not that significant, we are all much more connected and similar than e realize.
The} l)'P1callyopera1c ·" ne1works 10 dc1cc1.analrze, and acru-atc re,pon<e; IO cm 1ronmental even 1,
The sensors are not only networks of analysis, detection, and responses to environmental events but are ways of describing environments and bringing them into being as sociopolitical worlds that reflect the differing ways of experiencing and navigating planetary zones.
While structural injustice and inequality do impede autonomy by fostering force and fraud, oppression and exploitation, these structural conditions also undermine autonomous self-recognition by impeding the psycho-social development integral to fulfilling the capability to be an autonomous self and agent. This is one convergence of symbiotic theorizing and the recognitional practice of autonomy. Through symbiotic practices, the assistance or “affordances” of the material and social worlds can be drawn on to actualize the inherent potential for autonomous action that resides in each human being.[16]
!- key insight : autonomy and symbiosis
What is abrogated here is our right to the future tense, which is the essence of free will, the idea that I can project myself into the future and thus make it a meaningful aspect of my present. This is the essence of autonomy and human agency. Surveillance capitalism’s “means of behavioral modification” at scale erodes democracy from within because, without autonomy in action and in thought, we have little capacity for the moral judgment and critical thinking necessary for a democratic society.
!- surveillance capitalism : key insight -mass behavioral modification takes away autonomy
Susan B. Anthony,
It is important to know that Susan was one of the people who was for women’s right to vote
our plan was not thought through in context of the time needed, our industrial capacity, and our ability to supply the raw materials needed. 00:09:04 And so a new plan is needed and a new paradigm is needed.
!- key claim : our current plan was not well thought through and we need a new plan
I have DNS settings in my hosts file that are what resolve the visits to localhost, but also preserve the subdomain in the request (this latter point is important because Rails path helpers care which subdomain is being requested)
This is an effective, dynamic stand-in for a fixed secret.
run-time dynamicness vs. hard-coded values hard-coded values = fixed secret
From the Introduction to Ed25519, there are some speed benefits, and some security benefits. One of the more interesting security benefits is that it is immune to several side channel attacks: No secret array indices. The software never reads or writes data from secret addresses in RAM; the pattern of addresses is completely predictable. The software is therefore immune to cache-timing attacks, hyperthreading attacks, and other side-channel attacks that rely on leakage of addresses through the CPU cache. No secret branch conditions. The software never performs conditional branches based on secret data; the pattern of jumps is completely predictable. The software is therefore immune to side-channel attacks that rely on leakage of information through the branch-prediction unit. For comparison, there have been several real-world cache-timing attacks demonstrated on various algorithms. http://en.wikipedia.org/wiki/Timing_attack
Further arguments that Ed25519 is less vulnerable to - cache-timing attacks - hyperthreading attacks - other side-channel attacks that rely on leakage of addresses through CPU cache Also boasts - no secret branch conditions (no conditional branches based on secret data since pattern of jumps is predictable)
Predicable because underlying process that generated it isn't a black box?
Could ML (esp. NN, and CNN) be a parallel? Powerful in applications but huge risk given uncertainty of underlying mechanism?
Need to read papers on this
More "sales pitch" comes from this IETF draft: While the NIST curves are advertised as being chosen verifiably at random, there is no explanation for the seeds used to generate them. In contrast, the process used to pick these curves is fully documented and rigid enough so that independent verification has been done. This is widely seen as a security advantage, since it prevents the generating party from maliciously manipulating the parameters. – ATo Aug 21, 2016 at 7:25
An argument why Ed25519 signature alg & Curve 25519 key exchange alg is more secure; less vulnerable to side attacks since the process that generates is have been purportedly verified and extensively documented.
US : broiler exports as a % of total production : 1.5% to 15%+
what is the same ratio for India / China
facilitate conflict resolution, improve decision-making, and sharpen patient and family assessment skills.
