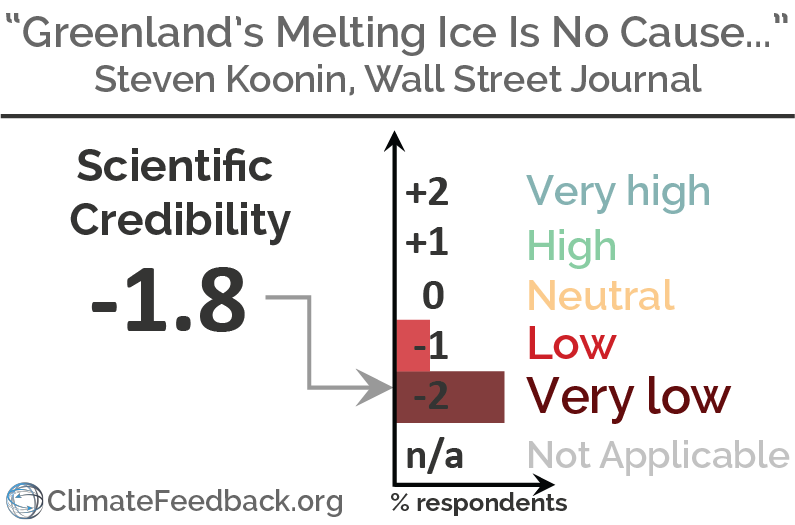
The Culture Industry: Mass Deception in Dialectic of Enlightenment
The culture industry is any industry that is producing cultural products: news, beauty, music, fashion industry has one goal: generate profit. They will produce things that are produced like a factory. They are intended to produce consumerism. In the way that sex sells, rebellion also sells. The industries that are making our culture are feeding us our news so are corporaterized.
Adorno and Horkheimer would not be suprised about YouTube. That cultural adversary may be dialectical.
Academia. You know more about less and less.
Backdrop context: Shaky ground of liberal democracy in the beginnings of WW2,rise of social movements, rise of nationalism and facism.
Englightment: Reason & Individual liberty
Bacon: a larger system that synthesized knowledge and power as one; a flipping of nature over man and man over nature; but A/H thought that this played out in a human global scale.
If Enlightenment was supposed to create logic and reason why did we experience WW2, for A/H if we're to take Bacon seriously we have to consider DOMINATION in newer notions of freedom.
Regression: Enlightenment as Myth. Englightenment becomes totalitarian it ABSTRACTS. Ex. Hitler youth, a difference among others yet they become homogenous sameness among each other.
The result of the sacrifice continues that is far more reaching that MArx's alienation. --> UNFETTERED ACCEPTANCE
Adorno/H say that positivism: 1) a system of philiospgy were every assertion can be proved 2) as ideoogy where eveyrthing is true by default and questioning it goes against objective foundations.
Kant saw a short-sighted view of self-reason
IDEOLOGY of defintiion #2 the process of Englightenment is brought into analysis of the Culture Industry.
Context: AMerica is becoming global powerhouse, Soviet underwent their own Industrial Revolution, change was everywhere and revolutionary change with one large outlier thus the immediat question. Despite a global population of workers revolitng around the globe then why didnt the United States or Western Countries embrace similar post-capitalist systems seen across teh globe? And how is Soviet existing as a post-capitalist system alongside the capitalist system?
Art is being systematized, newer technology is being synthesized into one and the same narrative. The same repackaged story; subject and authority. This mimics the governance of a few over many.
A/H utilize Kant's idea of schemtaism (being how the midn communicates with objects and other structures aorund us, how to reason and cogantate; synthesize and bring Froyd into the mix, how we suppress ourselves and our desires to how we fit into society. We cognitively pick up how the world is presented to us. Viewership creates the bounds within which we can do art. A psychological realism that is difficult to break for a person who works a 9-5pm; to break it in a capitalist system is used to labor and build wealth. Art becomes the same even when it tries to stand out. There is a unifornm aethetic if you wnat to be different, the sameness and constant
Art is now abstracted a fulfilmmnet of mere numbers rather than aesthetic work and utility. Regarding art in newer creation, A/H bring up autombiles as an example, a film must have a romatic sequence that the industry now demands. This is part of Mechanical reproduction. Art will become tailored to your class relation as well. But it's not only class and poleconomy but it's not just corporate art is entirely based oof profit but rather there is a cyclcial ideology that reinforces this ideology. see
The focus isn't on marvel movies (for their thrist for profit) or to tell consumers to not consume this art but its the industry itself that reproduces the
"Thirst" is not conscious it is a result of the structure that is capitalism the culture industry modling of our desires in the first place.
It's not good enough to tell individuals to not consume said tailored art. Example anti-semitism is a result of essentialist notions of race. Largest incubators of anti-semitism stem from the bourigeoise themselves but a ruling class of people attempting to hide a ruling class domination. Here the bouregoise know the struggles of individuals and pins this to Jewish individuals.
Thus its not really just pushing Jewish people out of certain borders this marks the downfall of bouregoise property.
Look up: > Cultural education became....
The whole world is made to pass through the filter of the culture industry...
Culture is a paradoxical commodity. It is so completely subject to the law of exchange that it is no longer exchanged; it is so blindly equated with use that it can no longer be used. For this reason it merges with the advertisement. The more meaningless the latter appears under monopoly, the more omnipotent culture becomes. (pg 131).
Unending sameness also governs the relationship to the past. What is new in the phase of mass culture compared to that of late liberalism is the exclusion of the new.