IMPORTANT
skills can impact how you perceive yourself and others, communicate with others, cope with change and challenge, and create a culture of safety and collaboration is vital to nursing practice and leadership
IMPORTANT
that is the key difference
If akey is lost, this invariably means that the secureddata asset is irrevocably lost
Counterpart, be careful! If a key is lost, the secured data asset is lost
Theowner of a resource is by definition the one hold-ing the private encryption keys.
definition of "owner of a resource"
都是可以根据 RoutingKey 把消息路由到不同的队列
direct模式下,同一个routingkey可以绑定不同的queue,这样路由器可以分别发送同样的消息到相应的两个queue中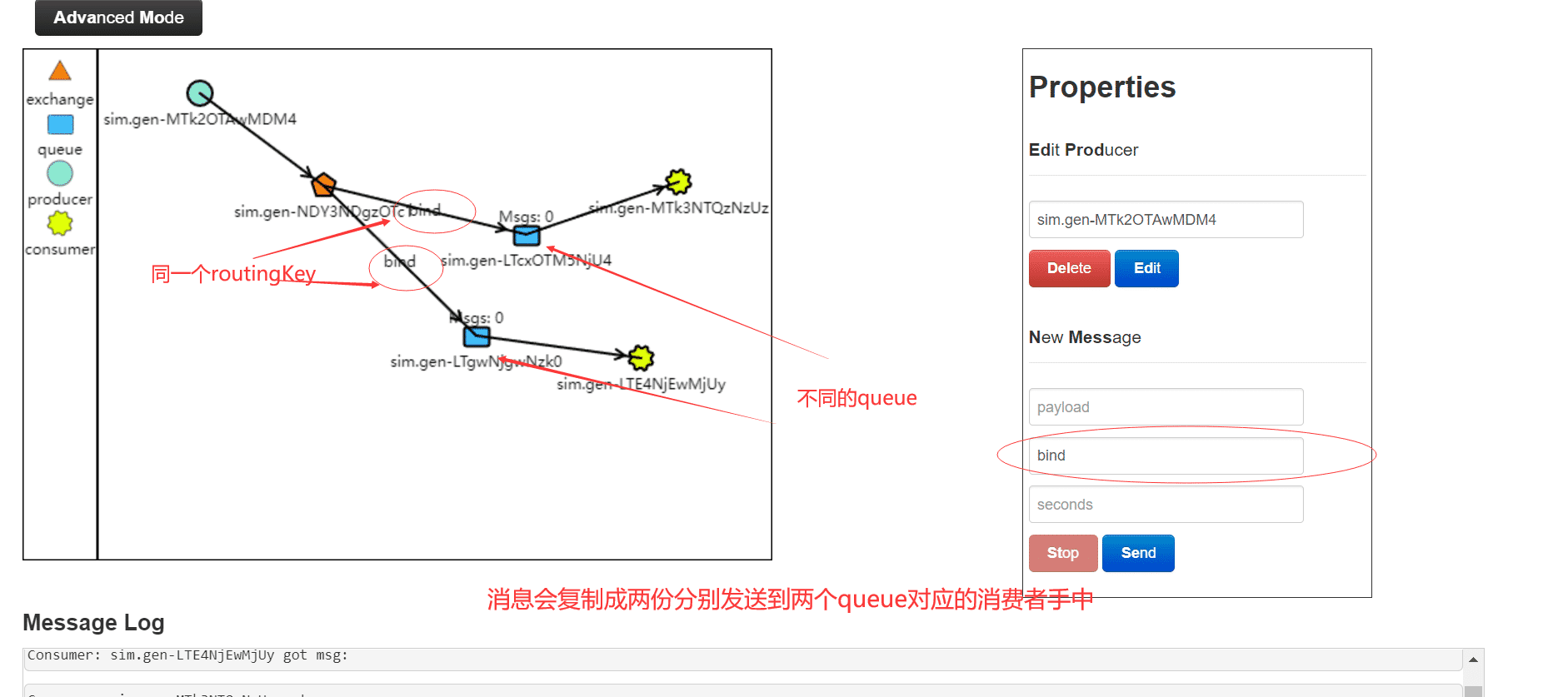
4.5 Getting the right people in the right roles in support of your goal is the key to succeeding at whatever you choose to accomplish.
4.5 Getting the right people in the right roles in support of your goal is the key to succeeding at whatever you choose to accomplish.
At the time I wasa a web designer with a focus on usability and user interfaces. I executed Json's design direction for key features of the app and collaborated with him to fill in details of the concept.
The difference between a non- lateral and a lateral join lies in whether you can look to the left hand table's row.
Kernel is already defined by Ruby so the module cannot be autoloaded. Also, that file does not define a constant path after the path name. Therefore, Zeitwerk should not process it at all.
Every element of config.autoload_paths should represent the top-level namespace (Object).
The core benefit of Marginalia is being able to decorate SQL queries with details of the context of the source of the query.
The Hori key enters a Hori lock in such a way as to affirm your suspicion that every key you’ve ever inserted into every lock throughout your entire life was a sham. A false combination — jittery, sticky, imprecise. You realize how badly cut, forged by shoddy means, all the keys you own currently are. Using this Hori key and lock combination is similar to how you might have felt the first time you ever touched a masterfully finished piece of wood — shock at that glassy smoothness you didn’t think could be brought out from the material. The key enters. Within perfectly milled chambers, the driver pins — attenuated by precisely tensioned springs — push against the key pins as the key slides forward in the keyway. The driver pins align to a dead-straight shear line and you feel the key settle with a satisfaction of a meticulously-measured thing spooning its Platonic opposite. Then you twist. The movement of the bolt away from the frame is so smooth — the door having been hung by some god of carpentry with the accuracy of a proton collision path — that you gasp, actually gasp, at the mechanism.
I love the visceral way Craig Mod describes these Hori key/lock mechanisms. Makes me want to go out and buy one.
9.2. Describe general cell signaling strategies and explore the different types of cell surface receptors and singling molecules.
9.2 Key Concepts
Chemical Signaling: * Intracellular vs. Intercellular * types of chemical signaling
Receptors: * internal vs. surface-cell * categories of surface-cell receptors
Ligand Molecules: * hydrophobic * water-soluble * nitric oxide (NO)
Work Cited
Hinic-Frlog, S., Hanley, J. and Laughton, S. (2020). Introductory Animal Physiology. Missausgua, CA: Pressbooks.
The remaining problem should be how to declare Ruby-define methods to be 'non-block taking'. Under the current language spec, absence of '& argument' may or may not mean the method would take a block.
No. 1 resource you have inherent in a professor is the latent cognitive capacity to instruct, mentor, and produce original ideas, and that we should take that resource very seriously
Family child care (FCC) refers to regulated (licensed, certified, or registered) HBCC. Family, friend, and neighbor (FFN) care refers to HBCC that is legally exempt from licensing or other regulation, whether paid or unpaid. FFN care includes care given by grandparents, other relatives, and non-relatives. Home-based child care (HBCC) providers are a heterogeneous population of providers who offer care and education to children in their own or the child’s home. (Although we use “HBCC” throughout the report, we recognize the role providers play both caring for and educating children.) Providers’ HBCC status is fluid, and individuals’ roles may change—those who care for a few children who are related to them, whether with or without pay; those who offer care as a professional occupation and a business; those who care for children over many years; and those who care for children sporadically in response to changing family needs. We assume a variety of factors influence these patterns, which may shift over time.
Essential knowledge for SECURE lab
HBCC is the most common form of nonparental child care for infants and toddlers
Notice the particular importance of HBCC for infants and toddlers (i.e., approximately birth to age three years).
HBCC includes regulated (licensed, certified, registered) family child care (FCC) and care legally exempt from regulation (license-exempt) that is provided by family, friends, or neighbors (FFN).
these are KEY TERMS for our project - learn these terms and acronyms: FCC and FFN are part of HBCC
You have to be doing 80% of the hard work, which means making the conscious effort to avoid the design flaws that will exclude people from using your product
The difference is what the server expects the client to do next.
Mabry says if you own a Hyundia or Kia, you better add extra security so you don't become the next target.
Apparently, there is an issue with key fob security on 2020 Kia Sportage and Hyundai models.
Also, Columbus Police and 10TV don't know how to spell Hyundai or use spell check.
only about 1% of carbon atoms are C-13. These are the only ones picked up by this form of NMR. If you had a single molecule of ethanol, then the chances are only about 1 in 50 of there being one C-13 atom in it, and only about 1 in 10,000 of both being C-13. But you have got to remember that you will be working with a sample containing huge numbers of molecules. The instrument can pick up the magnetic effect of the C-13 nuclei in the carbon of the CH3 group and the carbon of the CH2 group even if they are in separate molecules. There's no need for them to be in the same one.
the author believe that even though the percentage of C-13 is low, but its NMR signal can be captured.
violencia de género
«Todo acto de violencia sexista que tiene como resultado posible o real un daño físico, sexual o psíquico, incluidas las amenazas, la coerción o la privación arbitraria de libertad, ya sea que ocurra en la vida pública o en la privada».
Esa “formación” del hombre, que lo conduce a una estructura de la personalidad de tipo psicopático
No existe un perfil único de maltratador. Tampoco se trata de hombres agresivos ni de psicópatas. Nuestro estudio pone en cuestión los estereotipos relacionados hasta ahora con la conducta y los rasgos del maltratador, como puede ser el consumo de sustancias tóxicas y de alcohol, la vivencia de experiencias traumáticas en la edad infantil o los problemas psíquicos. En este último aspecto, los datos del patrón de personalidad de un grupo de maltratadores basados en el inventario clínico multiaxial Millon-II señalan a la compulsividad como rasgo más destacado de estas personas; no obstante, el percentil no supera el grado de normalidad, por lo que se descarta la posibilidad de una psicopatología.
The Query word can be interpreted as the word for which we are calculating Attention. The Key and Value word is the word to which we are paying attention ie. how relevant is that word to the Query word.
Finally
That's not how flatpack works; the executable is hidden in a container and you need to set up the whole environment to be able to call it. Delivering a well-isolated, not-to-be-run-from-outside environment is the whole point.
By connecting over an SSH tunnel, you’re limiting VNC access to machines that already have SSH access to the server.
People should also consider visiting a sleep medicine physician
lack of sleep is about lack of time.
flavored vaping products
Breathing in flavored nicotine product through a device. The device is... (need to look up)
**Need to find a good description of a vape product
Food and Drug Administration
Important term to understand - What do they do, are they part of the government, how do they regulate things?
This may be the sine qua non of rhetoric: theart of linguistically or symbolically creating salience.
Salience: importance
Weltanschauung
Weltanschauung: worldview. German.
medium thinking
Okay, so medium design/thinking is considering the backdrop against which one's subject matter is situated.
COMPLICITY
I have heard this term used a lot in the last four years. Even when I was unsure what the word precisely meant, I understood it to have negative connotations. OED defines complicity as, "the state of being involved with others in an illegal activity or wrongdoing." If Miller is using the term in this way than that's a pretty risky way to title his piece. It implies that the structure of academia is corrupted.
Matthews, D. (2021). Drowning in the literature? These smart software tools can help. Nature, 597(7874), 141–142. https://doi.org/10.1038/d41586-021-02346-4
People’s Covid Inquiry: Impact of covid on frontline staff and key workers—The BMJ. (n.d.). Retrieved September 1, 2021, from https://blogs.bmj.com/bmj/2021/08/27/peoples-covid-inquiry-impact-of-covid-on-frontline-staff-and-key-workers/?utm_campaign=shareaholic&utm_medium=twitter&utm_source=socialnetwork
So for each word, we create a Query vector, a Key vector, and a Value vector. These vectors are created by multiplying the embedding by three matrices that we trained during the training process.
I'm going to try provide an English text example. The following is based solely on my intuitive understanding of the paper 'Attention is all you need'.
This is also good
For the word q that your eyes see in the given sentence, what is the most related word k in the sentence to understand what q is about?
So basically: q = the vector representing a word K and V = your memory, thus all the words that have been generated before. Note that K and V can be the same (but don't have to). So what you do with attention is that you take your current query (word in most cases) and look in your memory for similar keys. To come up with a distribution of relevant words, the softmax function is then used.
paradigmatic
I was not sure what this term meant in this context. After looking the term up on google, the definition that seems to fit is the denotation of the relationship between a set of linguistic items that form mutually exclusive choices in particular syntactic roles.
It means that when having a type guard:TypeScript and JavaScript runtime are tied to the same behaviour.
You can't just move 'side-ways' between unrelated types; you need to move either up or down the lattice.
Isolation ensures that concurrent execution of transactions leaves the database in the same state that would have been obtained if the transactions were executed sequentially
This is why for a recent Angular+Rails project we chose to use a testing stack from the backend technology’s ecosystem for e2e testing.
So, what problem is blockchain solving for identity if PII is not being stored on the ledger? The short answer is that blockchain provides a transparent, immutable, reliable and auditable way to address the seamless and secure exchange of cryptographic keys. To better understand this position, let us explore some foundational concepts.
What problem is blockchain solving in the SSI stack?
It is an immutable (often permissionless) and auditable way to address the seamless and secure exchange of cryptographic keys.
(load functions call handle directly, there's no intermediate network requests.)
When fetch runs on the server, the resulting response will be serialized and inlined into the rendered HTML. This allows the subsequent client-side load to access identical data immediately without an additional network request.
'set-cookie': response.headers.get('set-cookie')
plus authorization if it's not explicitly provided, to a fetch request that happens inside load to an internal endpoint
Moreover, “[r]elations of power are not in a position of exteriority with respect to other types of relationships (economic processes, knowledge relationships, sexual relations), but are immanent in the latter.” Such claims played some role in the rise of a mode of analysis that vastly expands the range of what can be treated as political.
power is everywhere; in every relationship; this is why the range of what is "political" is actually quite vast
responsibly deploy AI systems
the concentration is calculated based on the fraction of droplets that is empty (that is, the fraction that does not contain any target DNA).
first sighting: this file referenced by https://hyp.is/ZD-z8px8Eeue0ws8rEMsrw/gist.github.com/cowboyd/1642793
often in error
Personal and professional development will follow andultimately these very same characteristics and approaches will naturally transfer intopractice and in direct contact with young people
what we learn when becoming youth workers is transferable to our practice, reflective of the necessity of openness and transparency. when we learn the value of these skills, we can demonstrate their value to the young people, and continue the learning journey together
the better a student/youth worker knows himself/herself the more likely he/shewill be able to help others know themselves;
the quality of training and the development of skills will impact on the growth of the young person
the Activity component is the heart of TRB
ReconfigBehSci. (2021, February 8). RT @lakens: @BrianNosek @SLLancaster @siminevazire @hardsci Very cool—And it already has a list of glossaries to build on https://t.co/c9… [Tweet]. @SciBeh. https://twitter.com/SciBeh/status/1359042653539741696
exceptions are not exceptional, they represent expectable problems
for term in vt100 linux screen xterm { echo "$term:" infocmp -L1 $term|egrep 'key_(left|right|up|down|home|end)' }
Coronavirus doctor’s diary: Karen caught Covid - and took it home. (2021, January 16). BBC News. https://www.bbc.com/news/stories-55682405
That's the whole point of an abstraction layer—to isolate your business logic from a subsystem's mechanics
So the hard and unsolvable problem becomes: how up-to-date do you really need to be?
After considering the value we place, and the tradeoffs we make, when it comes to knowing anything of significance, I think it becomes much easier to understand why cache invalidation is one of the hard problems in computer science
the crux of the problem is: trade-offs
The key phrase here is “children of a grid container.” The specification defines the creation of a grid on the parent element, which child items can be positioned into. It doesn’t define any styling of that grid, not even going as far as to implement something like the column-rule property we have in Multi-column Layout. We style the child items, and not the grid itself, which leaves us needing to have an element of some sort to apply that style to.
The Black Panther Party chose the name because the panther is known to be an animal that never makes an unprovoked attack, but will defend itself vehemently when attacked, and this was symbolic of what the Black Panther Party for Self-Defense stood for
black unity and black autonomy were at the core of its platform and program